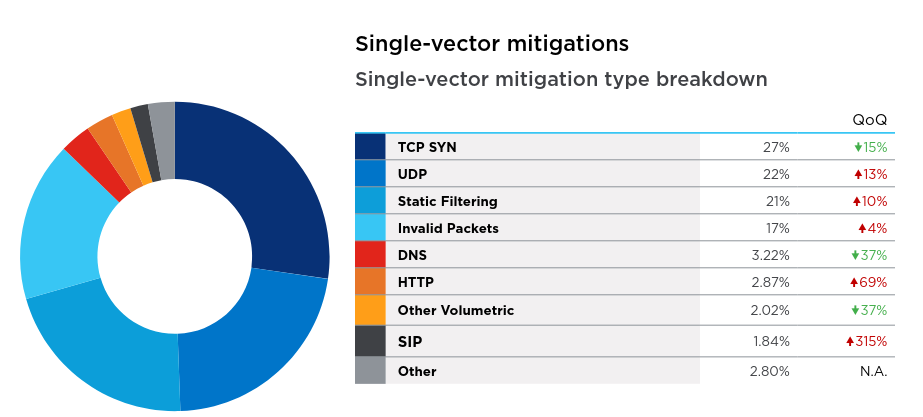
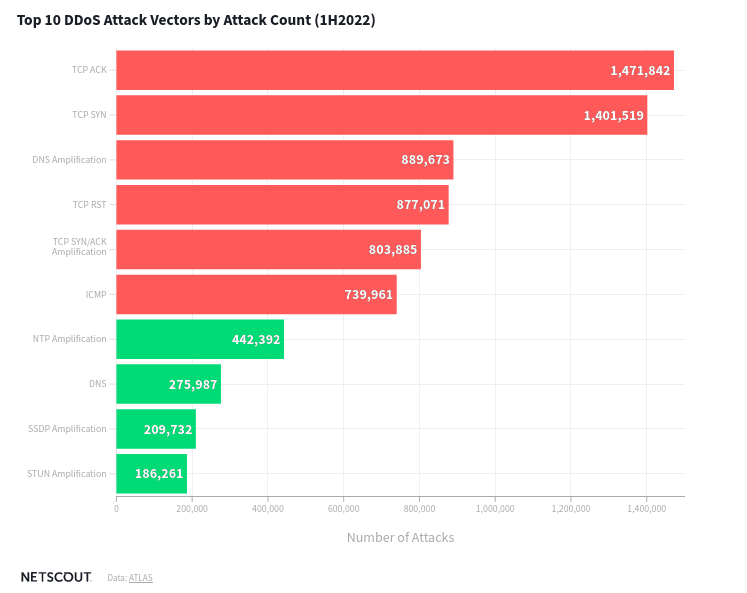
zeroBS collects informations and status reports on the subject of infrastructure security vs DDoS-Threats. In this article we provide an condensed overview of trends and developments.
additionally we track DDoS-ThreatLevels in different flavors:
2022
Summary
-
general trend: frequency goes down, quality goes up
-
OSINT is the big newcomer in 2022, giving attackers the ability to find and attack weak spots in targets networks/application (hello
kittyKillNet/Noname et al -
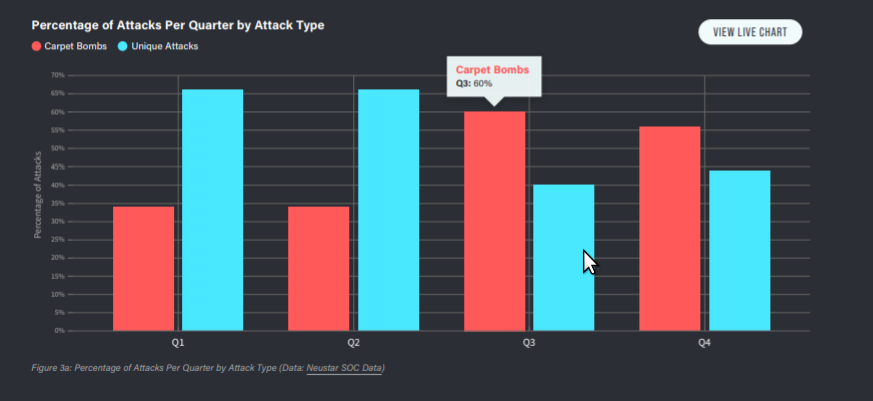
once-sophisticated Attacks hit the Mainstream (TCP-DirectPath, Carpetbombing, DNS-DDoS): Neustar & Netscout are seeing CarpetBombing arriving in the mainstream, where in Q3/Q4 50% of attacks against networks are leveraging CarpetBombing-Attacks (Neustar, Netscout)
-
Server-based Botnets are back again and have a stable 5-10k - size
-
TCP DirectPath has been seen as a dominant and most successful attackvector in more-than-average-attacks
-
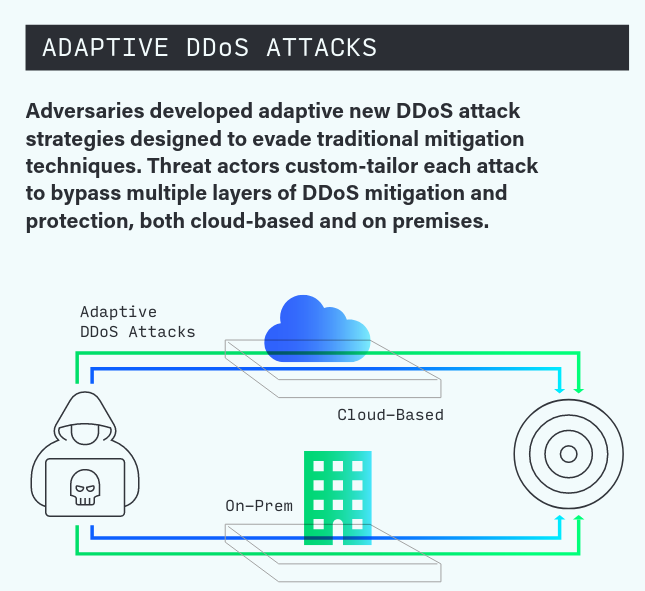
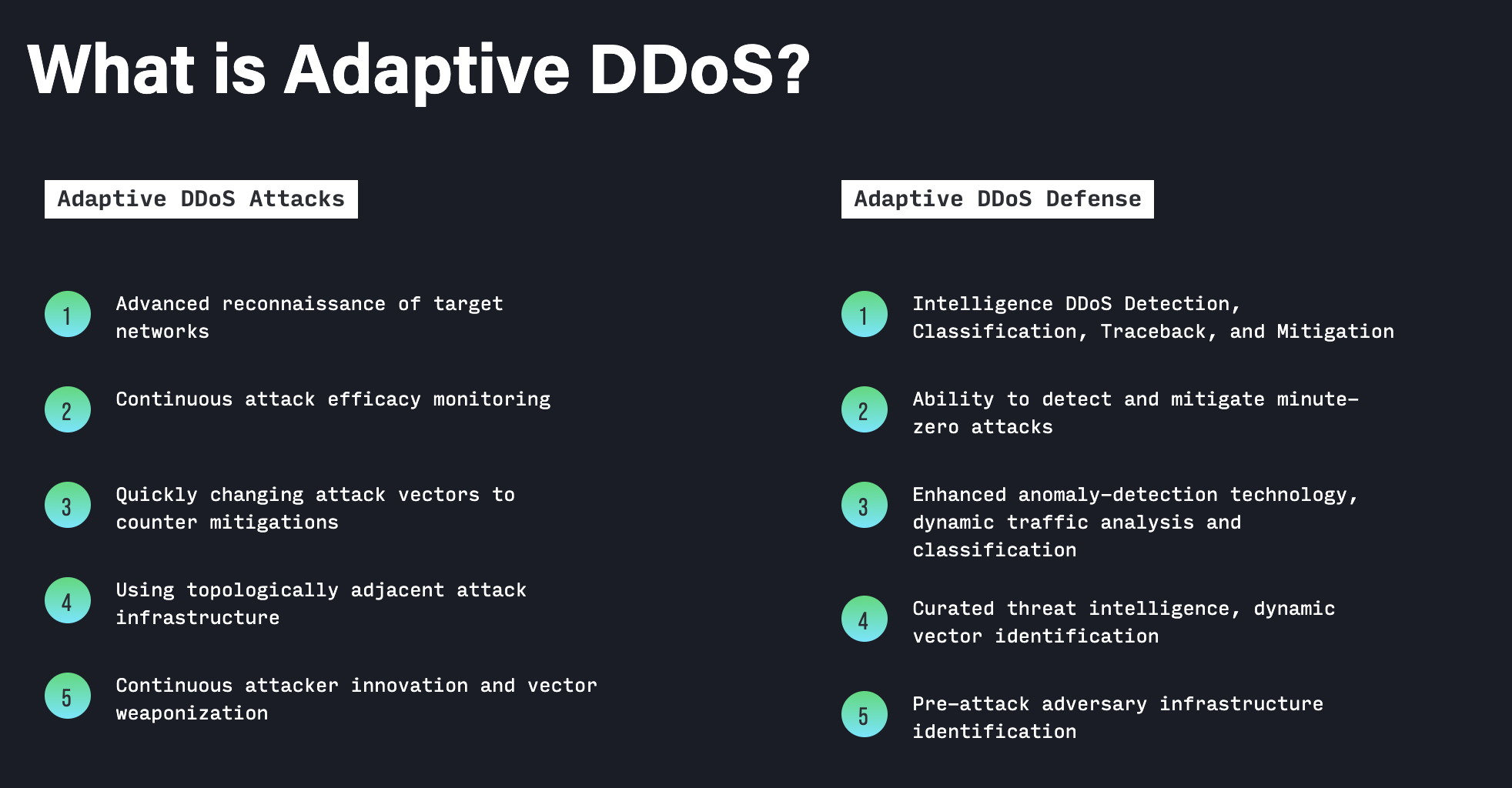
DDoS - Threat actors custom-tailor each attack ("surgical methods", Lumen) to bypass multiple layers of DDoS mitigation and protection, both cloud-based and on premises.
-
HitAnd Run-Attacks (Short-term, Testing defense only)
-
DDoS as third ransom-vector by Ransomware-Gangs
-
strong hacktivism-activities due to geopolitical events (Ukraine-War, Iran uprising etc) fuel the DDoS-Threat-Landscape
References & Reports
- Cloudflare DDoS attack trends for 2022 Q4
- Cloudflare DDoS attack trends for 2022 Q3
- Cloudflare Radar DDoS attack trends for 2022 Q2
-
Akamai: Cyberterrorists Target Record Number of Victims with DDoS Attacks in Q2
- Akamai: The Relentless Evolution of DDoS Attacks
- How Google Cloud blocked largest Layer 7 DDoS attack yet, 46 million rps | Google Cloud Blog
TA DDoS
- NoName057
- XAKNet (HackNet)
- Cyber Army of Russia
- Deadnet
- KillNet
2021
TL;DR: attackers get more advanced, but experienced protectors know how to cope with the attacks
- a more detailed timeline of current events are tracked in our DDoS-Incidents Logbook 2021
- a german version as PDF-Download is available as well (TLP:GREEN)
current Trends and what we expect in the near future:
The DDoS-Threat-Situation has not really improved in recent years, and DDoS-based extortion still seems lucrative enough. Furthermore, we see a Renaissance of DDoS-Attacks in 2021 for many actors, either extortion, hacktivism or your average "sportsman".
-
since 2020, a DDoS ransomware gang with changing names has been very active (tracked by us here ), attacking unprotected companies with highly targeted attacks. Trademark of this gang:
- customized and targeted attacks after reconnaissance with high penetrating power.
- APT-mocking with constantly new names (Fancy Bear, Armada Collective, Lazarus Group, or REvil lately)
- attacks on multiple targets of one industry (so far: banks, travel, ISP, telcos, VOIP providers, gaming industry, email providers)
- global scale attacks
-
DDoS campaigns in 2021 have become more targeted, multi-vector and persistent (Neustar, Netscout)
-
Ransom DDoS (RDDoS) campaigns got a substantial boost (ENISA, Cloudflare, Netscout)
-
cybercrime-as-a-service (aka: Booter/Stresser-services) works as an amplifier of web-based and volumetric DDoS attacks
technical trends
-
TCP-based attack vectors are coming into focus due to
new researchpapers (link to paper directly ), which suggest a huge potential in TCP volumetric attacks -
TCP-Amplification and Reflection will become a major threat in the coming years, especially with amplification-rates > 1000. we expect advanced adversaries using this vector more and more successfully, and already have seen well done TCP-attacks
-
DDoS is moving towards mobile networks and IoT (ENISA), supporting localised DDoS where an attacker interferes with the connectivity of a specific area threating services like onlinebanking and any service with a large customerbase using mobile devices/connection
-
Recon, target-analysis and mitigation-monitoring is quite common with Ransom DDoS and advanced attackers (multiple sources and DFIR)
-
Botnet-Size of 50.000 Bots and more is the new norm for IoT-Botnets
-
1TB/s volumetric attacks defines the new upper level and has been seen by many providers (Netscout, Cloudlfare, Google, Neustar)
-
streetprices for DDoS-Attacks kept stable in the last 2 years
-
DTLS and GRE are emerging vectors
-
60% of all DDoS-Attacks are application-based and non-volumetric
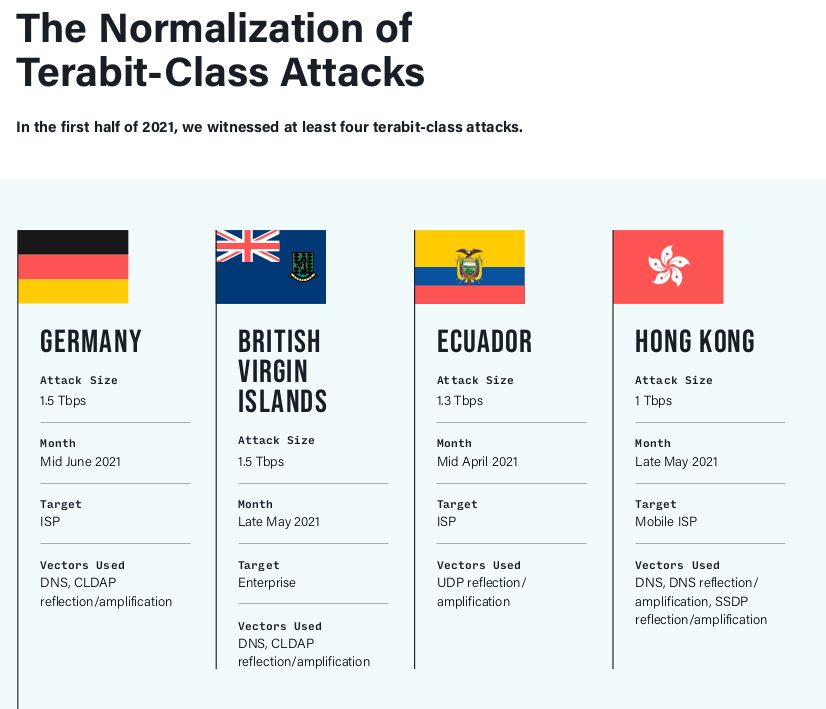
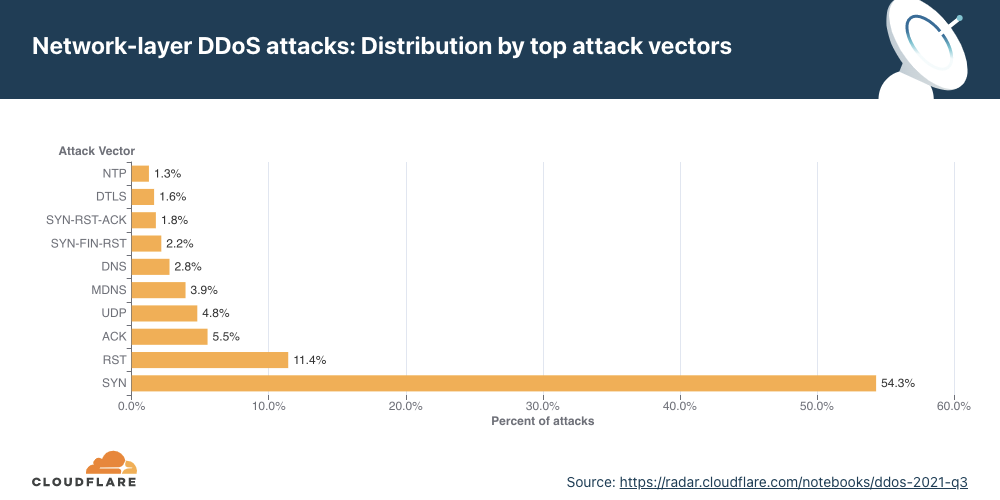
things that wouldnt surprise us in 2022
- IPv6 - attacks
- new vectors, maybe interesting misusage of QUIC
- attacks with unexpected and unpredictable side effects or cascade effects, e.g. a powergrid going down due to attacks, which is kind of overdue
Reports and Analysis
disclaimer: we refer to reports and analysis with benefit for technical personel/blueteams
-
The current ENISA-REPORT covers DDoS in detail in section 8. THREATS AGAINST AVAILABILITY AND INTEGRITY. Organizations in Europe should be aware that "... the threat potential of DDoS attacks is higher than its current impact in the EU ...", which may well lead to an increase in attacks in the EU area.
-
NETSCOUTs 2021 Threat Intelligence Report provides a very detailed development, analysis and overview of the DDoS threat situation in 2021, compared to previous years. One of the keyfindings (besides whatr has been covered above): TB-attacks starts to become "the norm"
-
Cloudflares report on a 17.2Mio RPS DDoS attack offers an interesting insight into a large Mirai-Botnet.
-
DDoS Attack Trends for Q3 2021 by Cloudflare gives an excellent overview about the global activities and trends.
-
Google: Exponential growth in DDoS attack volumes from 2020 ist a very interesting read about large-scale DDoS-Attacks, trends and attacker-capabilities
2018
Intro
zeroBS sammelt die wichtigsten Informationen und Status-Reports (Akamai, Neustar, Verisign, Qihoo 360) zum Thema Infrastruktursicherheit / Lage auf dem DDoS-Sektor, und gibt in diesem Artikel eine Übersicht über die wichtigsten Aussagen, Trends und Inhalte.
Statistics from Arbor
57% of DDoS-Attacks saturated the internet/network-capacity of attacked victims
658 Gbps
maximal size of volumetric attack
Attack-Visibility:
658 % of attacked companies had visibility on Volumetric Attacks
658 % of attacked companies had visibility on Layer-7-Attacks
Statistics from Akamai
TCP vs UDP in volumentric attacks
Volume:
658 GBit
Volumen max Arbor (1)Attack-Visibility:
658 % vs Volumetric Attacks
658 % vs Layer7-Attacks
Statistics from Neustar
avg volumetric Attack-Size, by percent
658 Gbps
maximal size of volumetric attack
Attack-Visibility:
658 % of attacked companies had visibility on Volumetric Attacks
658 % of attacked companies had visibility on Layer-7-Attacks
Statistics from Verisign
Avg Attack Peak Sizes
0 Gbps Avg Peak-Size
0 % > 1 GBps
Multi-Vectors:
Attack-Types:
Multi-Vectors:
https://ddosmon.net/insight/
https://blogs.akamai.com/2018/06/summer-soti---ddos-by-the-numbers.html
https://securityledger.com/2018/06/akamai-report-finds-ddos-attacks-more-sophisticated-adaptive/
https://www.corero.com/blog/890-the-current-state-of-ddos-attacks-are-they-getting-smarter.html
https://www.verisign.com/en_GB/security-services/ddos-protection/ddos-report/index.xhtml
https://www.security.neustar/blog/Neustar-DDoS-and-Cyber-Security-Report-Wins-InfoSec-Award-for-Research-Report
visibility / tools
https://blog.radware.com/security/2016/03/how-to-prepare-for-a-ddos-attack/
Referenzen
- Netscout/Arbor: INSIGHT INTO THE Global Threat Landscape
NETSCOUT Arbor's 13th Annual Worldwide Infrastructure Security Report - Akamai: SUMMER SOTI - DDOS BY THE NUMBERS
- Verisign: Distributed Denial of Service Trends Report
- Neustar: Global DDoS Attacks & Cyber Security Insights Report
Fragen? Kontakt: info@zero.bs