The Russia-Ukraine war is flanked in cyberspace by a number of actions and attacks, some of which can be attributed to state actors, others to hacktivists.
DDoS is the easiest cyber weapon to use and is guaranteed to be in the arsenal of any nation that is serious about the issue, so we were not surprised to see such attacks.
We would like to document some DDoS attacks, their effects that were observed in the context of the Russia-Ukraine war, and also the development of actors.
The Evolution of KillNet
tl;dr: From May to July 2022 DDoS-actor KillNet developed to a serious threat even for protected services, because they leverage TTPs that allows for targeted and successfull DDoS-attacks. We expect other hacktivism-groups to learn from that, so that there will be most probably a raise of DDoS-Attacks all around the world. We already see this
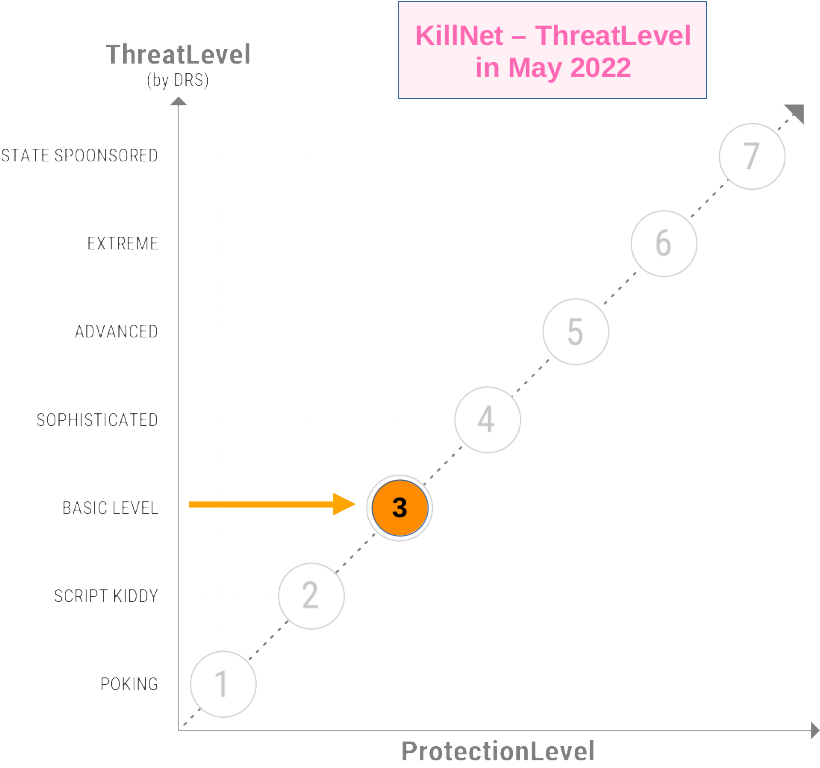
Since around Easter/April 2022 we have seen the KillNet - Group emerging, performing DDoS-Attacks for Mother Russia.
At the beginning, these attacks were still somewhat uncoordinated, but they already hit targets in various countries such as Germany (authorities, airports, banks, police), the USA (airports), Ukraine (banks, authorities, utilities), as individual media reported. The attacks were initially at DRS Level 2-3 (basic), i.e. primarily simple botnet attacks, TCP on OpenPorts, "mostly harmless". There are other analysts who estimated the ThreatLevel as Moderate/Low back at this time as well.
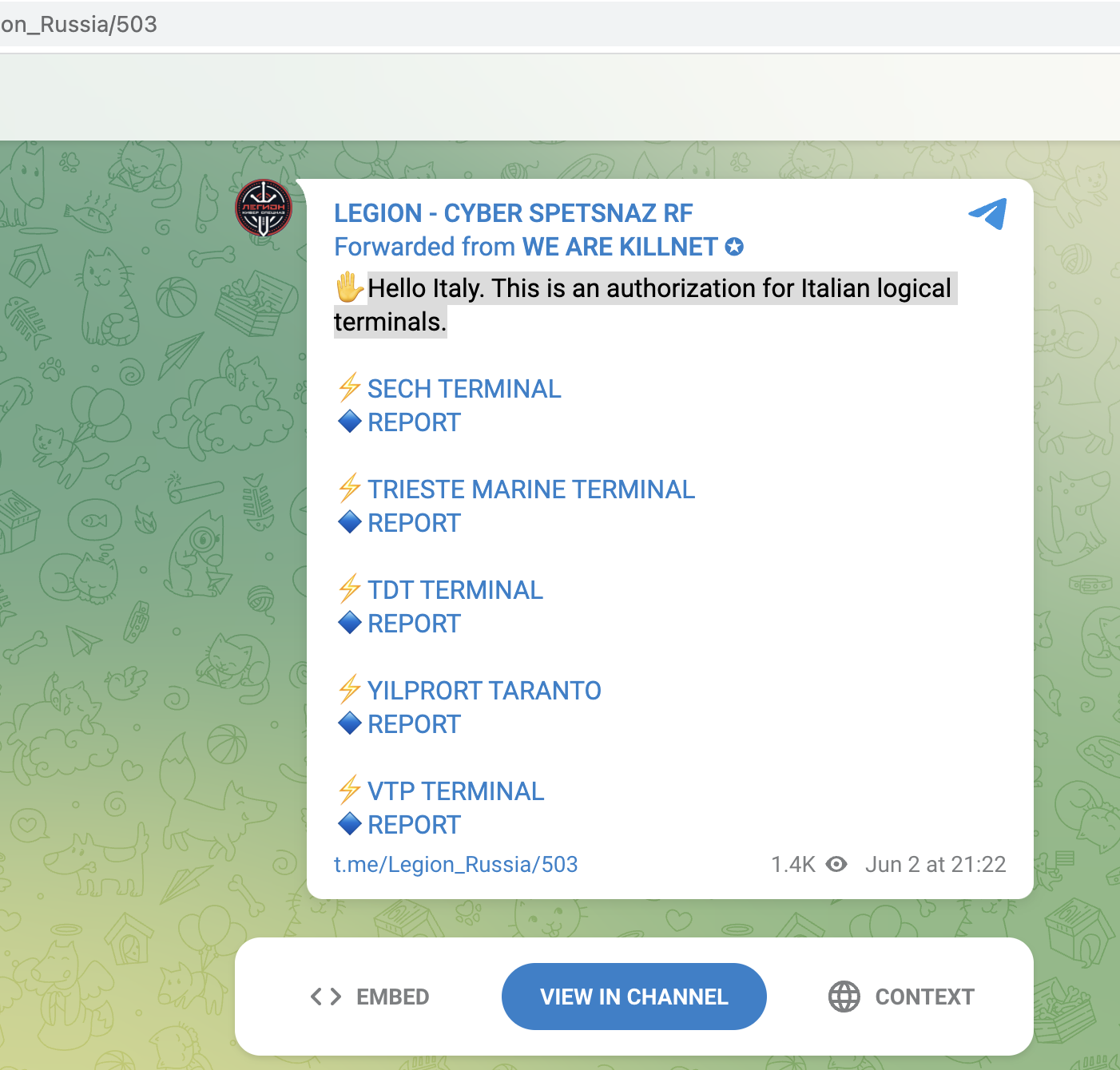
Then, in late May, more coordinated attacks on Italian infrastructure began, and one could slowly see the transition from more trolling attacks to target services that really hurt.
The first real damage was caused by the attacks on Italian seaports that took place from the beginning of June. Real Damage, because the attackers had learned in the meantime to find out the important targets and services, which, when blocked, can cause severe disruption.
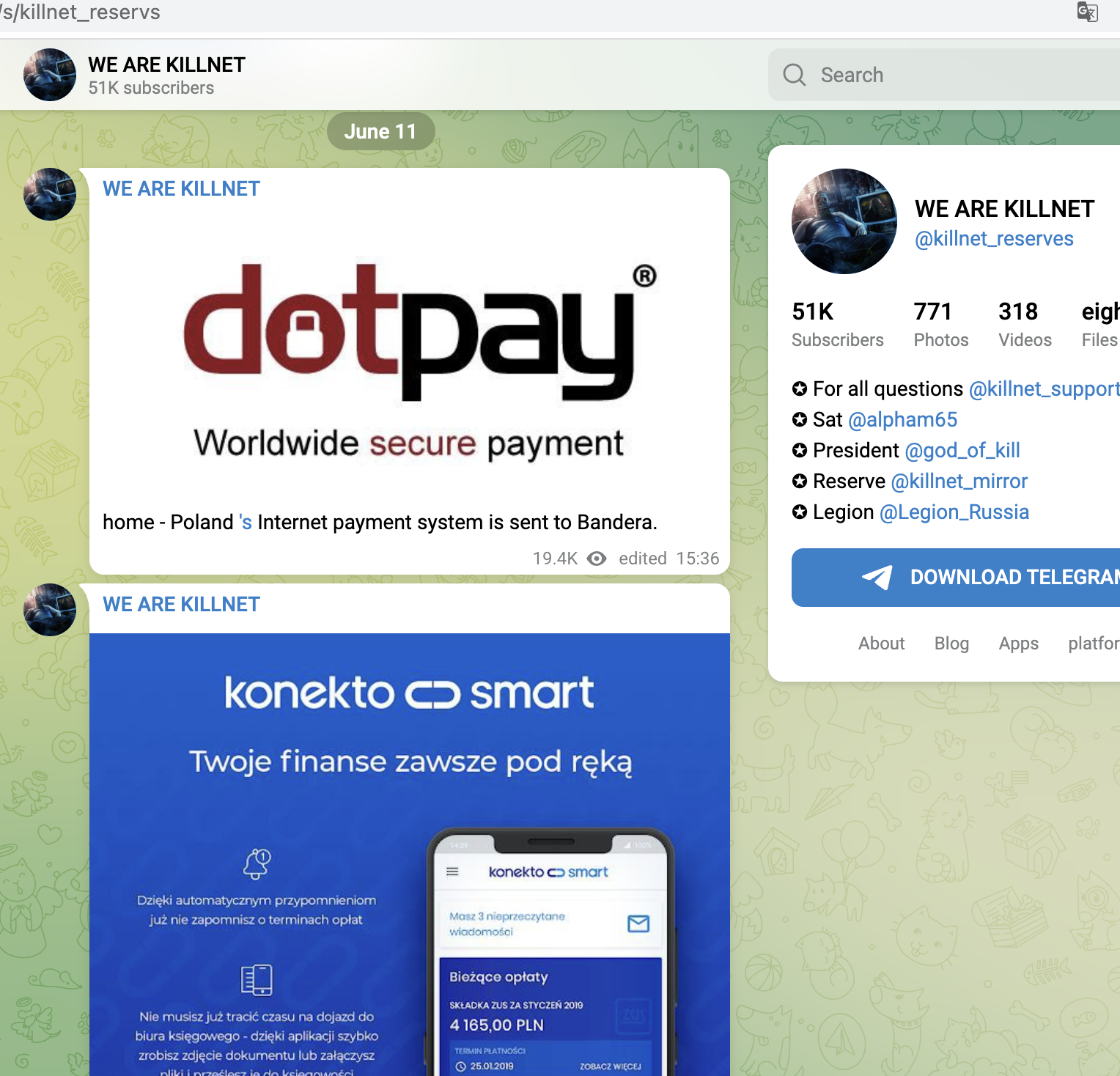
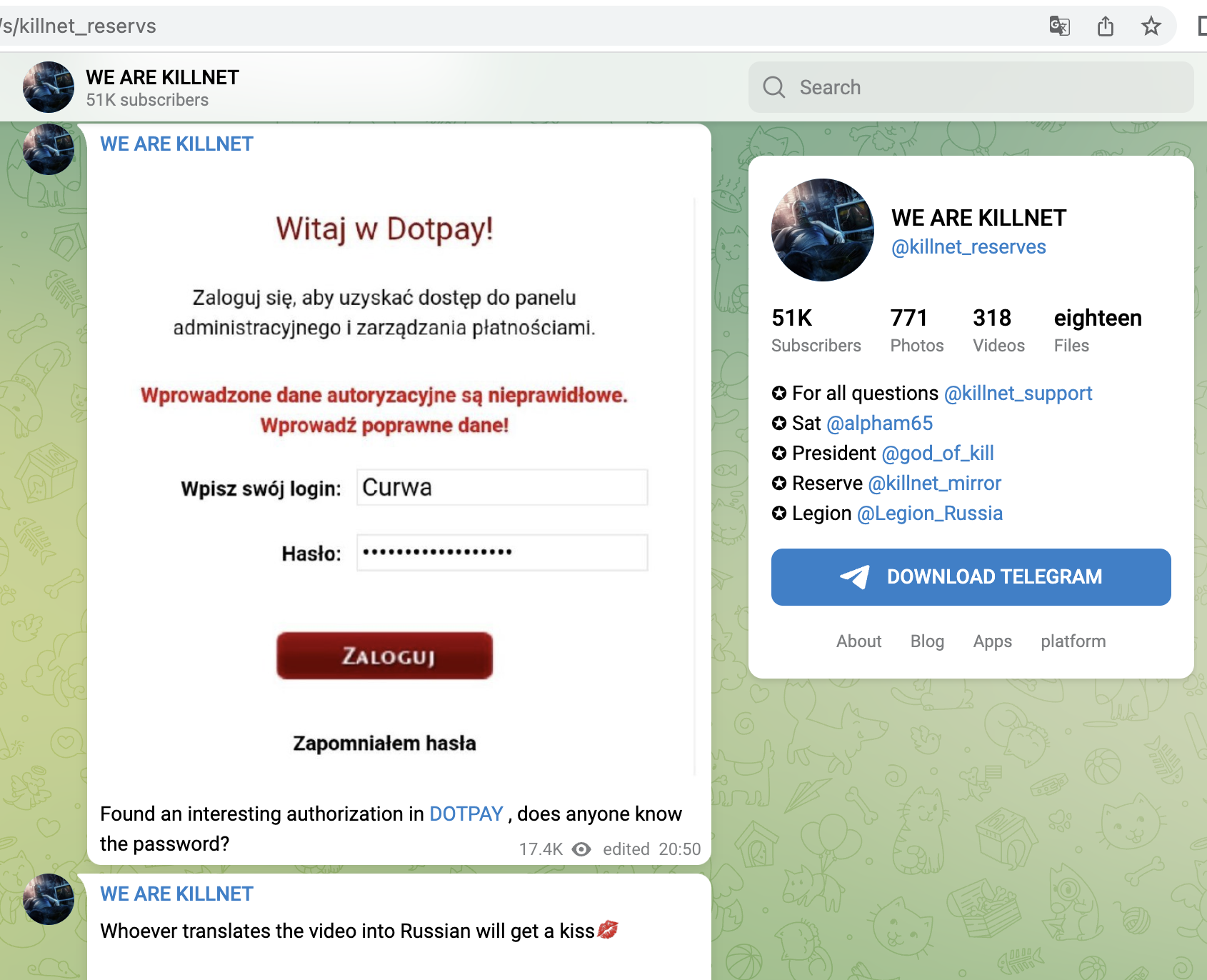
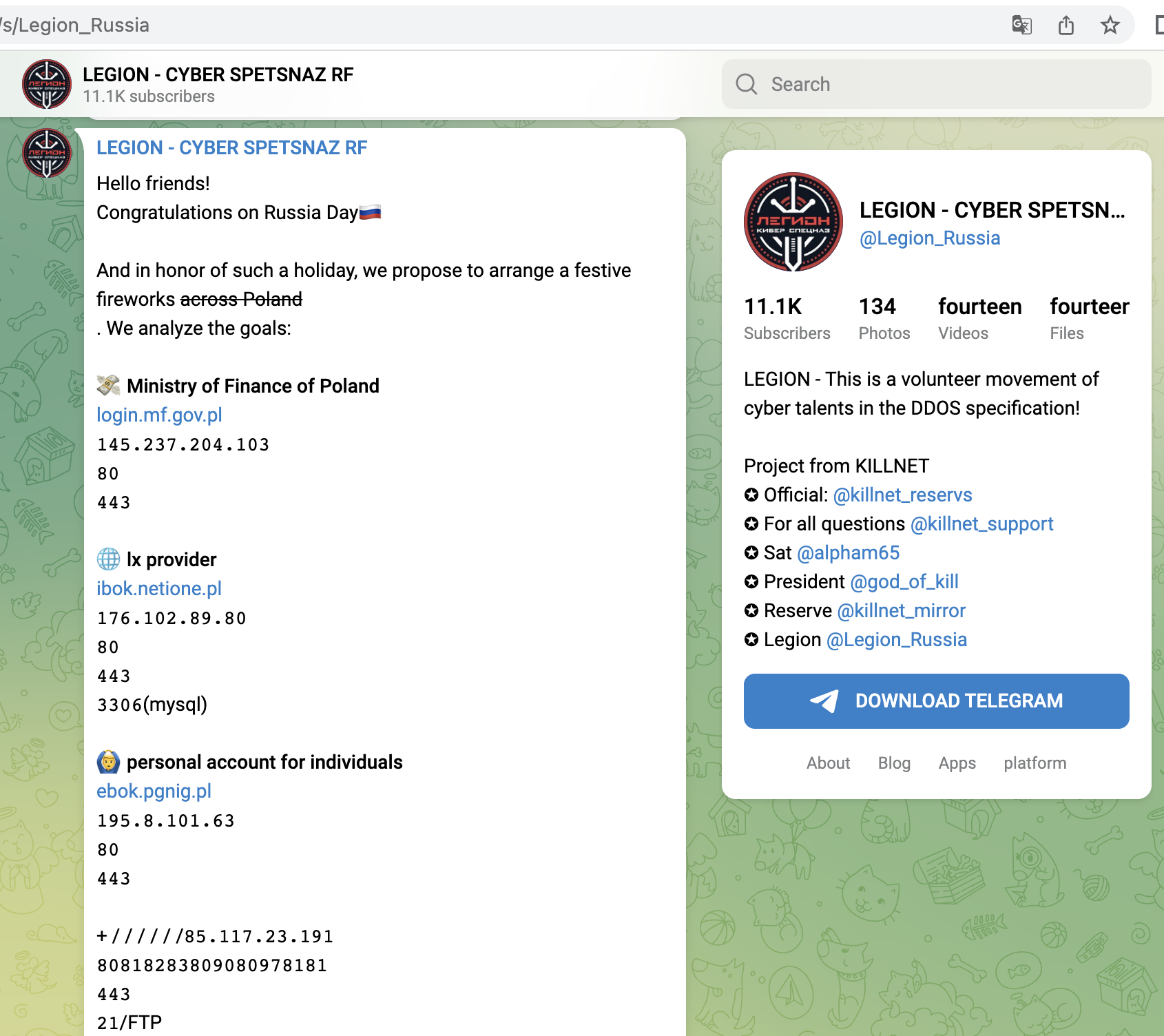
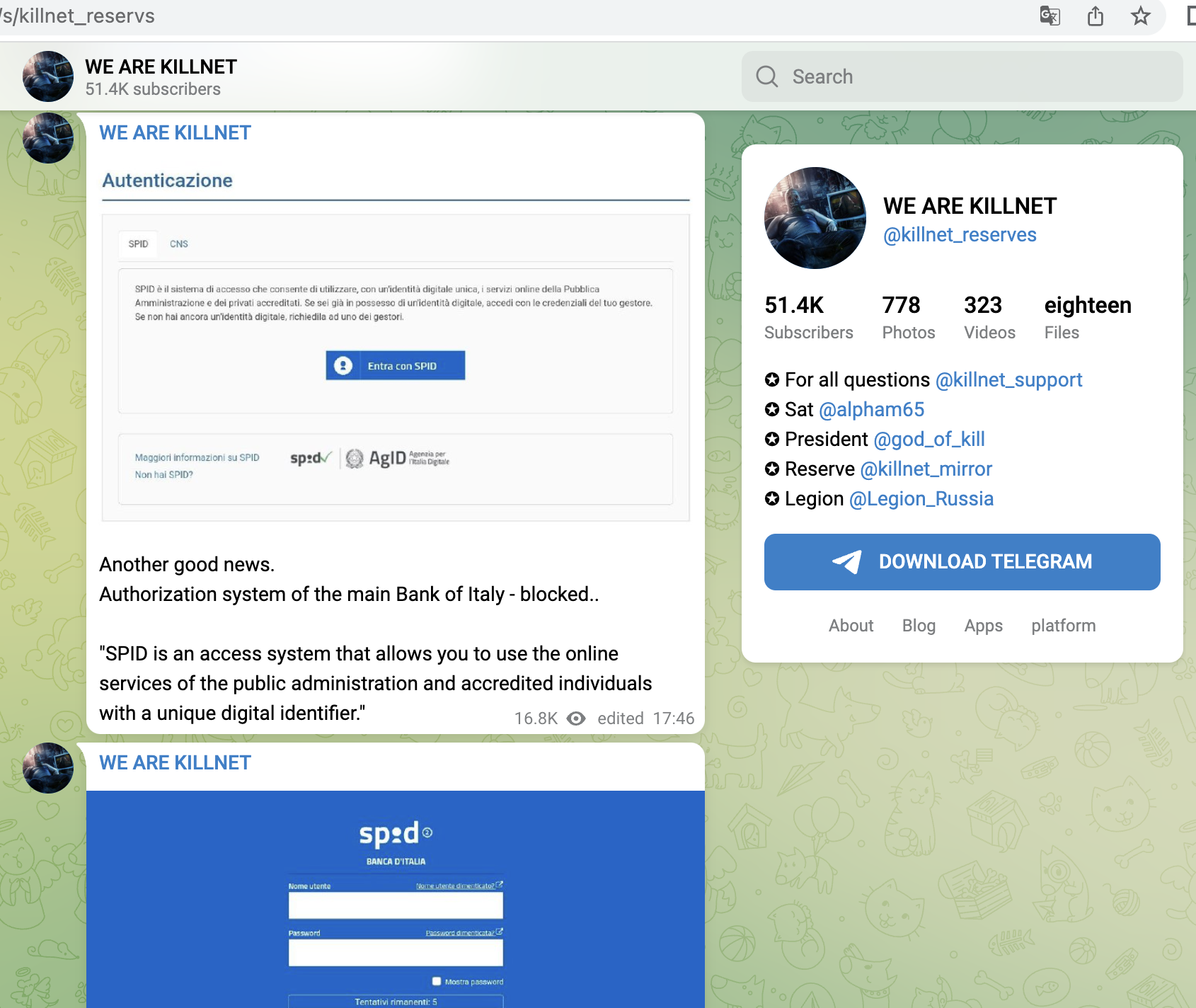
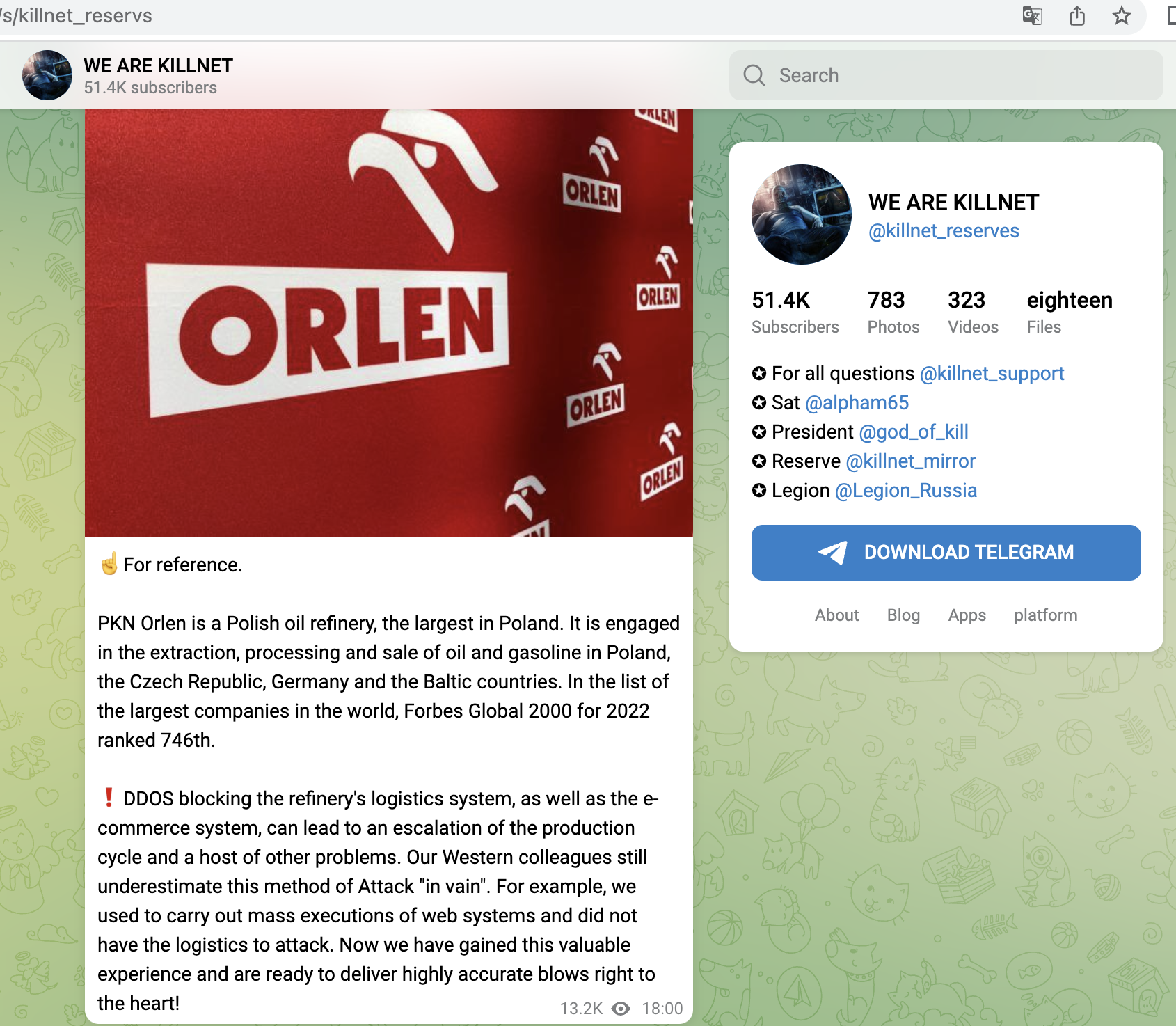
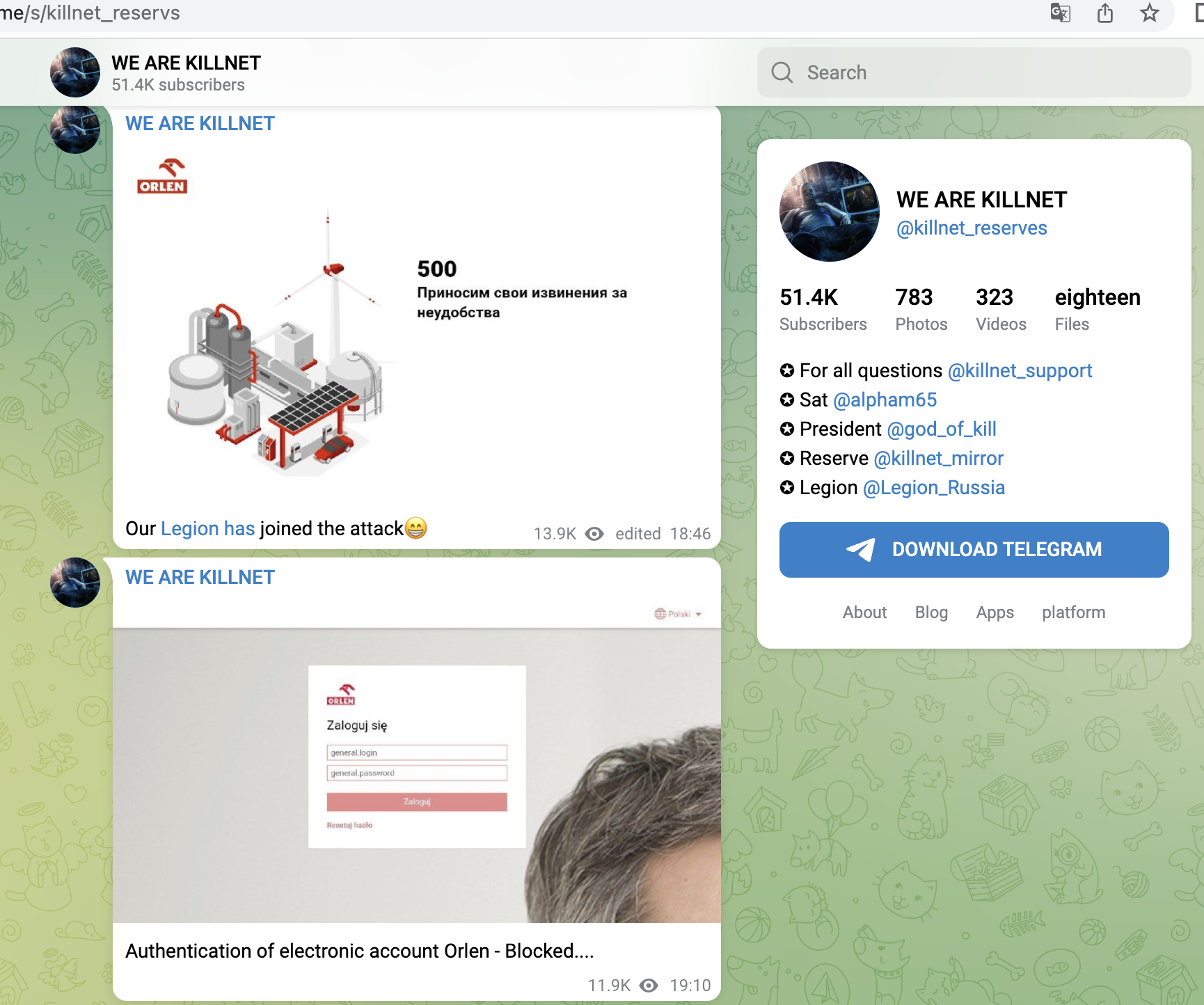
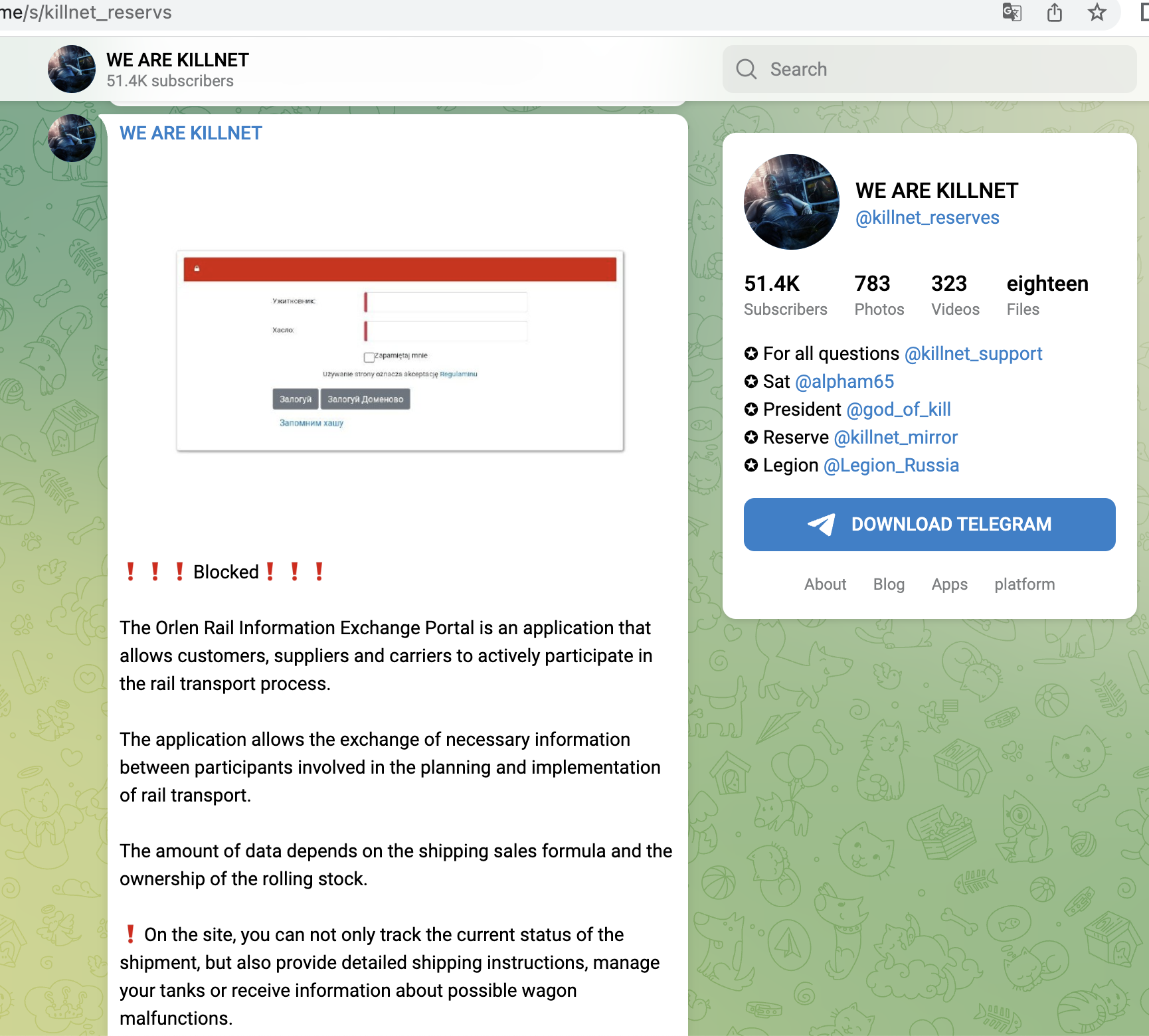
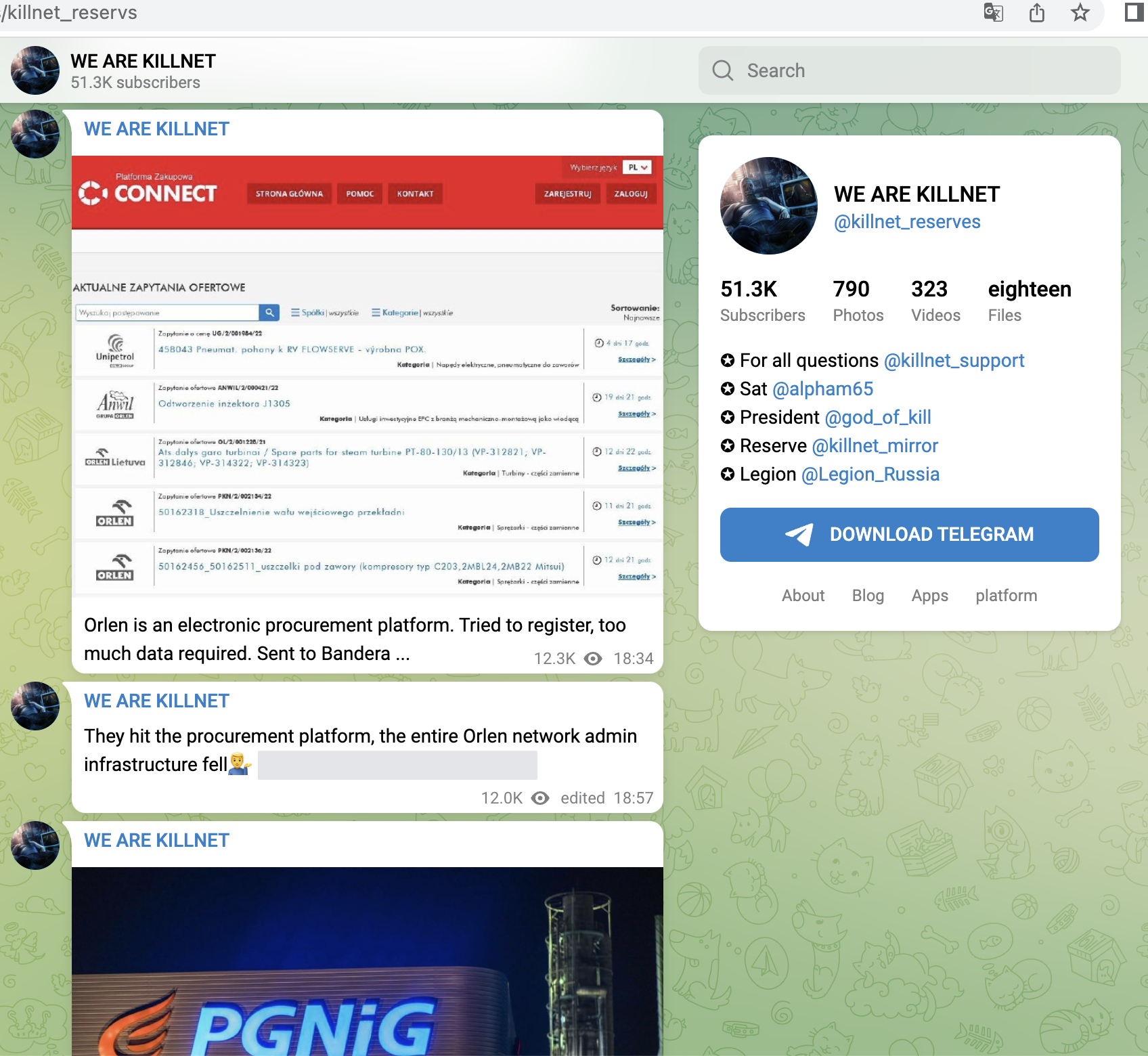
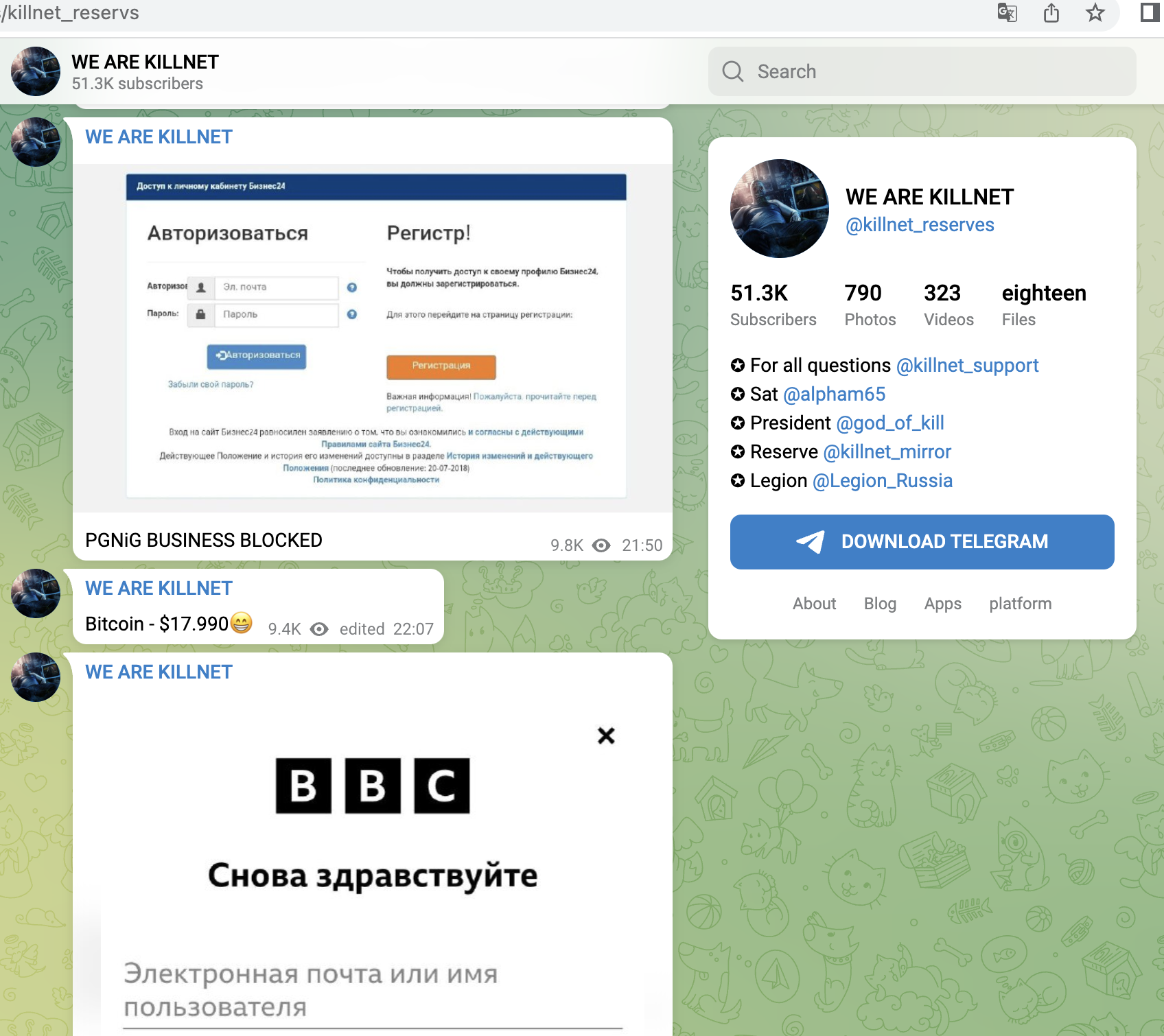
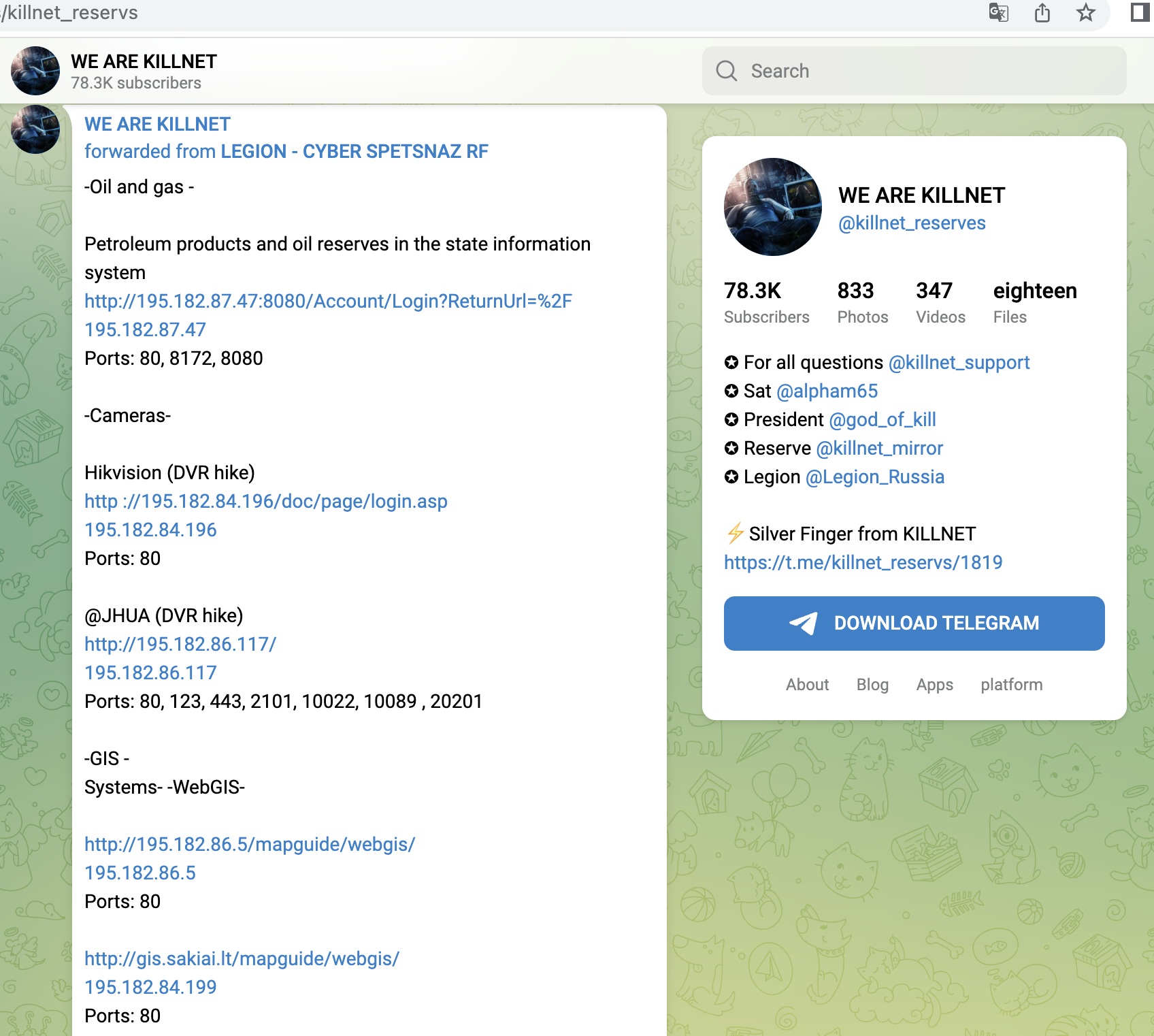
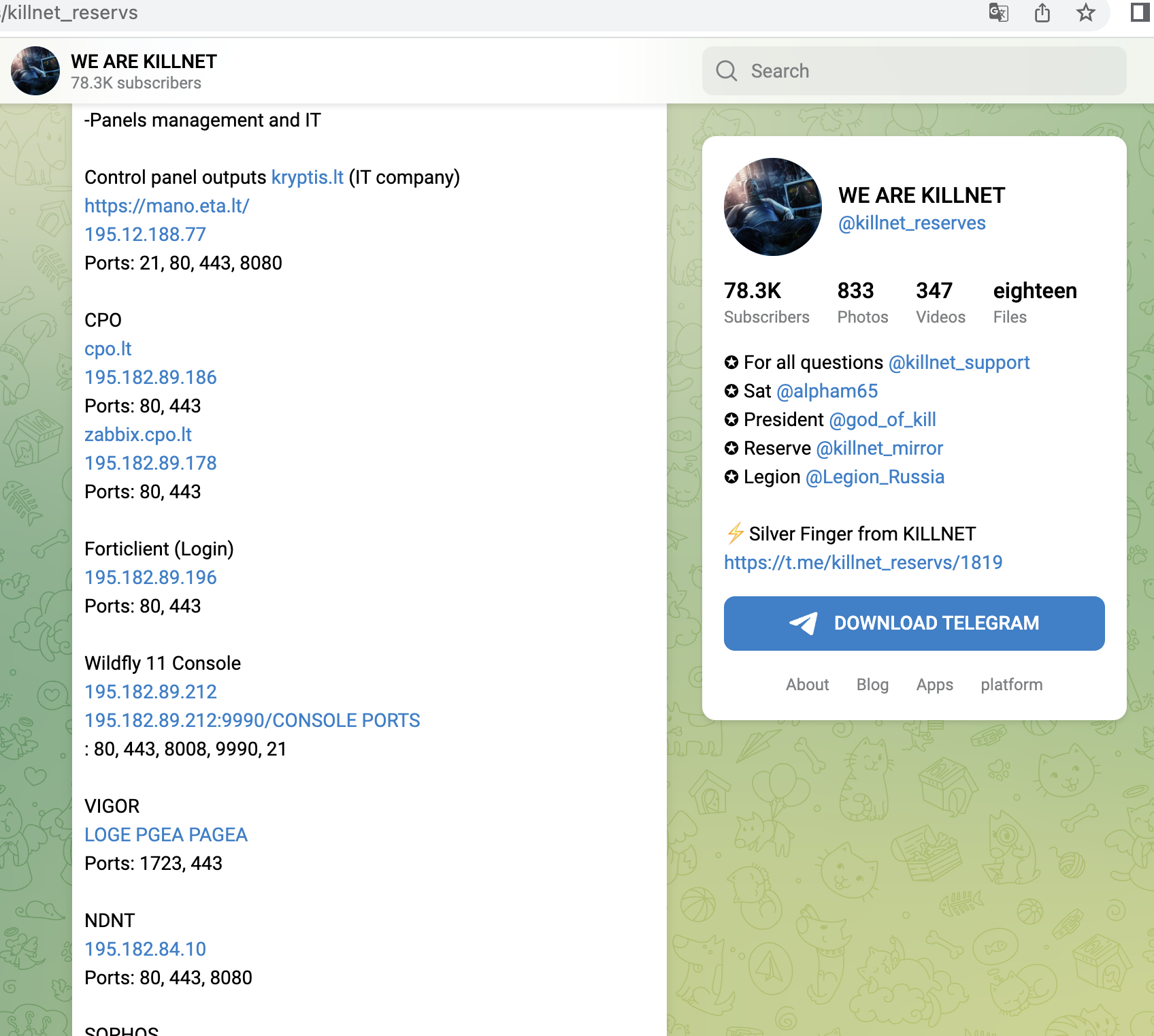
Shortly after, from 14.06, Killnet concentrated on Polish targets and attacked mainly companies here, e.g. a central payment service provider (dotpay), later the Ministry of Finance, a large ISP/TelCo, the refinery operator ORLEN or energy supplier PGNIG. Here we saw for the first time that not only the main websites were attacked, but rather the login portals for employees. Or Ecommerce-areas were found and targeted.
KillNet has learned a lot here and uses OSINT techniques to recon the target and to find the points that particularly "hurt". We see this approach regularly from mid-June onwards, and refined from wave to wave.
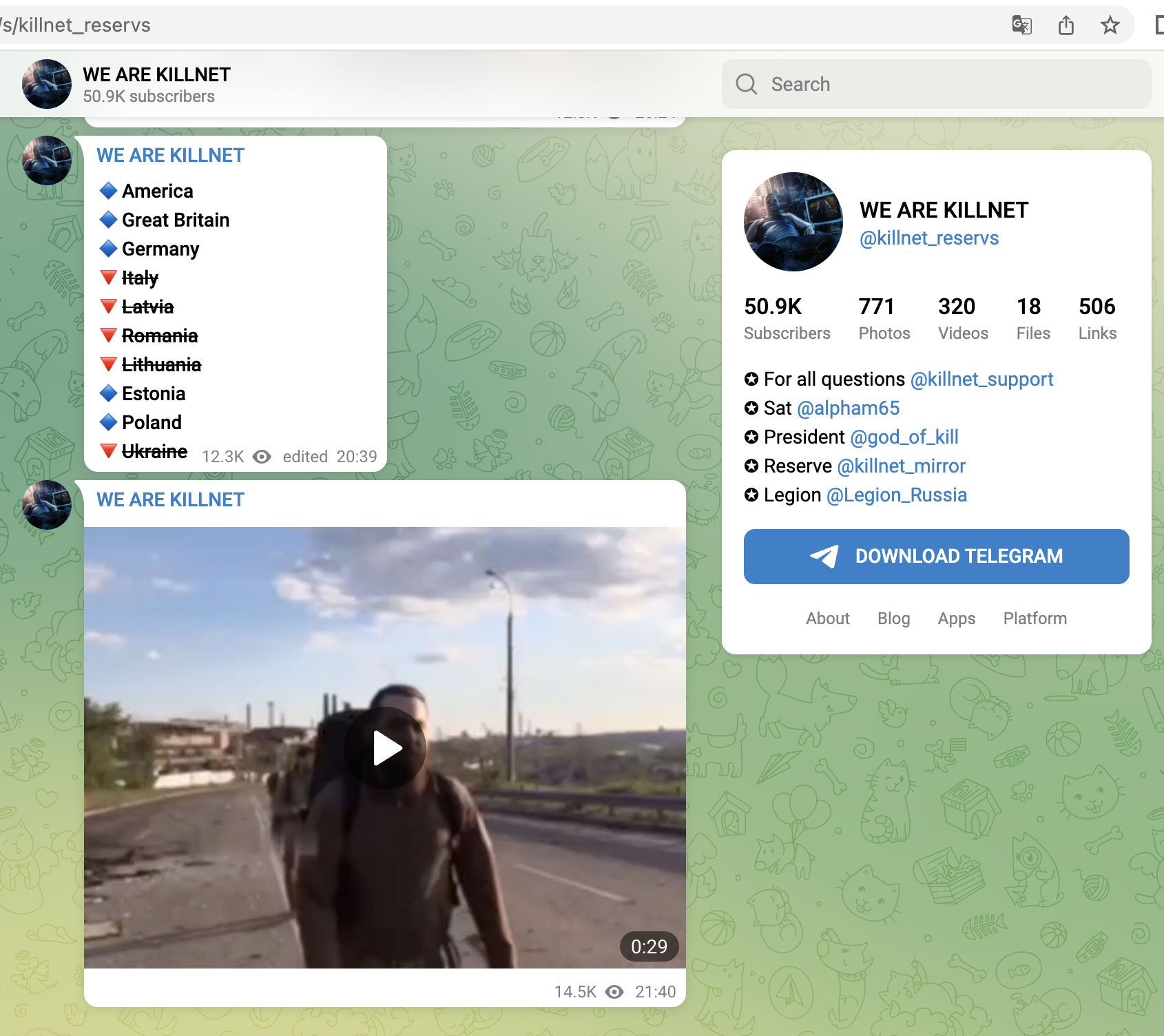
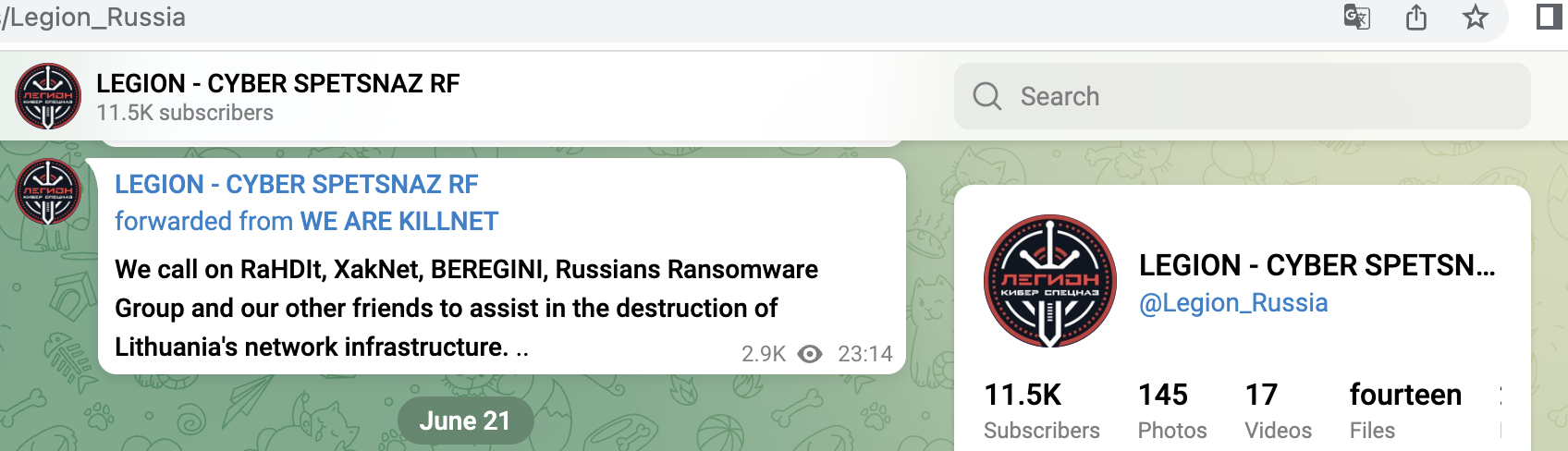
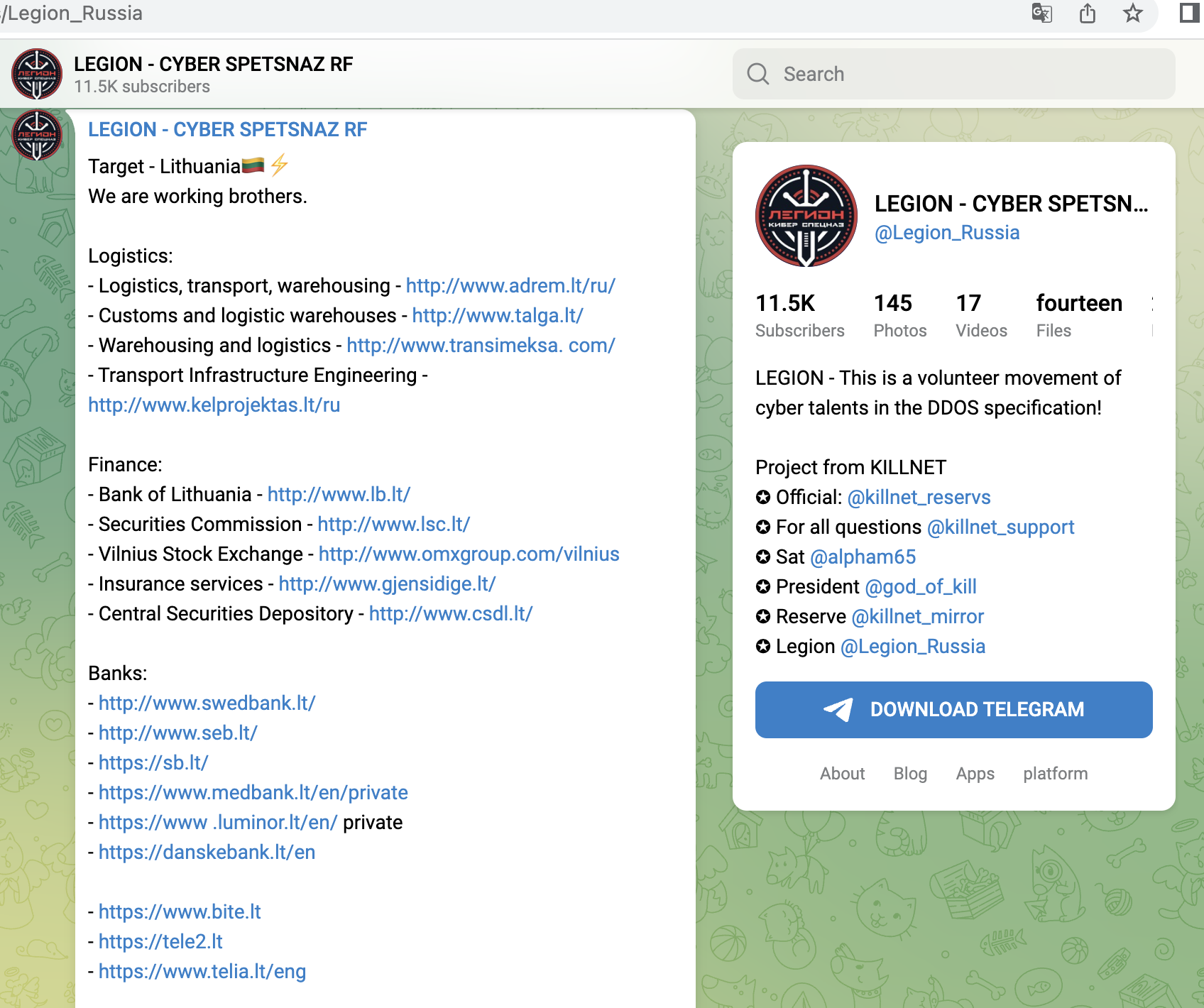
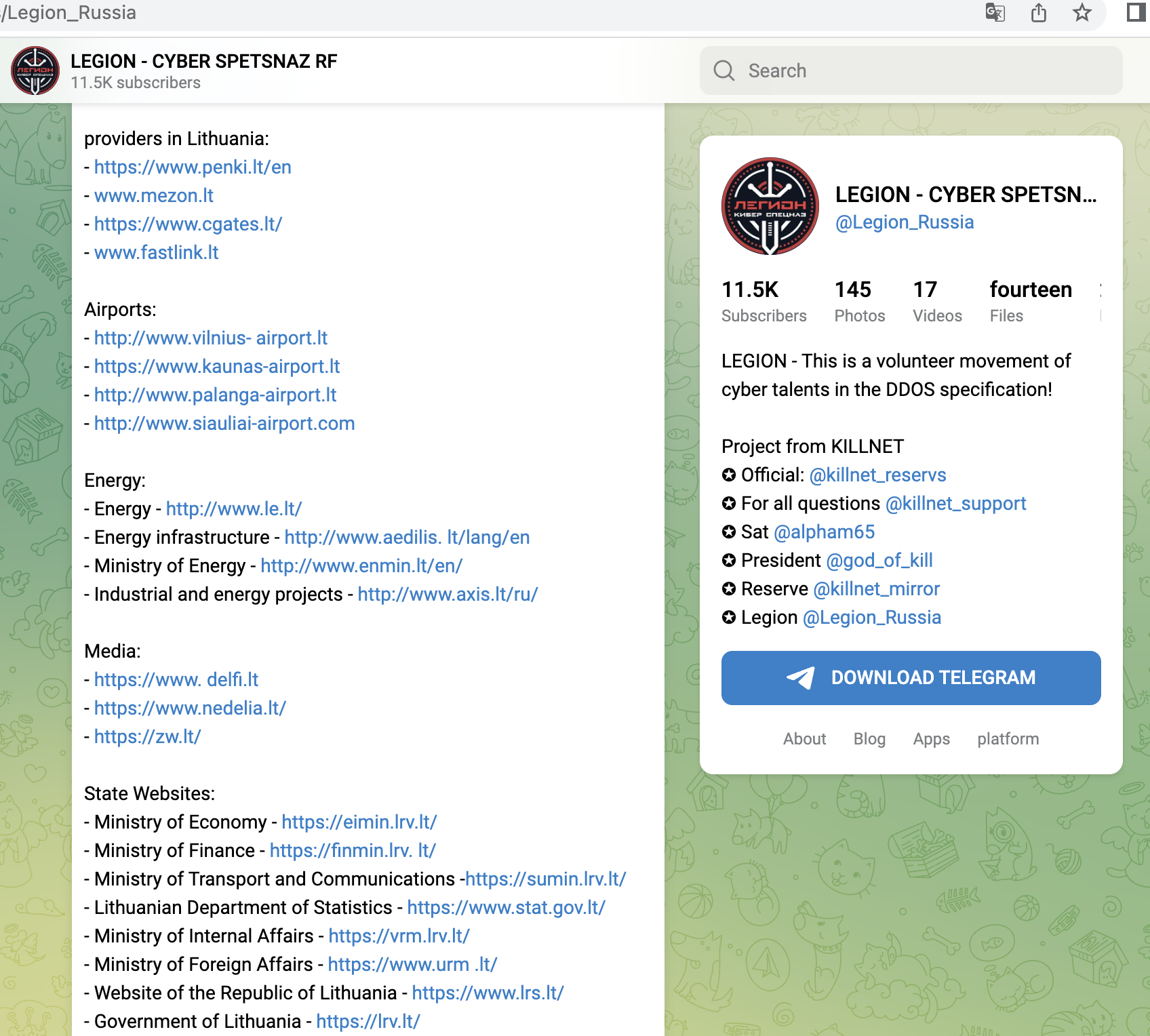
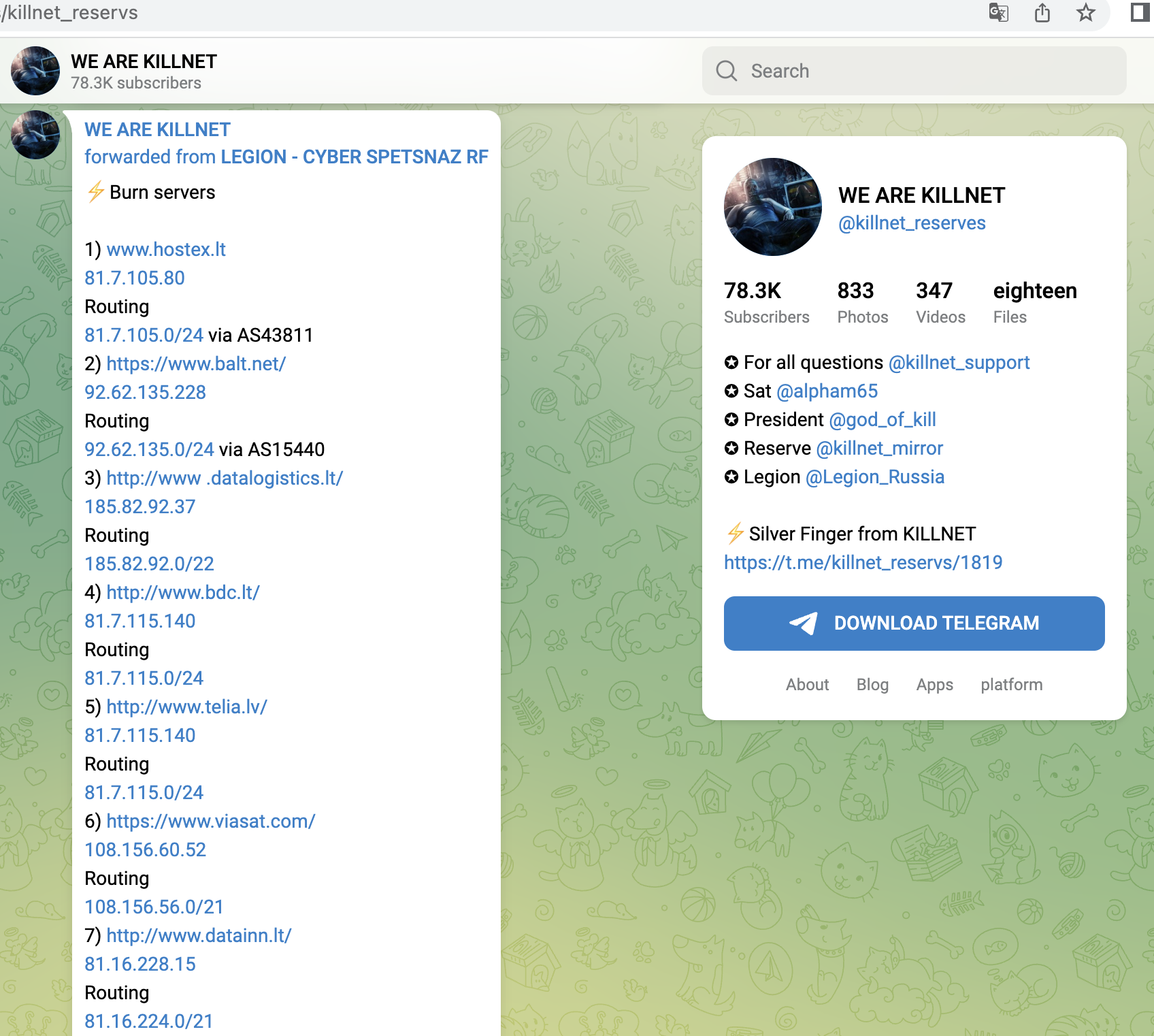
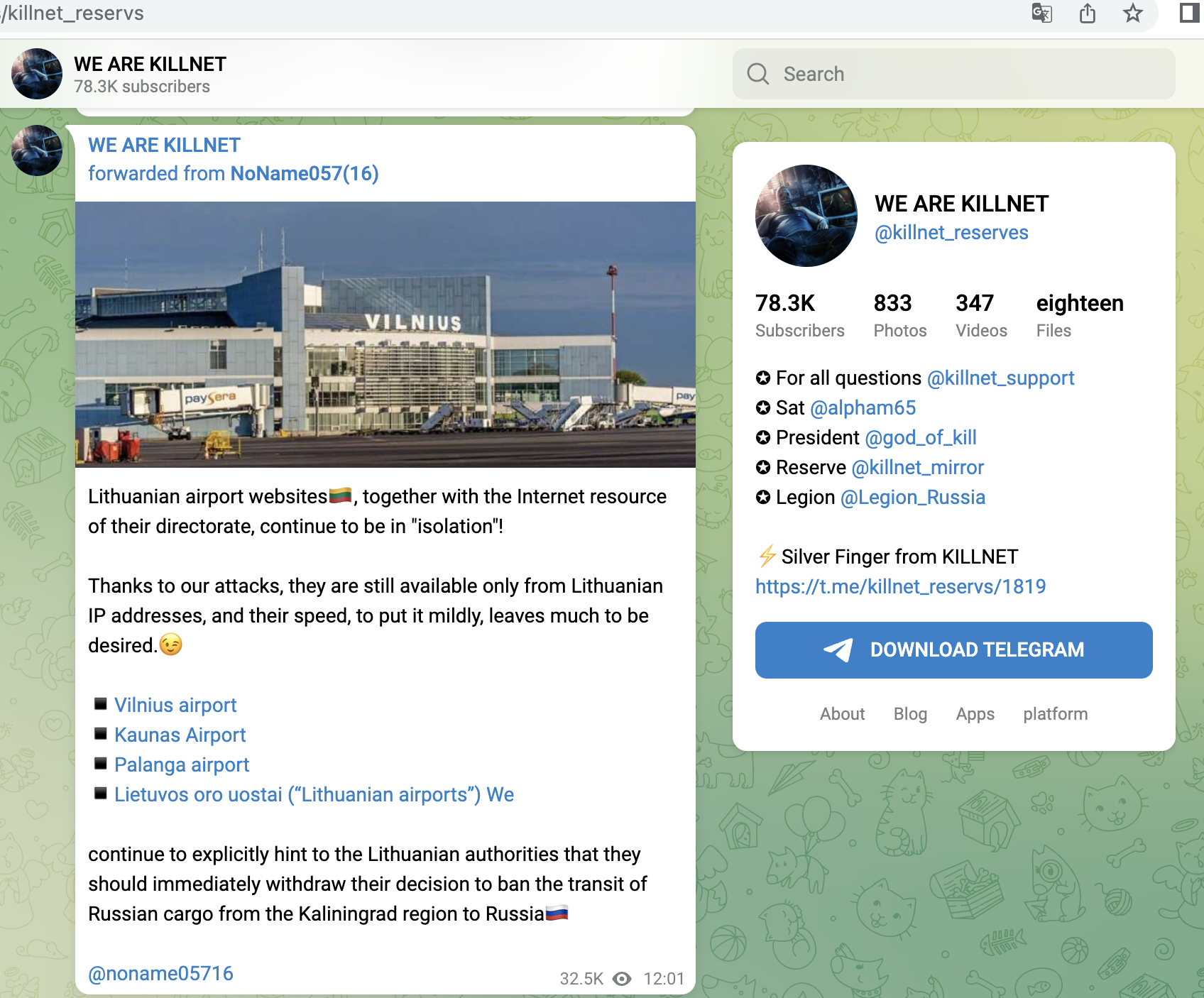
With the attacks on Lithuania and Norway from late June, they forced central services into so-called geo-fencing, i.e. isolation.
It should also be kept in mind that the Scandinavian countries and the three Baltic states are already very far advanced in the digitalisation of their societies and are therefore threatend by severe disruption of central services.
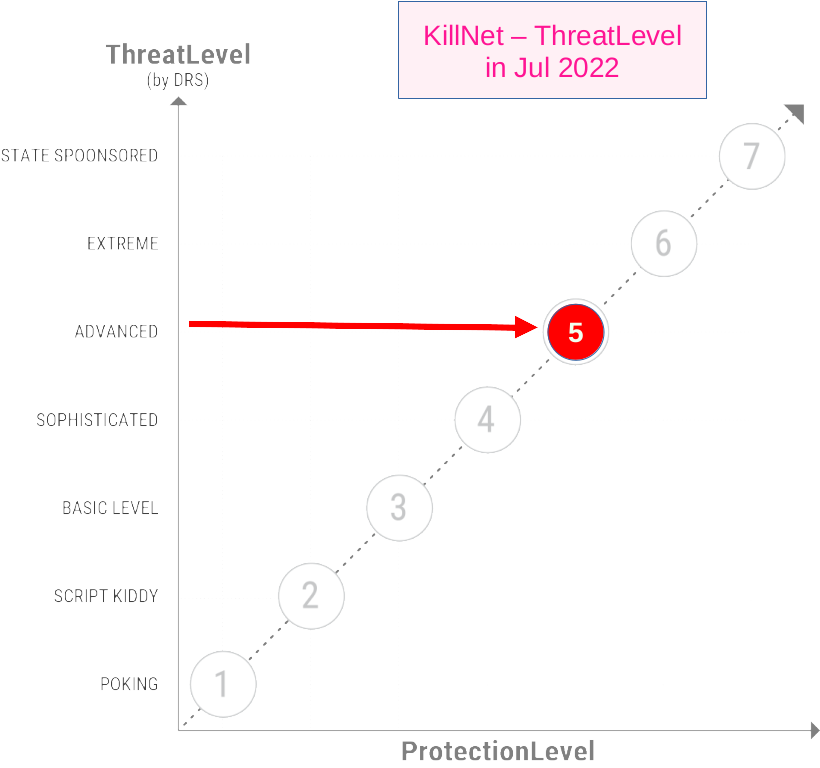
Update 2022-07-11
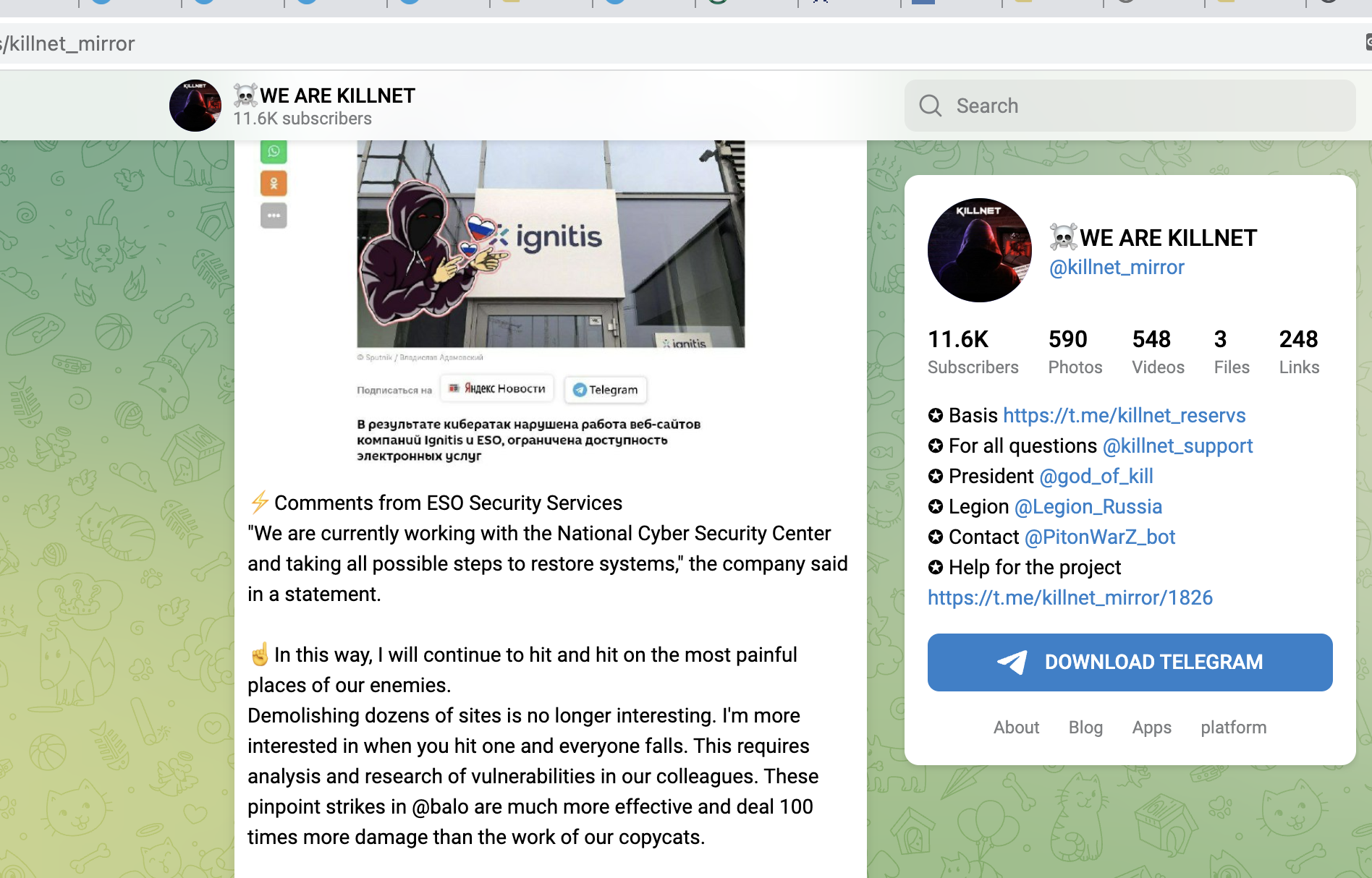
KillNet confirmed recently that it started to educate its members about OSINT-techniques to be able to find and hit valueble targets, not just main websites, confirming our analysis:
Demolishing dozens of sites is no longer interesting. I'm more interested in when you hit one and everyone falls. This requires analysis and research of vulnerabilities in our colleagues. These pinpoint strikes in @balo are much more effective and deal 100 times more damage
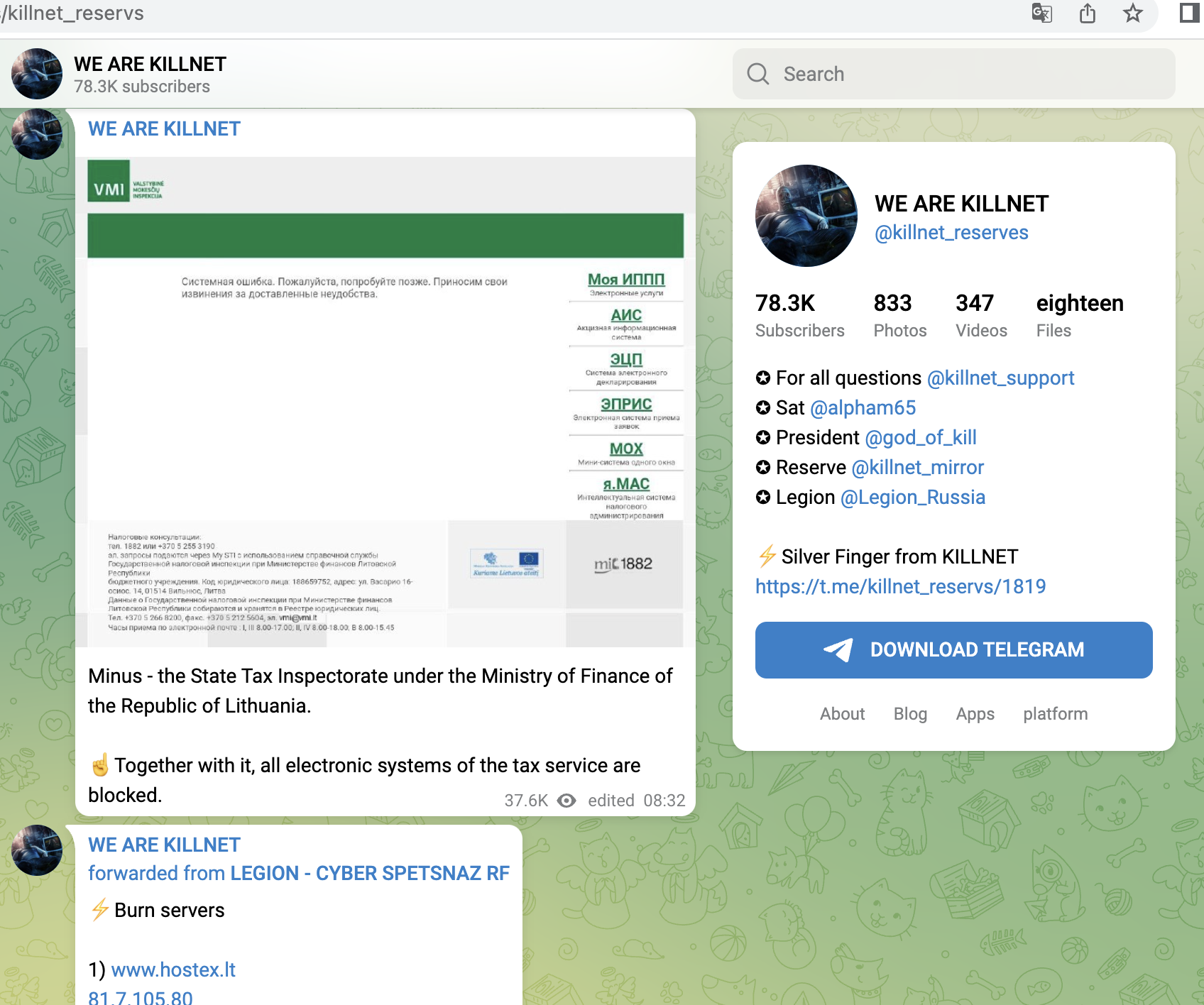
During the last weeks KillNet also started to target and attack Taxpaying-Systems, And it remains exciting which routes they will take in the future. from various states.
Our summary: As of early July 2022, KillNet developed to a serious threat even for protected services, because they leverage TTPs that allows for targeted and successfull DDoS-attacks. We expect other hacktivism-groups to learn from that, so that there will be most probably a raise of DDoS-Attacks all around the world. We already see this
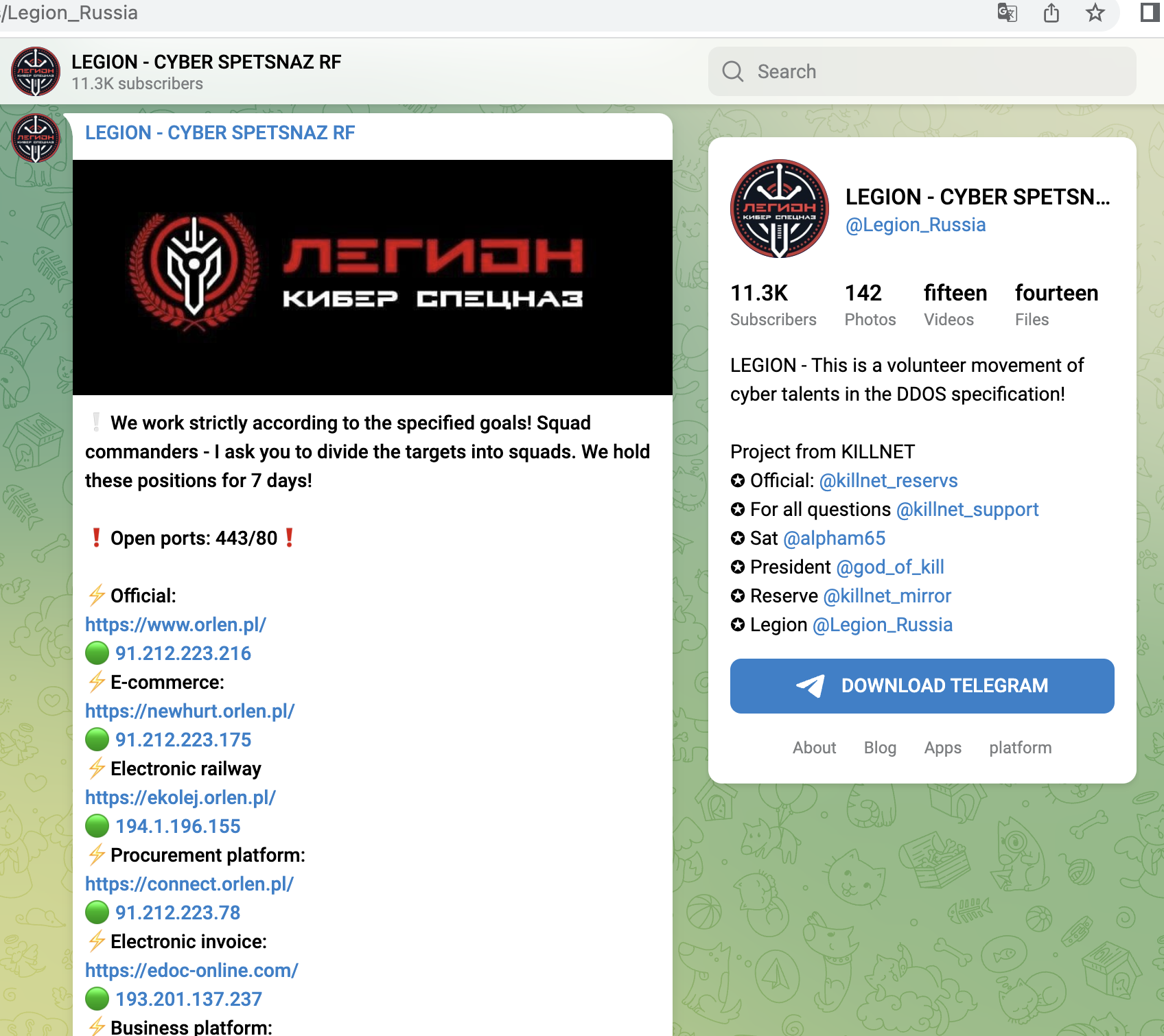
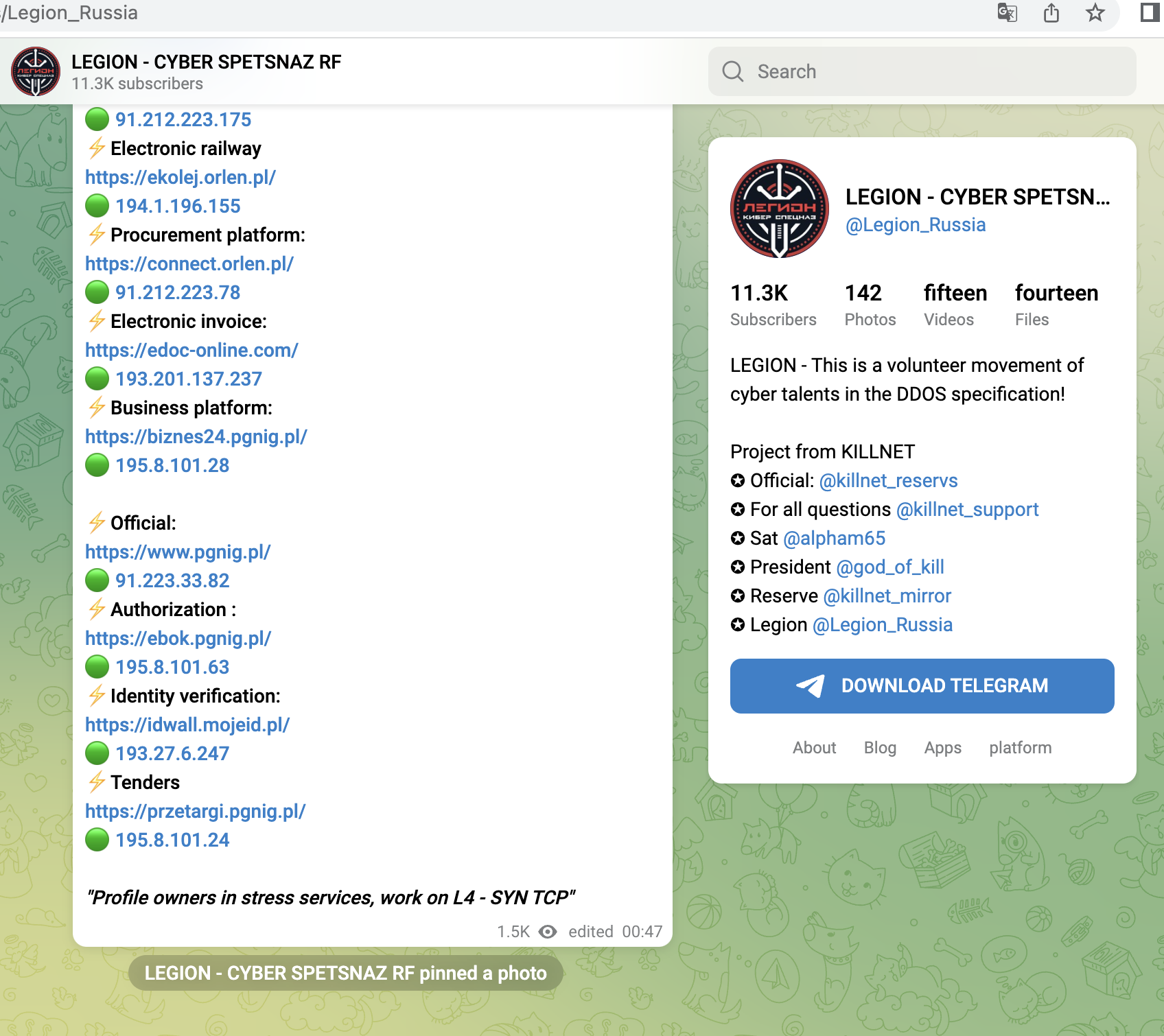
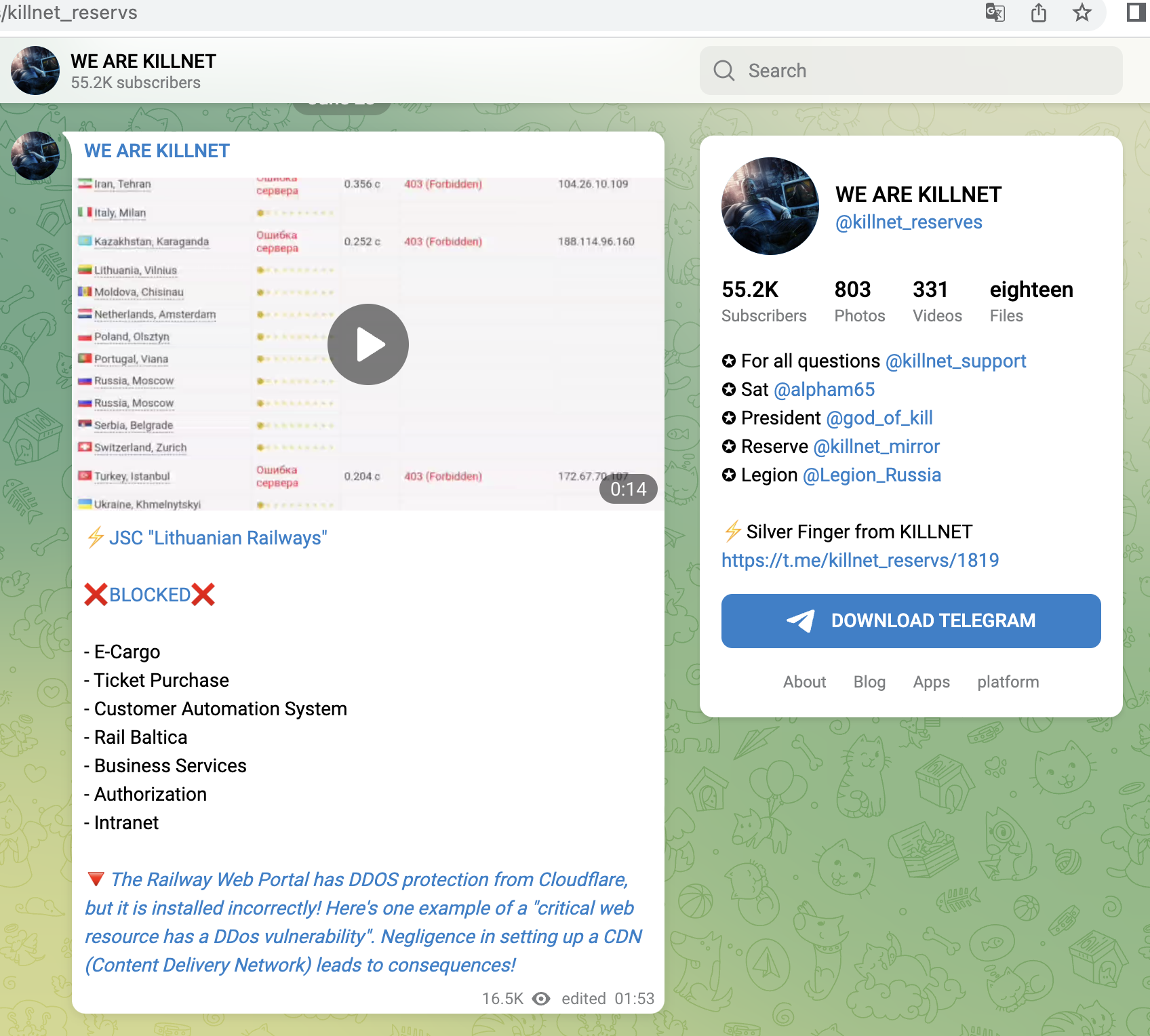
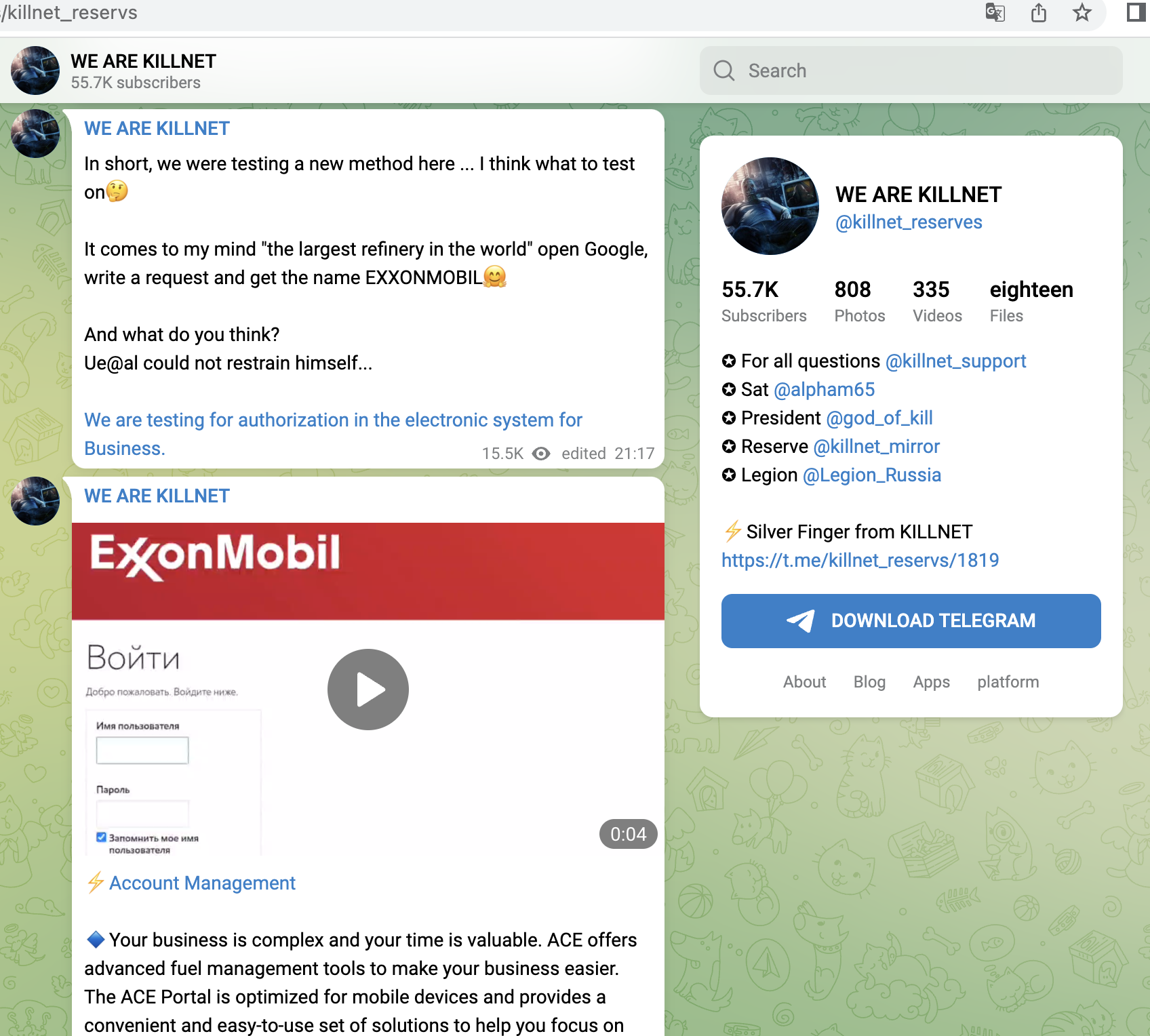
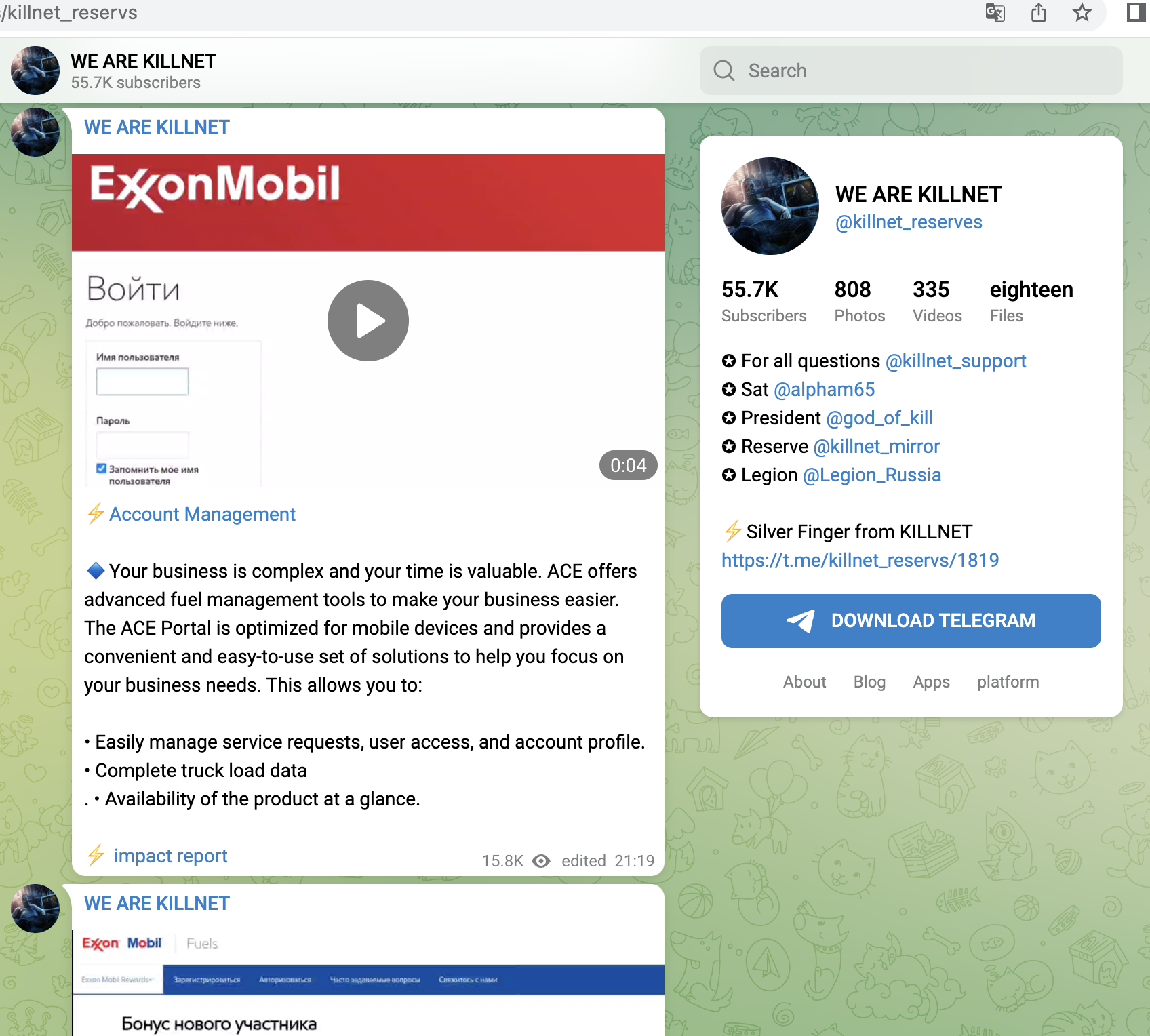
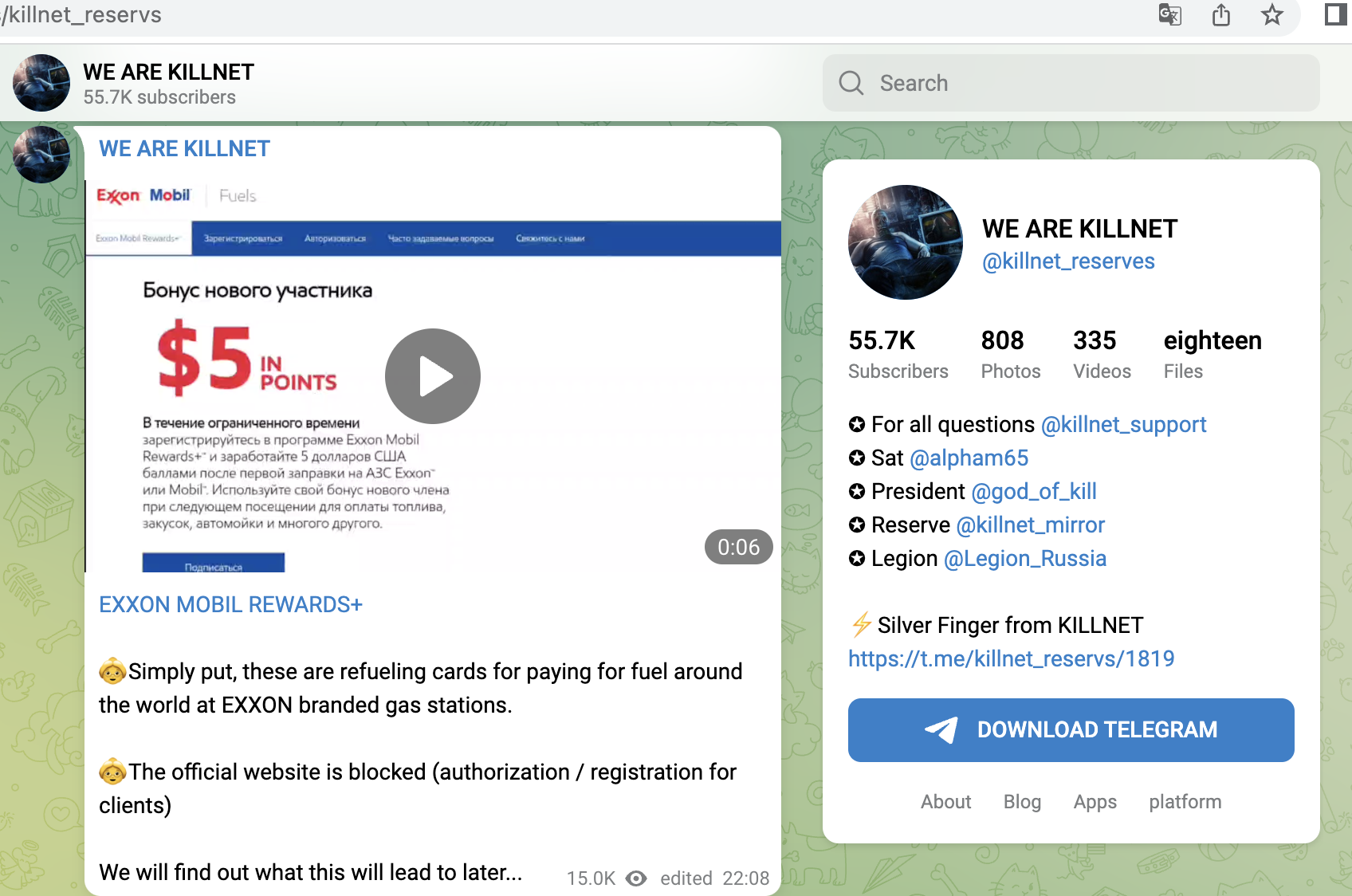
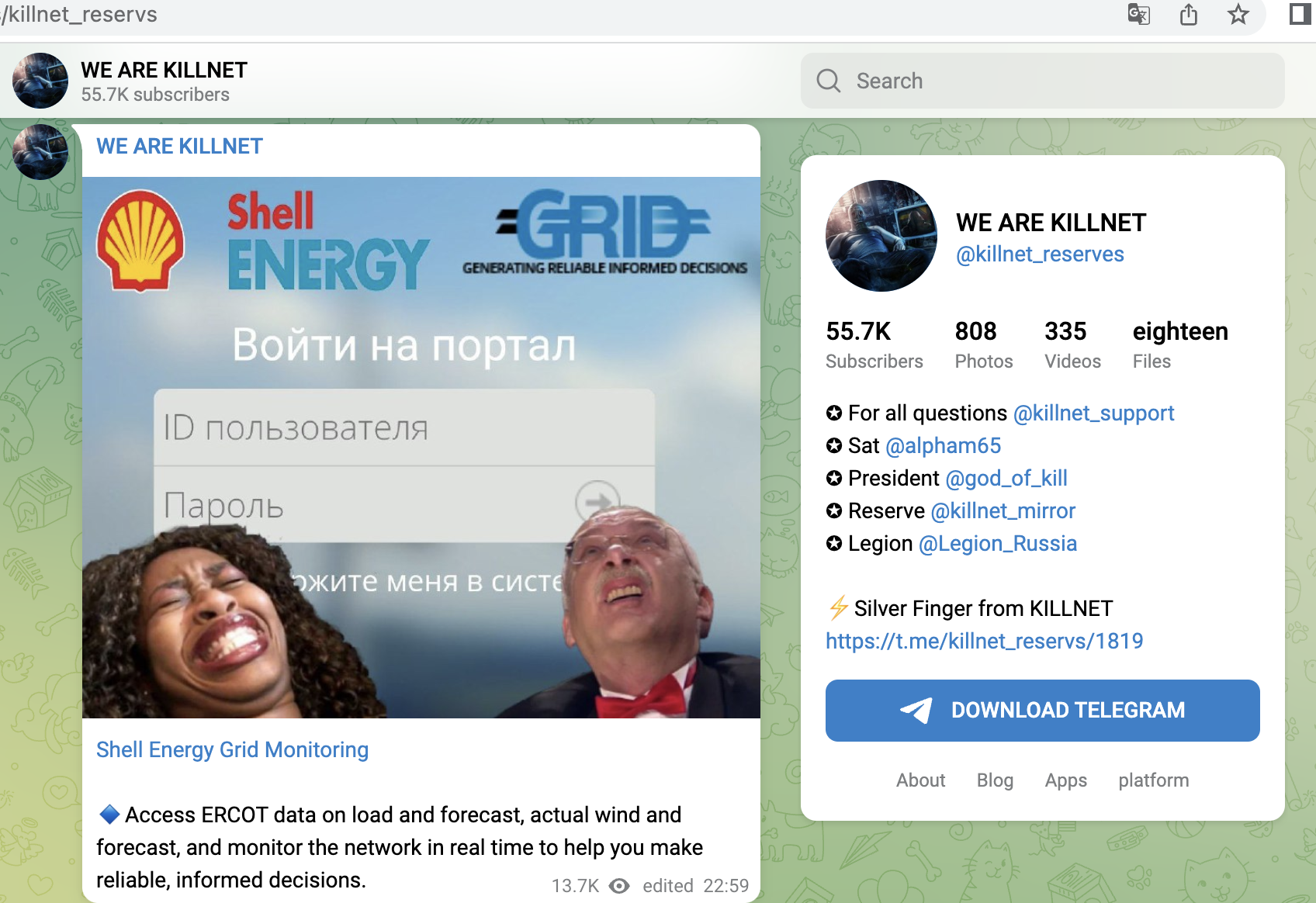
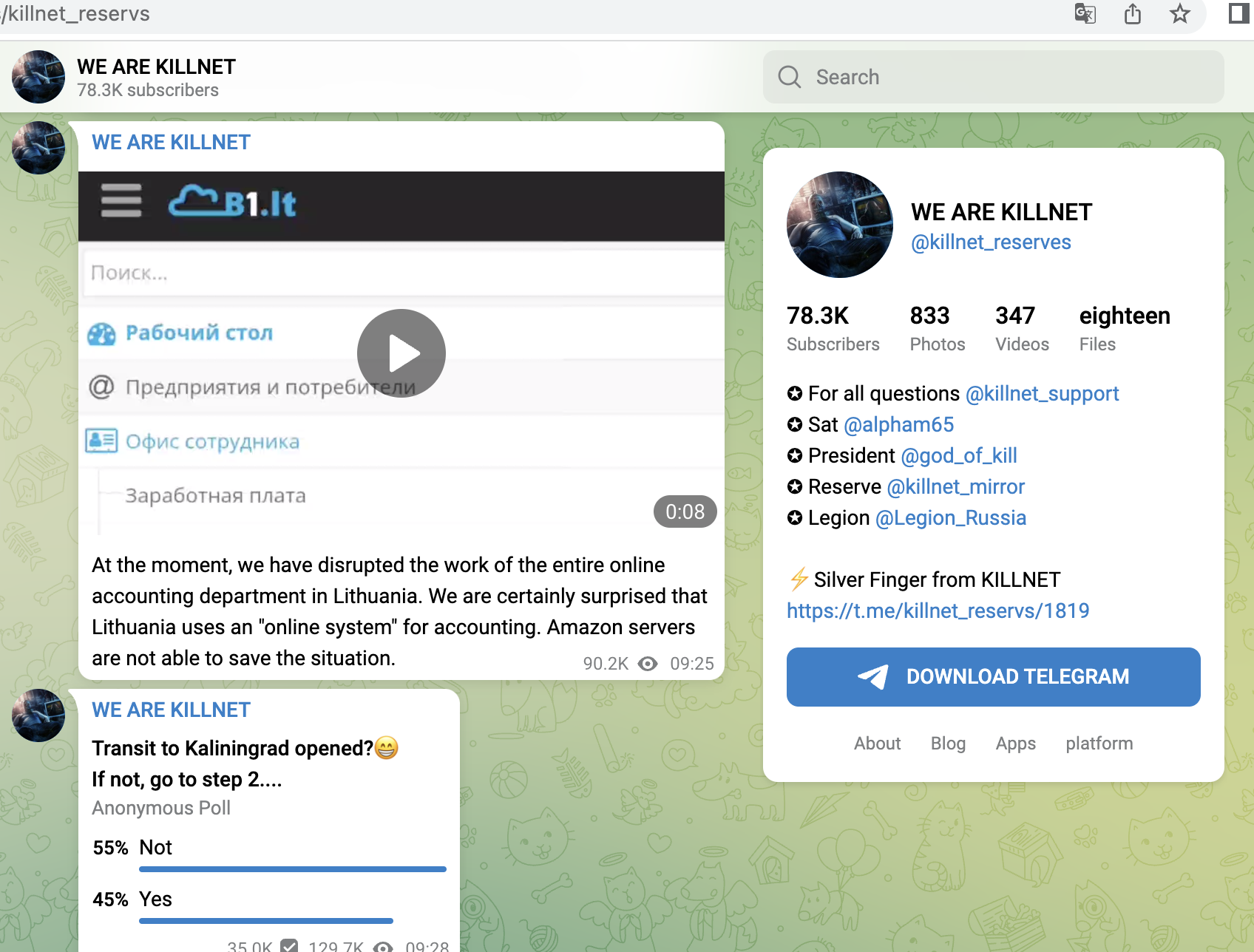
A small selection of specific KillNet targets with high relevance from the last 4 weeks, screenshots below:
- Access areas to Italian seaports
- Logistics Portal (Rail Information Exchange Portal) of ORLEN Refinery (Poland)
- Industrial customer logins of ORLEN - Refinery (Poland)
- central payment provider of Poland
- Central electronic court system (Lithuania)
- central bank ID service provider BankID (Norway)
- Business portal of the energy provider PGNiG (Poland)
- SPID - central login system for Italian banks
- Lithuanian railway operator, ticket system, customer login, business customer portal
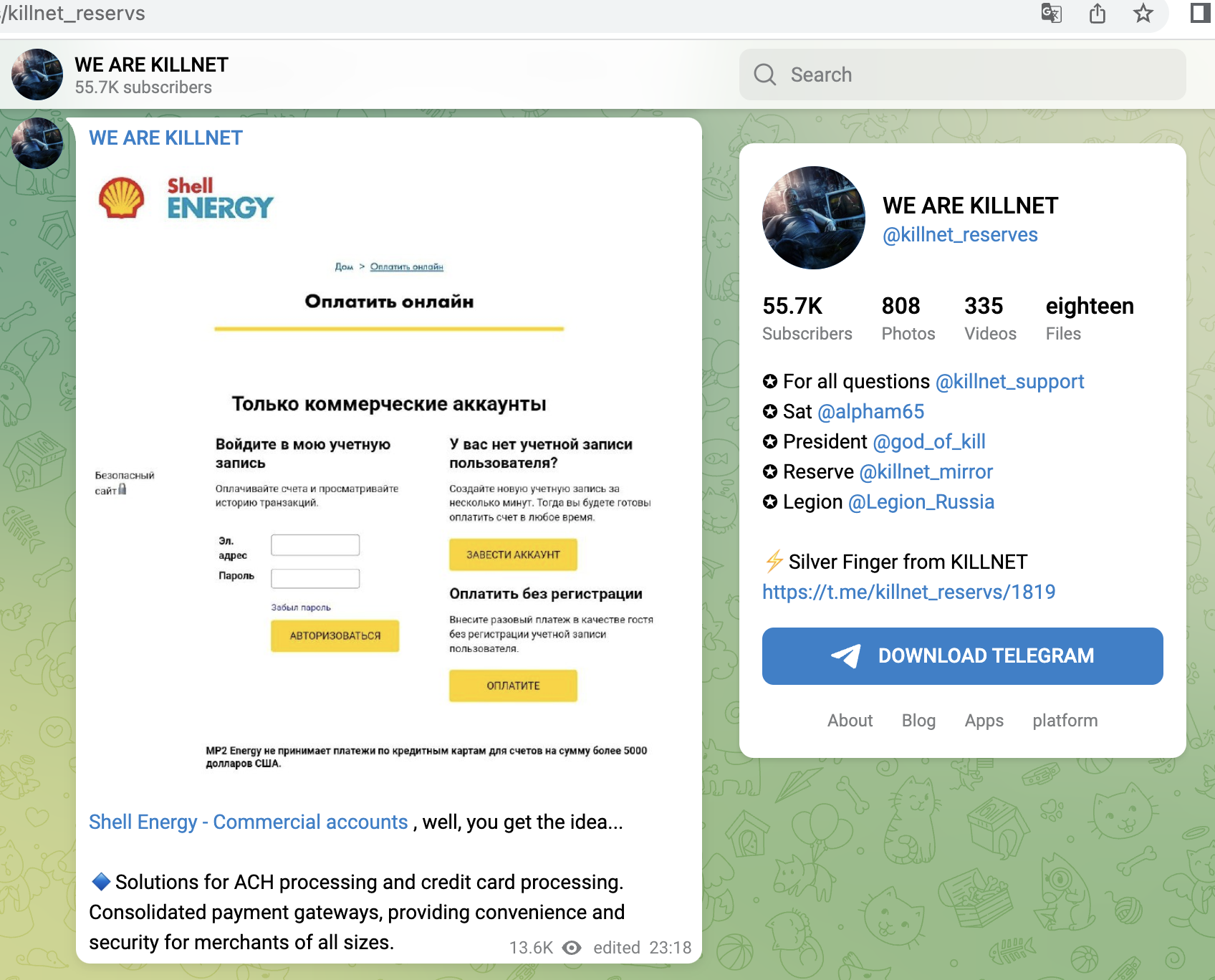
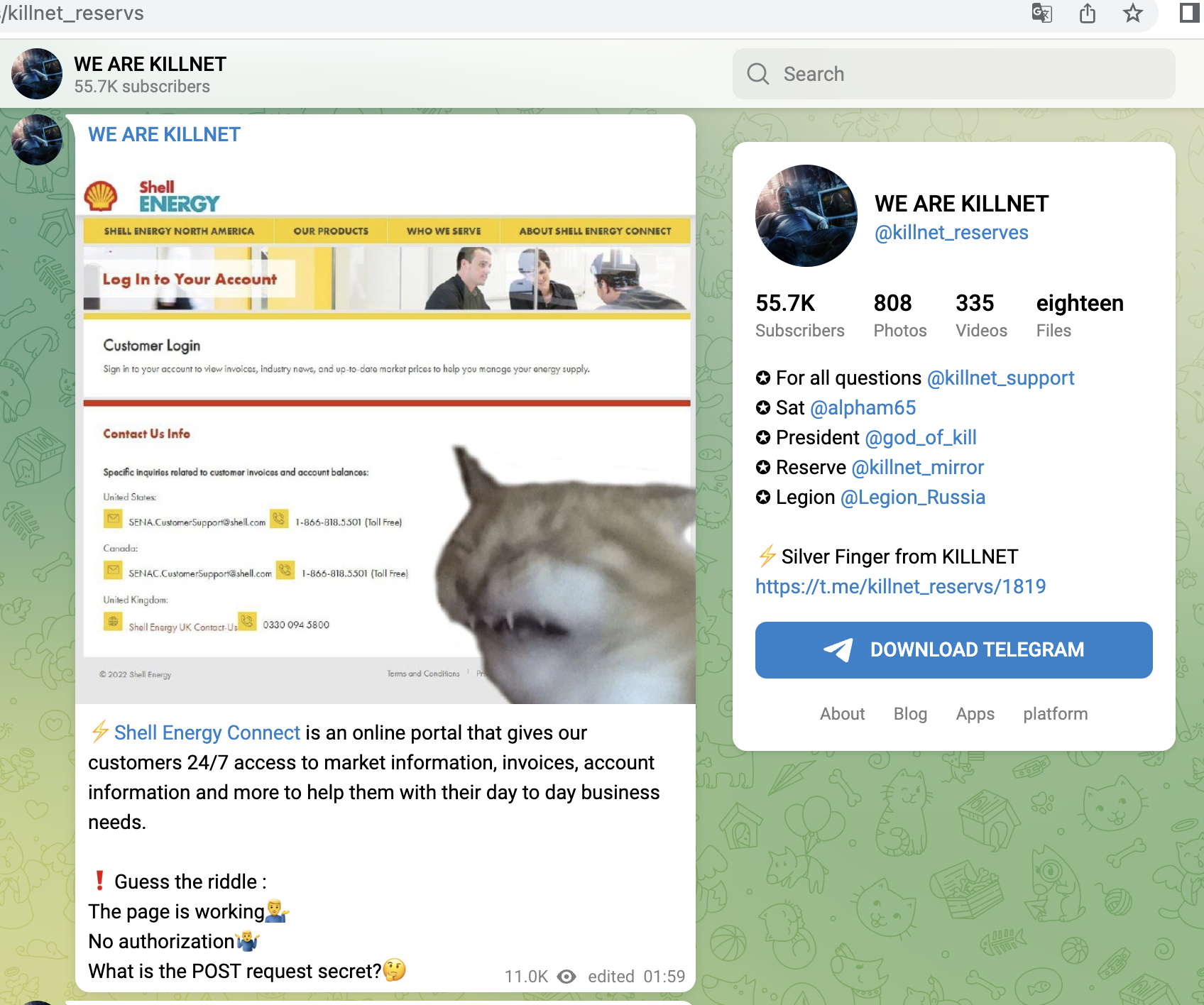
- B2B portals and logistics portals of ExxonMobile and Shell
- Shell Energy GRID Monitoring
- Online tax services Lithuania
- various airports in Europe
- Central billing service (Lithuania)
- Stock exchanges in Lithuania, Colombia, Poland
- US Federal Tax Payment System (USA)
- Polish Tax Payment System
- ... to be continued ...
KillNet - APT
(Update from May 2022)
Starting End of April, a new pro-Russian group "KillNet" appeared, which made a name primarily through DDoS-attacks.
The selection of targets is usually country-based, so Italy, Lithuania, Poland, but also Germany were among the targets.
In some cases "only" government websites were attacked, but in other cases also sensitive sensitive, critical infrastructure such as port terminals (Italy) or larger or larger logistics companies, or even banks.
Communication goes via various Telegram-Channels.
Killnet is also capable of causing massive disruptions at a provider like Hetzner; not exactly a lightweight.
Source with Analysis:
State-Sponsored Attacks
Feb 25th, the day after russia invaded ukraine, CISA (Cybersecurity & Infrastructure Security Agency), which is part of the U.S. Department of Homeland Security has issued an unusual warning to business that says they should be prepared to defend against cyber attacks originating from Russia.
Feb 28th has seen a targeted DDoS-attack against KA-SAT/VIASAT. As a result of this attack, parts of the satellite-based internet in Ukraine and also in Europe went down. According to various reports, KA-SAT is also used by the Ukrainian military.
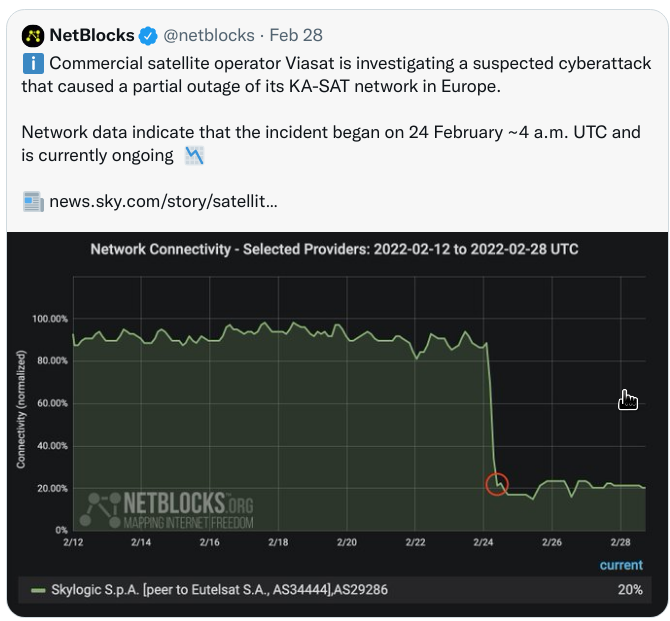
From the Viasat - Incident Report:
At approximately 0302 UTC on 24 February 2022, high volumes of focused, malicious traffic were detected emanating from several SurfBeam2 and SurfBeam 2+ modems and/or associated customer premise equipment (CPE) physically located within Ukraine and serviced by one of the KA-SAT consumer-oriented network partitions. This targeted denial of service attack made it difficult for many modems to remain online.
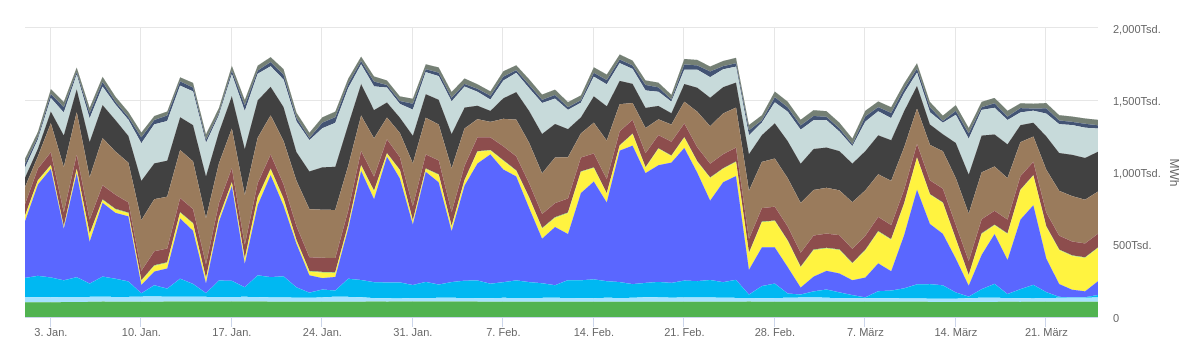
As collateral damage, the control accesses of 6000 wind turbines went offline in the course of this attack in Germany.
As a result, the amount of energy fed into the grid by wind turbines dropped by 90% for about 2 weeks, although there were enough windy days during this period.
Update 2022-08-22
Risky Business Newsletter reported
VIASAT hack impact in France: According to the minutes of a closed-doors meeting held by Stéphane Bouillon, Secretary General of Defense and National Security for the French Parliament's National Assembly, the Russian hack of the VIASAT satellite internet network had "affected" French ambulance (phone number: 15) and firefighting (phone number: 18) emergency services. The extent of the impact was not detailed.

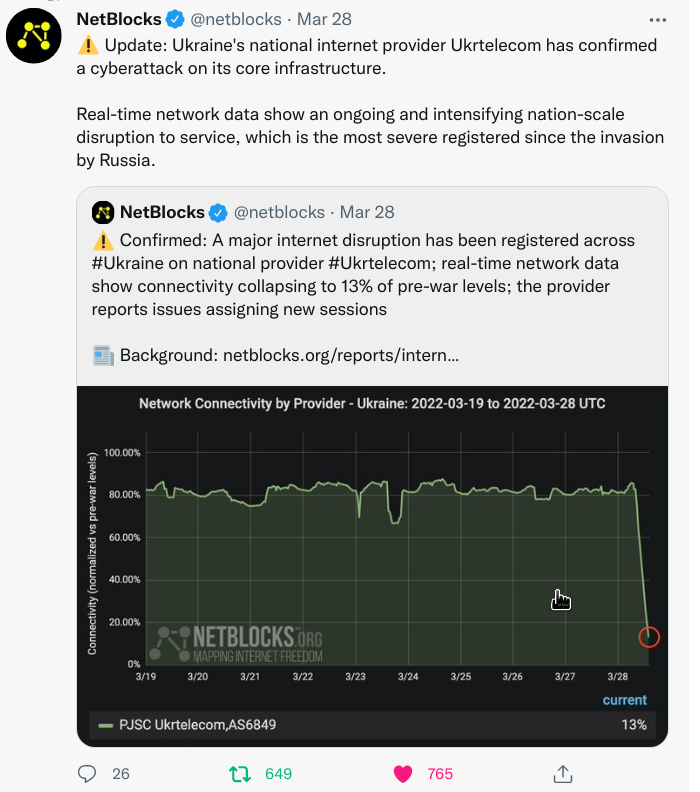
March 28th: Ukraine's national internet provider Ukrtelecom has confirmed a cyberattack on its core infrastructure.
Hacktivism and Clownerie
The above attacks can most probably be assigned to the state-sponsored spectrum, but there was also a lot of hacktivism from both sides. some at LOIC level, some quite serious.
Fragen? Kontakt: info@zero.bs