inb4 RuhRoh: yes, we know and acknowledge the 90s. But this is now, 27years later.
The "Classical" DDoS-Attack-Vectors are usually classified as either volumetric Layer 3/4, Network-based attacks that try to overwhelm the network-capacity or Layer 7, Application-based attacks that try to overwhelm the computing-capacity in applications.
With the decline of pure UDP-Floods an the rise of TCP also on the volumetric front as seen by most companies in 2022, stack-based attacks emerged as a successful technique for launching Distributed Denial of Service (DDoS) attacks. A stack-based attack targets the layer between the edgerouters of a network and the application itself: usually Firewalls, Loadbalancers, SSL-Offloaders or WAFs.
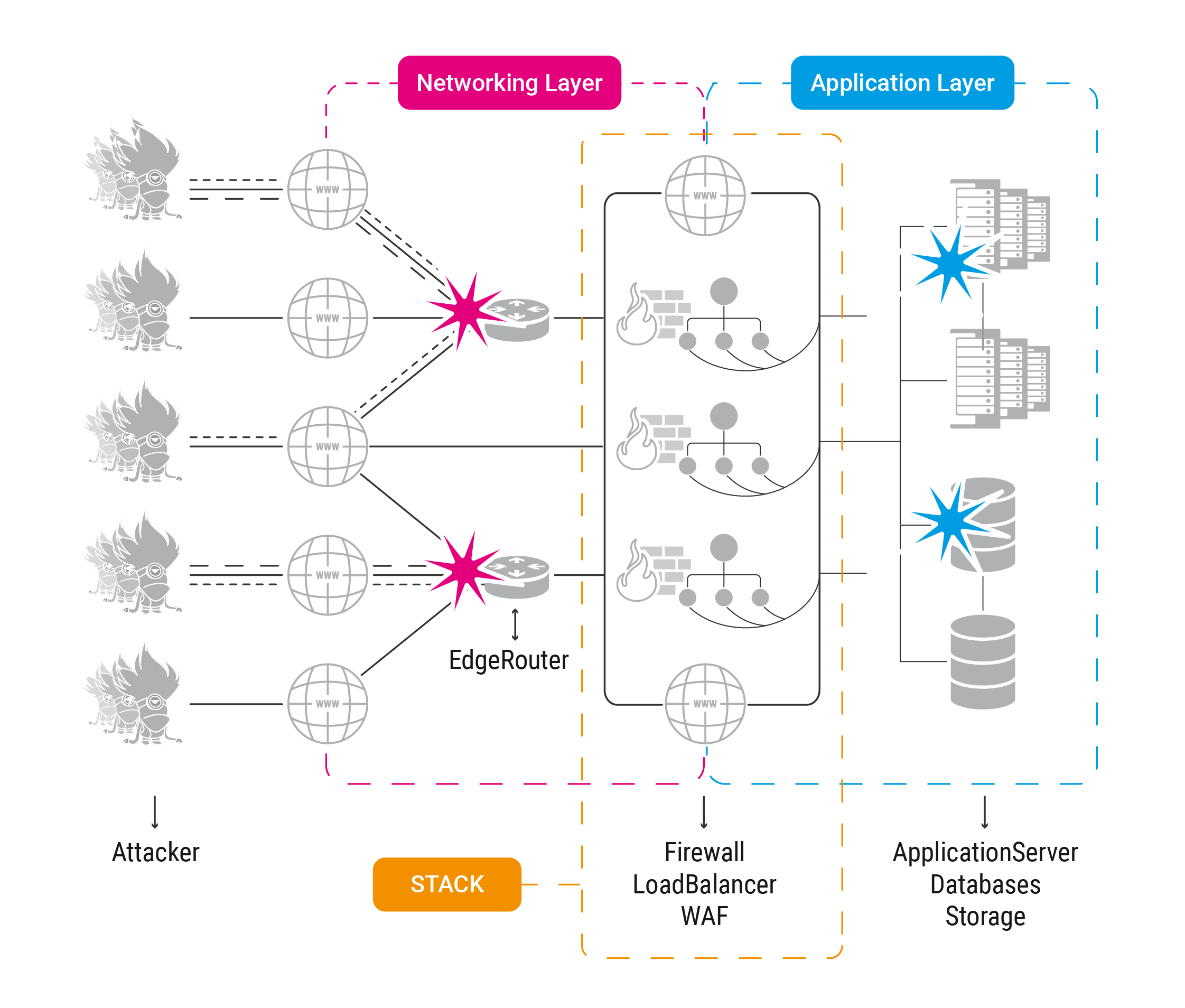
One of the most well-know StackAttack was SlowLoris, released 2009, meaning the issues are not new, but have not been classified as an own DDoS-attackvector until now.
The main reasons stack-based attacks were successful in 2022 is that they are relatively simple to execute. Unlike other DDoS techniques, such as network flooding or amplification attacks, stack-based attacks do not require a large number of compromised devices or a lot of bandwidth. All an attacker needs is a small number of devices or a single computer with a high-speed internet connection to launch a stack-based attack.
Another reason for the success of stack-based attacks is that they are difficult to detect and defend against. Traditional DDoS mitigation techniques, such as traffic filtering and rate limiting, are not effective against stack-based attacks because they do not target the network layer. Instead, they target areas like the memory/cpu of the device, which is not typically protected by these types of security measures, but also might affect diskstorage (think: Logstores) or other bottleneck-prone areas.
There are various vectors that qualify as StackAttack and that can be very successful when executed from a botnet, such as
- TCP-Handshakes
- TLS-Handshakes
- IP-Spoofing
- IPSec-Attack
- HTTPS-Replay-Attacks
- LogOverflow
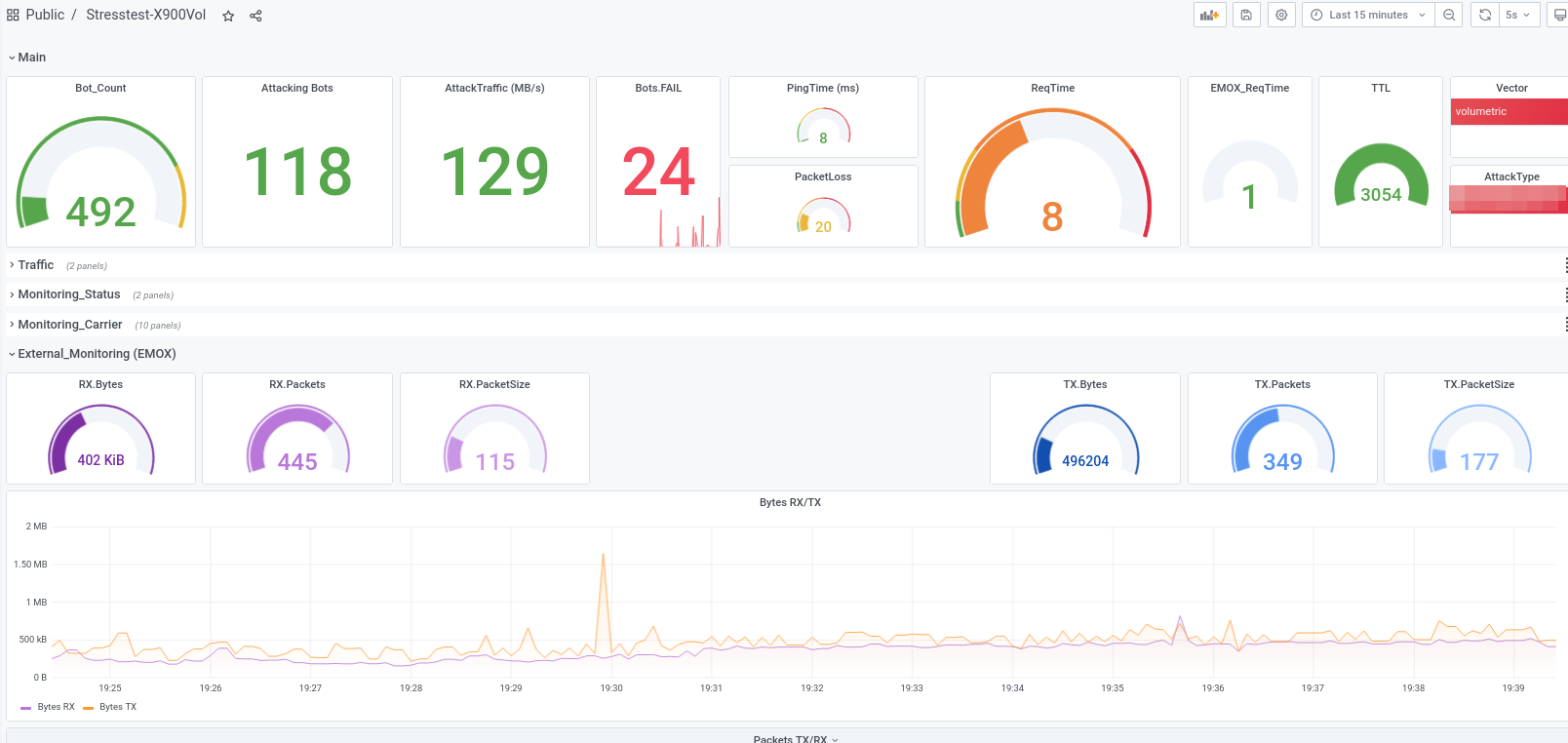
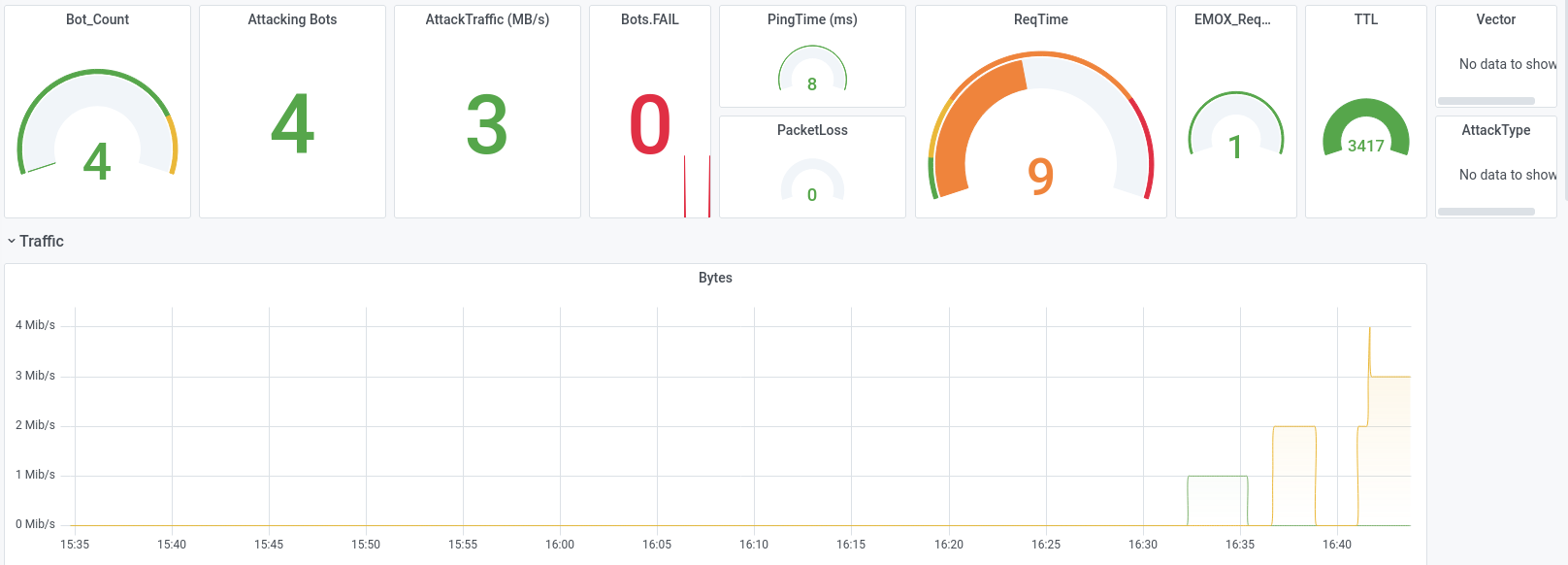
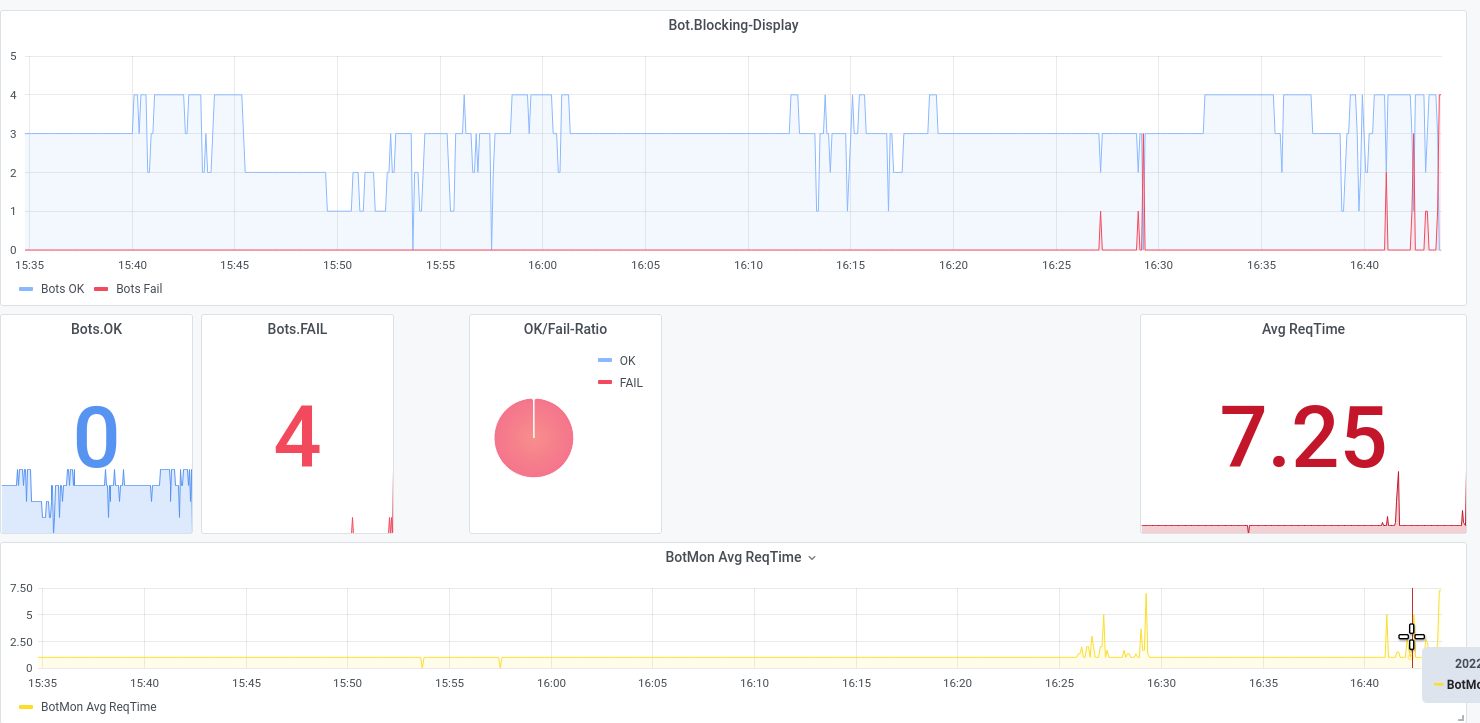
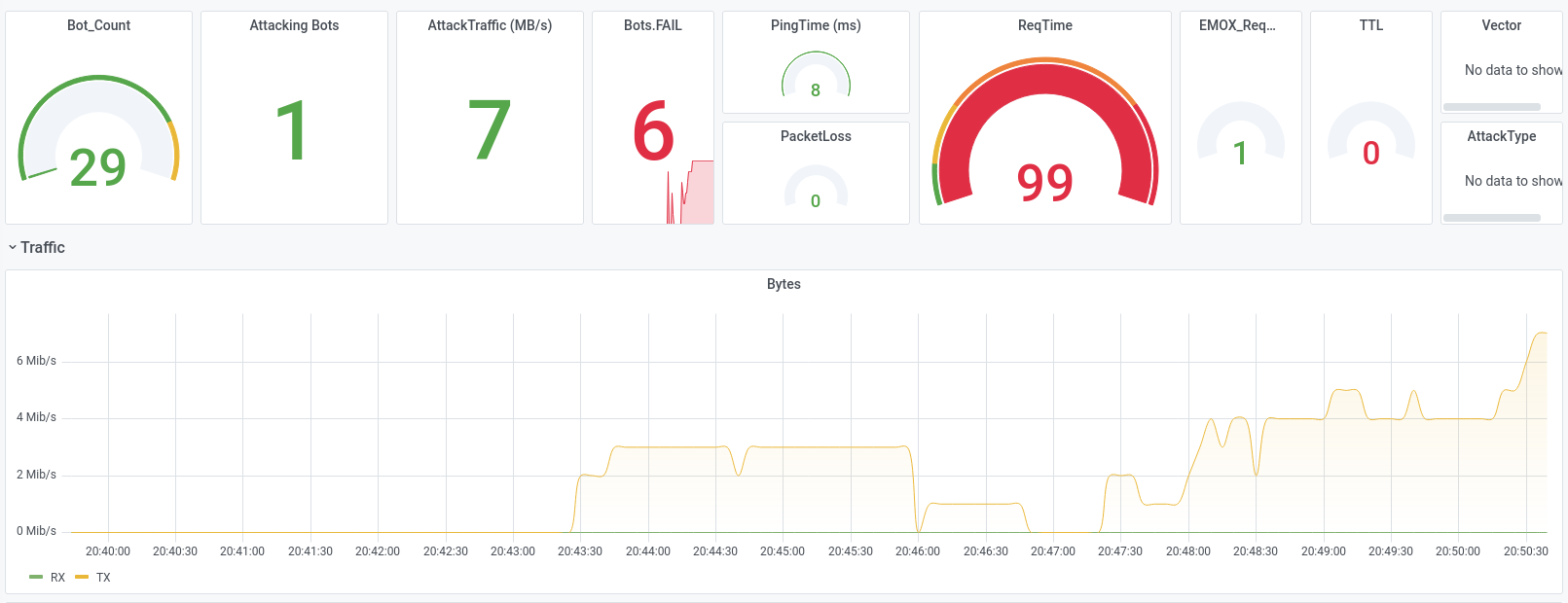
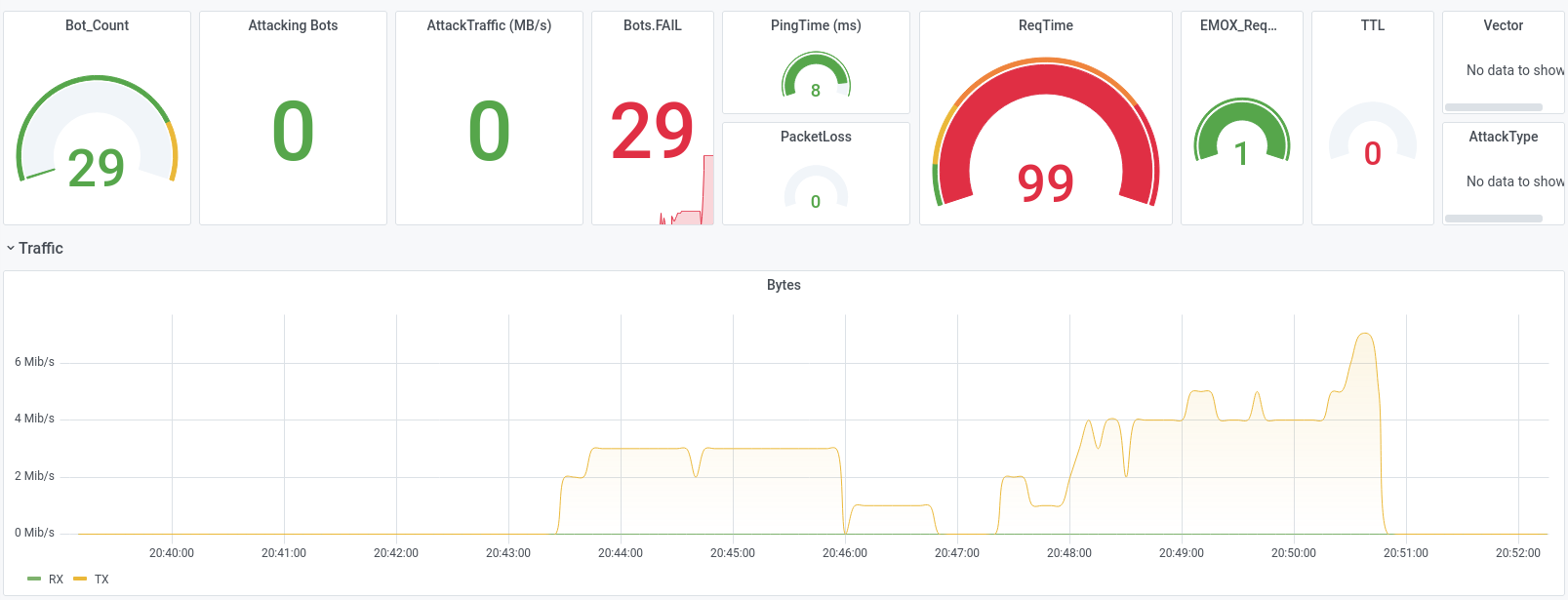
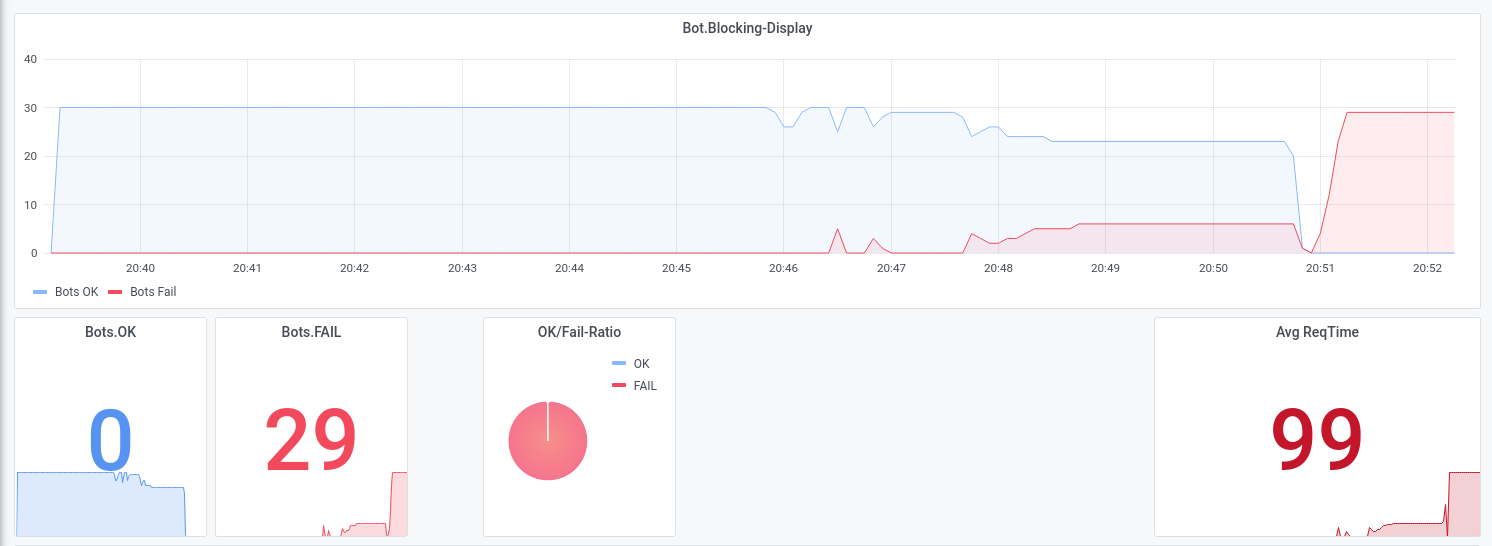
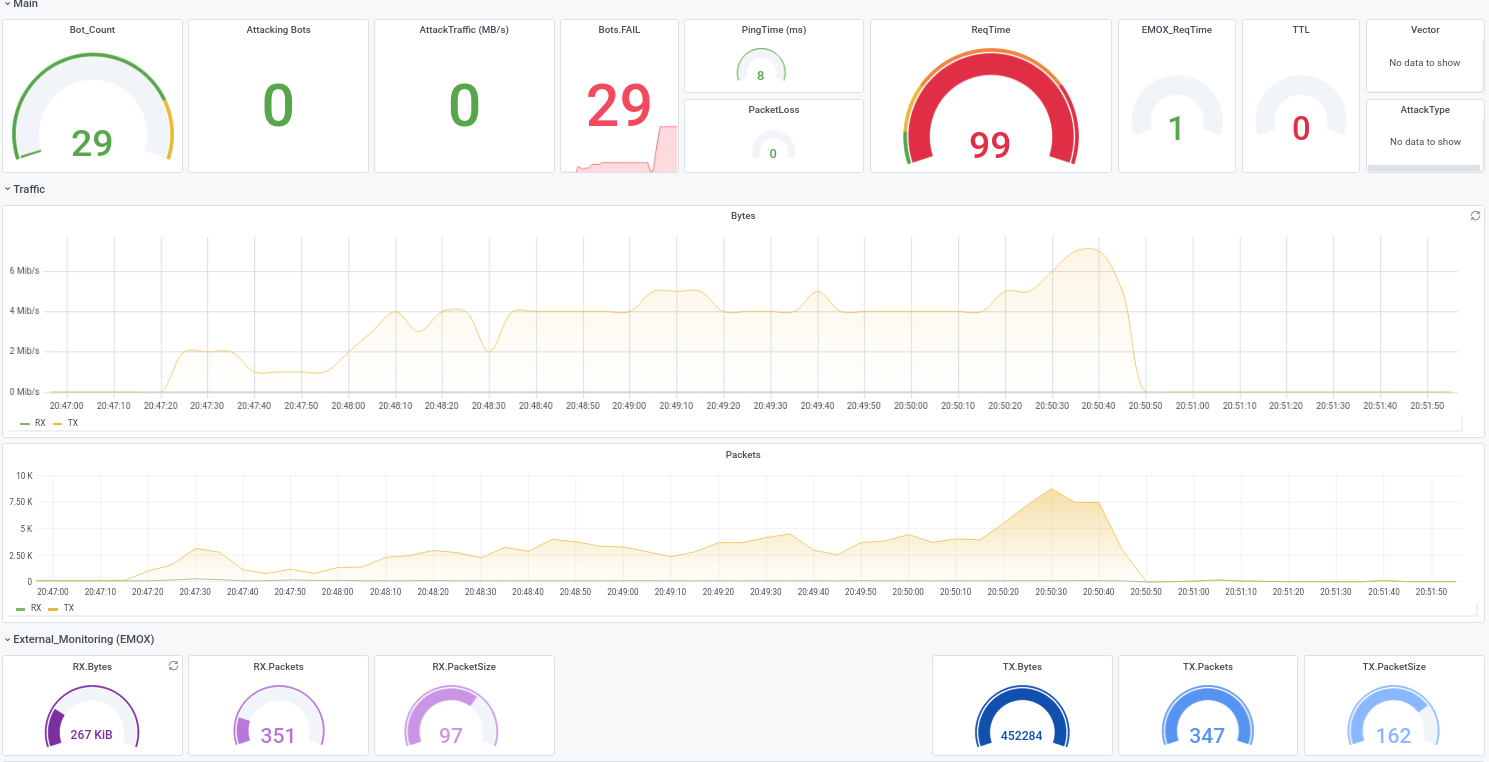
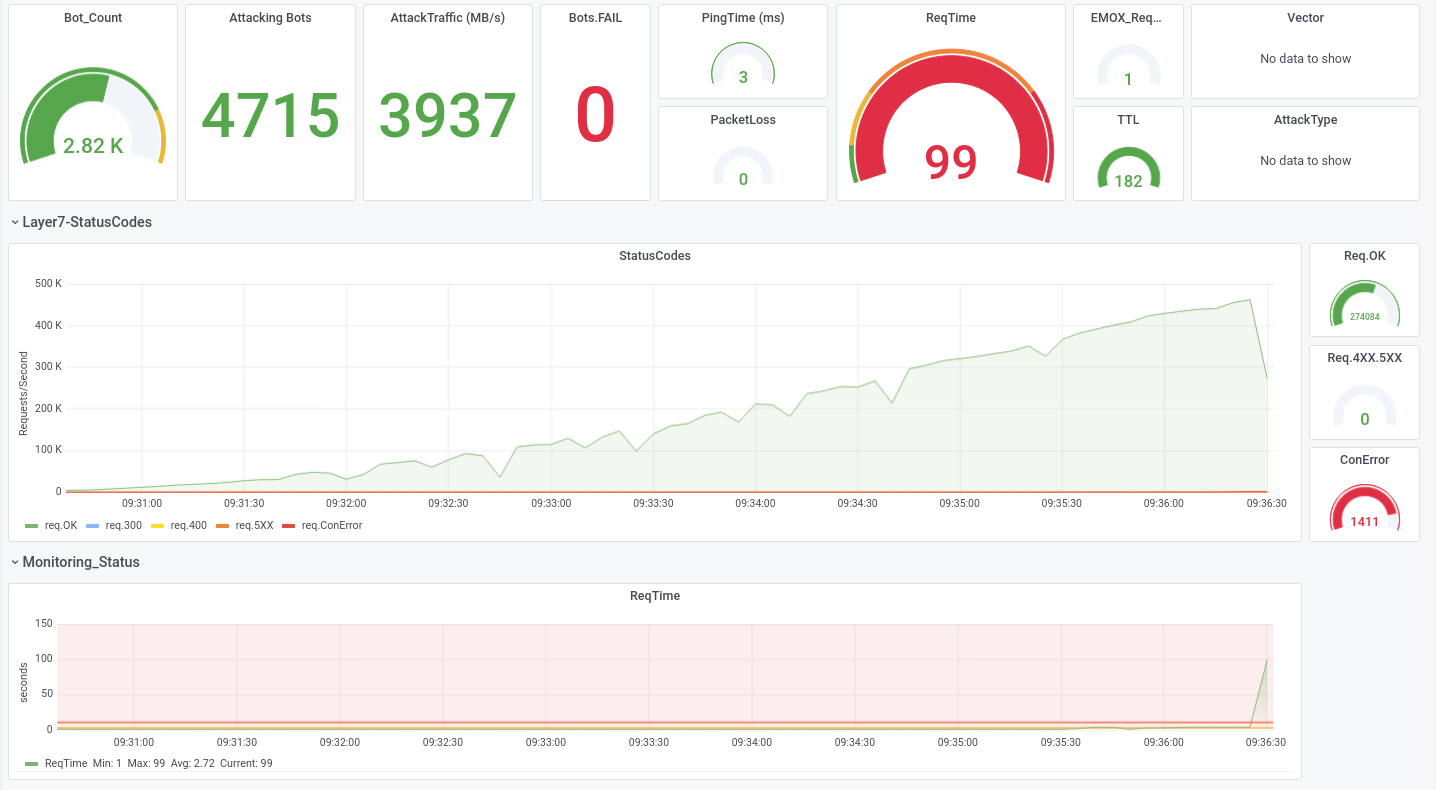
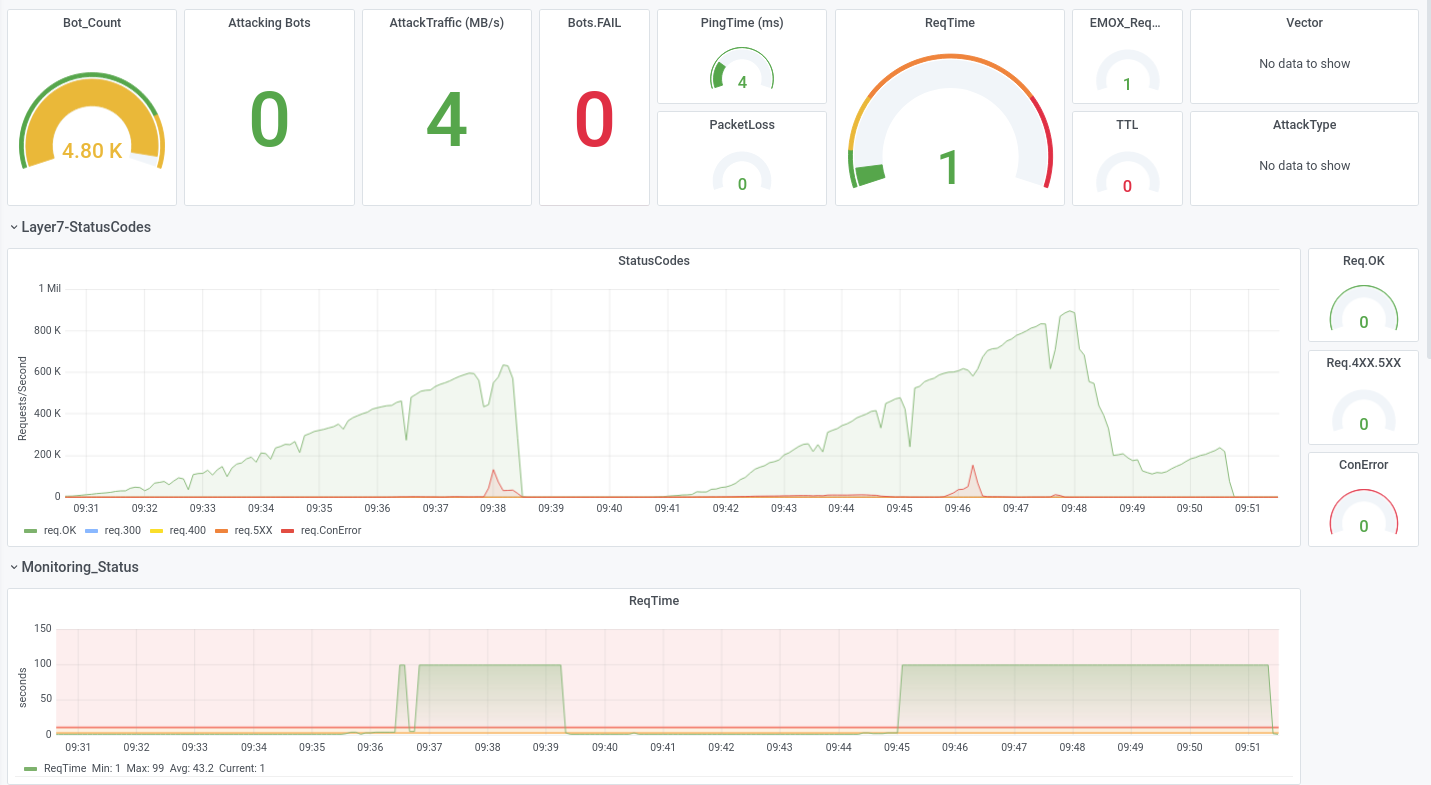
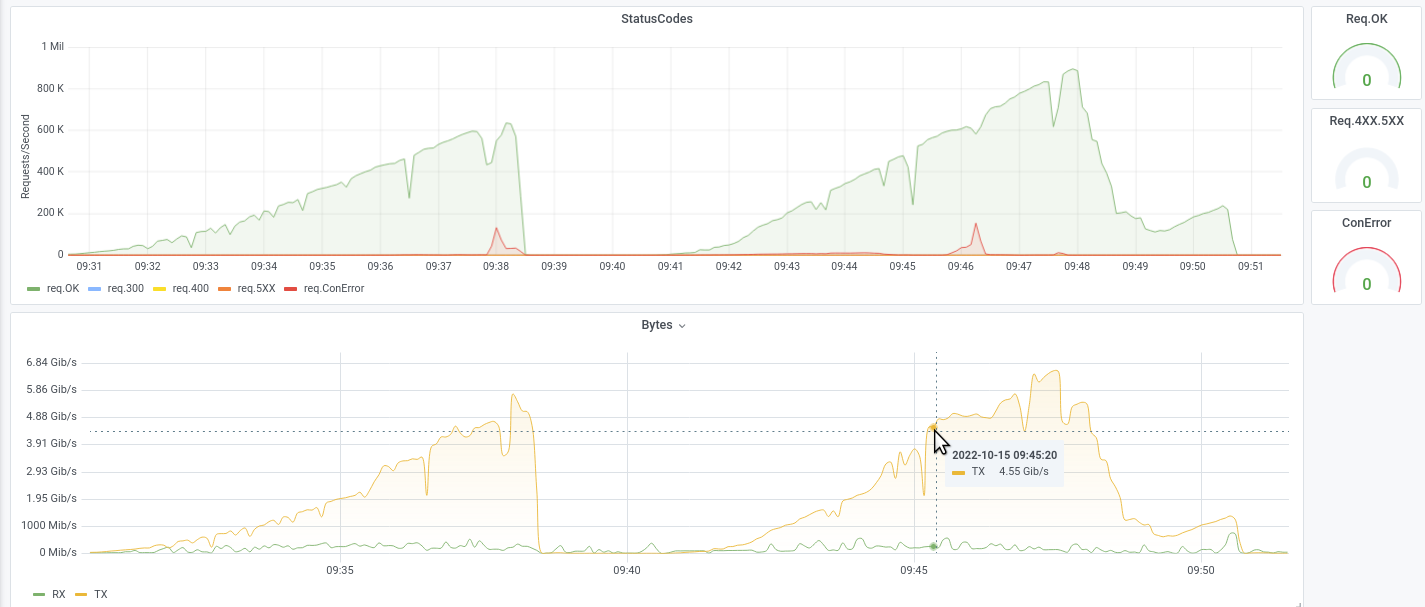
Let us show some examples from attacks we executed during DDoS-Stresstests that were successfully and could not be mitigated, while also beeing very small-scale with traffic not exceeding 300 Mbit/s