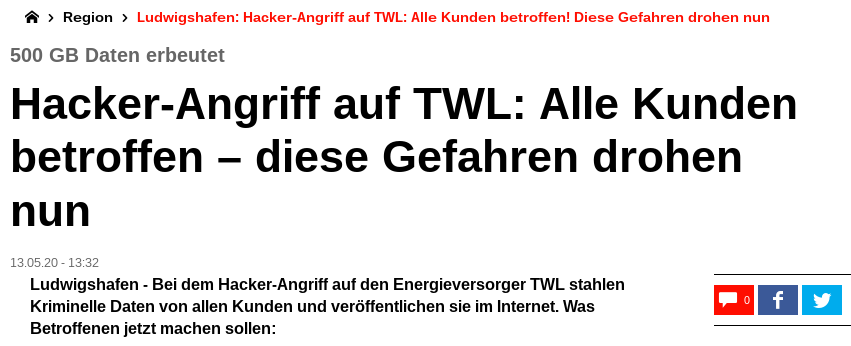
The ransomware wave, which has threatened businesses worldwide for weeks in tow with the corona chaos, is slowly reaching Cyberia Germany now; one of the first larger victims, energy provider "Technische Werke Ludwigshafen TWL" being hit on May 7, according to a report by media-outlet Heidelberg24.
Subsequent to the original ransomware attack the data were then published by Clop Group on May 11.
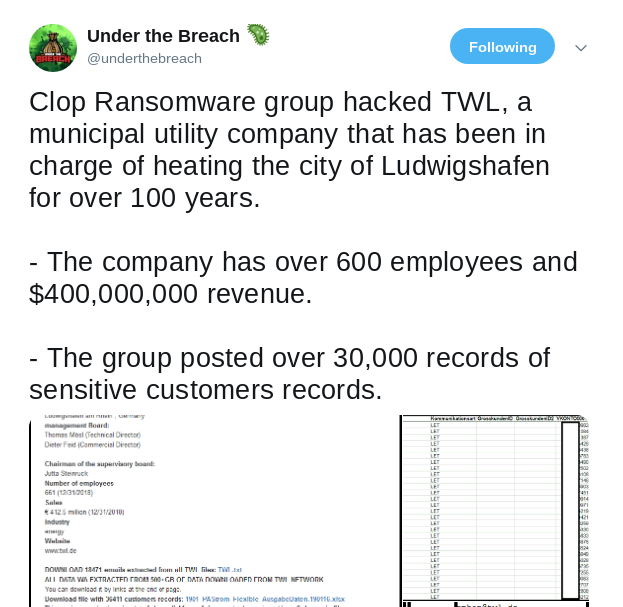
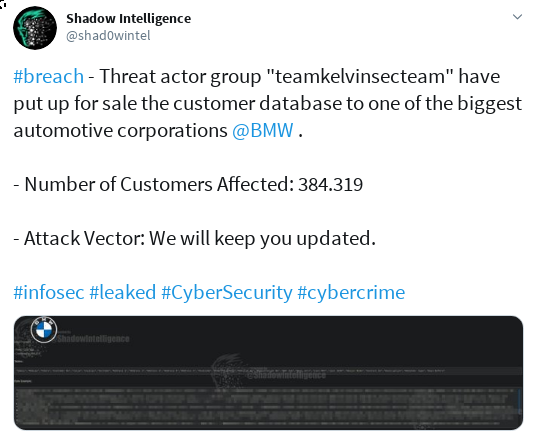
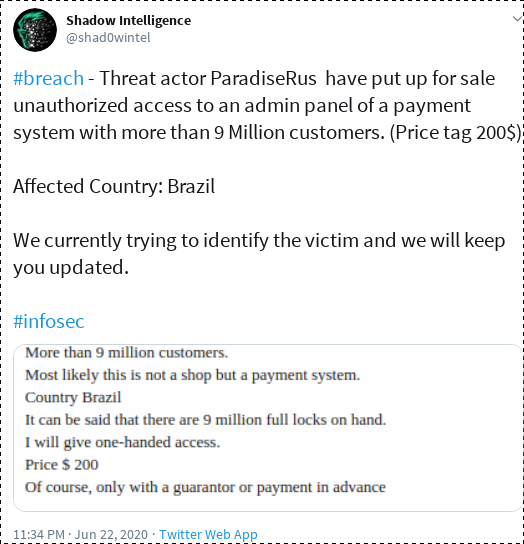
Update: the original article has been published on May 14th; 6 weeks later, at the end of June, the predictions made here are more than fulfilled, like the screenshots of leaks, breaches and accesses available for sale (BMW, LG, banks, payment providers etc ...) below are showing, which are a sampleset from the last 3 days (June 21-24, 2020) shows ; Honda had been hit in early June.
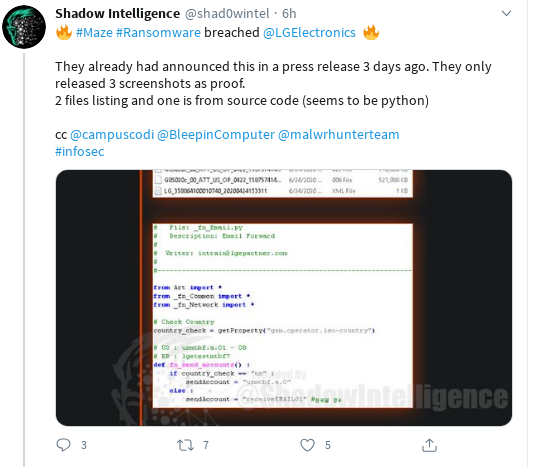
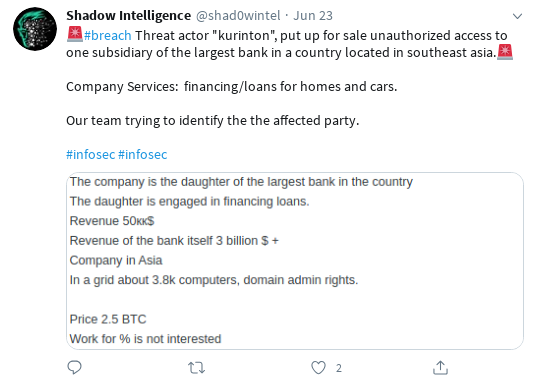
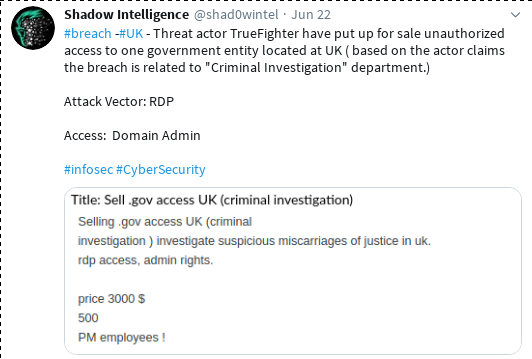
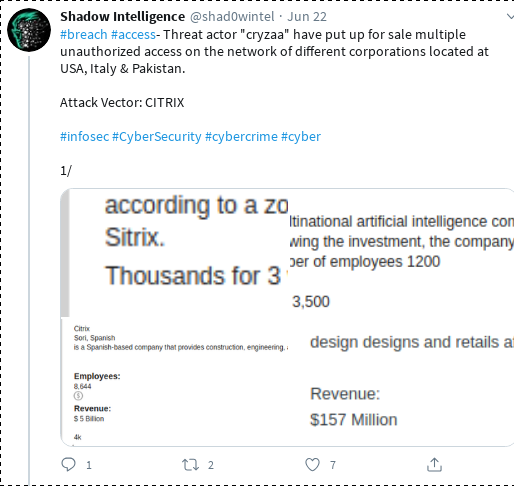
Ransomware groups attacking infrastructure directly
Besides the common attack vector via spam/malware mails a new trend has loomed since early 2020, which has been confirmed by different media and analyses: the ransomware groups are increasingly intruding networks via security gaps or via stolen/hacked RDP access, finding a variety of targets in a large number of data centers.
We are monitoring the threat situation for infrastructure operators continuously and published more Security Bulletins with critical vulnerabilities within the first months of 2020 than we previously did within a whole year, and there was about everything in it; Webservers, ApplicationServer, infrastructure tools, firewalls, VPN gateways ... a selection can be found here:
- Citrix Sharefile Data-Access
- SaltStack RCE
- Fortimail Auth-Bypass
- vCenter RCE
- HAProxy RCE
- Paessler PRTG RCE
- Exchange RCE
- Sophos Firewall RCE
- ...
Microsoft has noticed this trend as well and published it in an analysis on April 28, including a series of counter measures. ( Ransomware groups continue to target healthcare, critical services; here’s how to reduce risk )
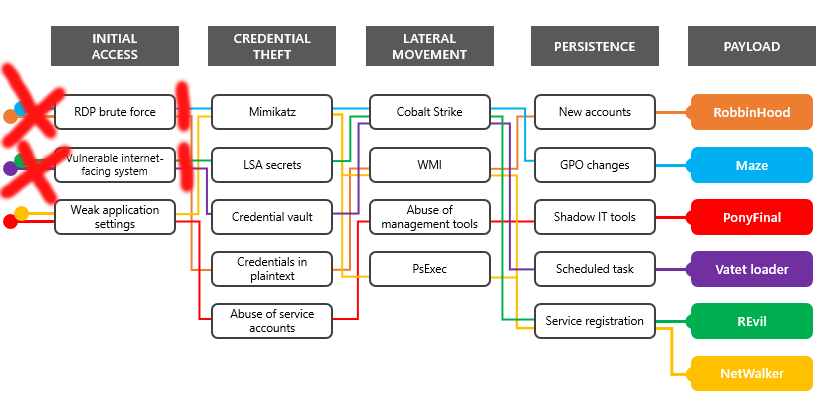
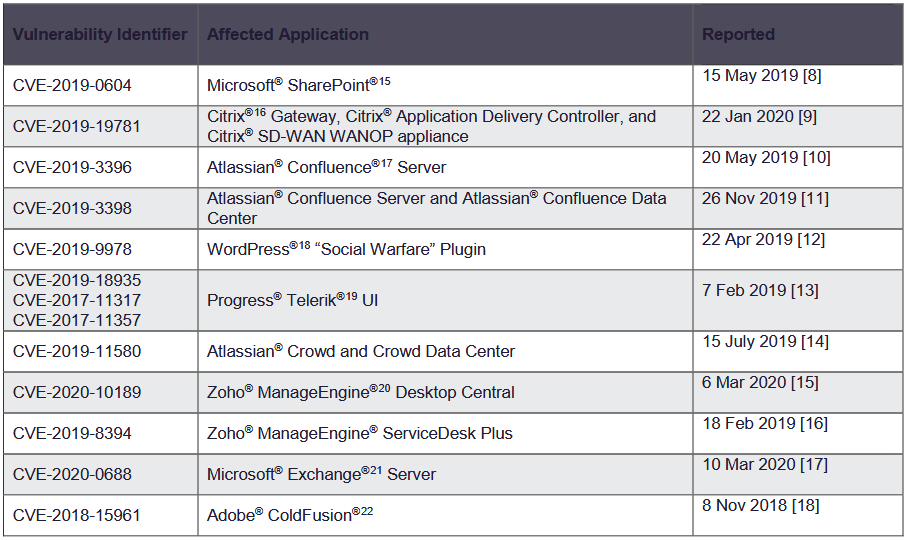
Furthermore, the NSA has published a document with an analysis of the paths attackers use to get access to networks for the purpose of performing further actions (data exfil, ransomware).
Issues can be outlined as follows:
-
At the beginning of the corona crisis many businesses acted with precipitation and either opened up RDP access outwards or made other mistakes, sometimes with fatal impact:
"Sadly we have seen some orgs drop "domain users" into their VPN groups to scale up WFH. We're discovering more valid creds during brute forcing with generic usernames such as meeting-room, conference, vendor, and other dormant but not disabled accounts."; -
Security officers/CISOs who are not familiar with the concept of "external attack surface" and who don’t question the statement of "our firewall is going to settle this" are surprised by security incidents, particularly since they lack the appropriate overviews.
-
The patchlevel is often insufficient
As a result, there is active RDP access trading on the darknet; through one of our cooperation partners, we can access a database containing current and previous access data for servers, services and systems being traded on the darknet. The database contains 2.3 M access data on 870,000 systems, with half a million added since March, which is about the same as previously within a whole year; there are 37,000 IPs for Germany; 5 systems from TWL’s network (AS 9022) are listed where access data are available on the darknet.
SUMMARY for rdp_trading_darknet
IPs : 876.249
Networks : 116.752
ASNs : 16.819
Countries : 220
Top 10 Countries
Country | Count
--------+-----------
US | 222304
CN | 139160
BR | 69952
DE | 36941
IN | 23189
GB | 20993
FR | 20175
ES | 17807
CA | 15755
IT | 15037
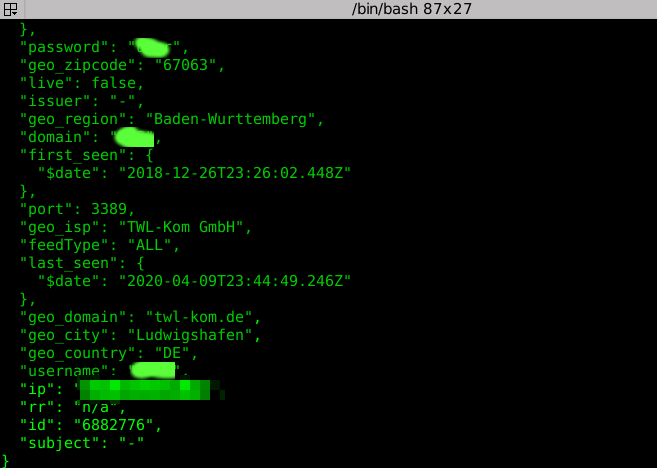
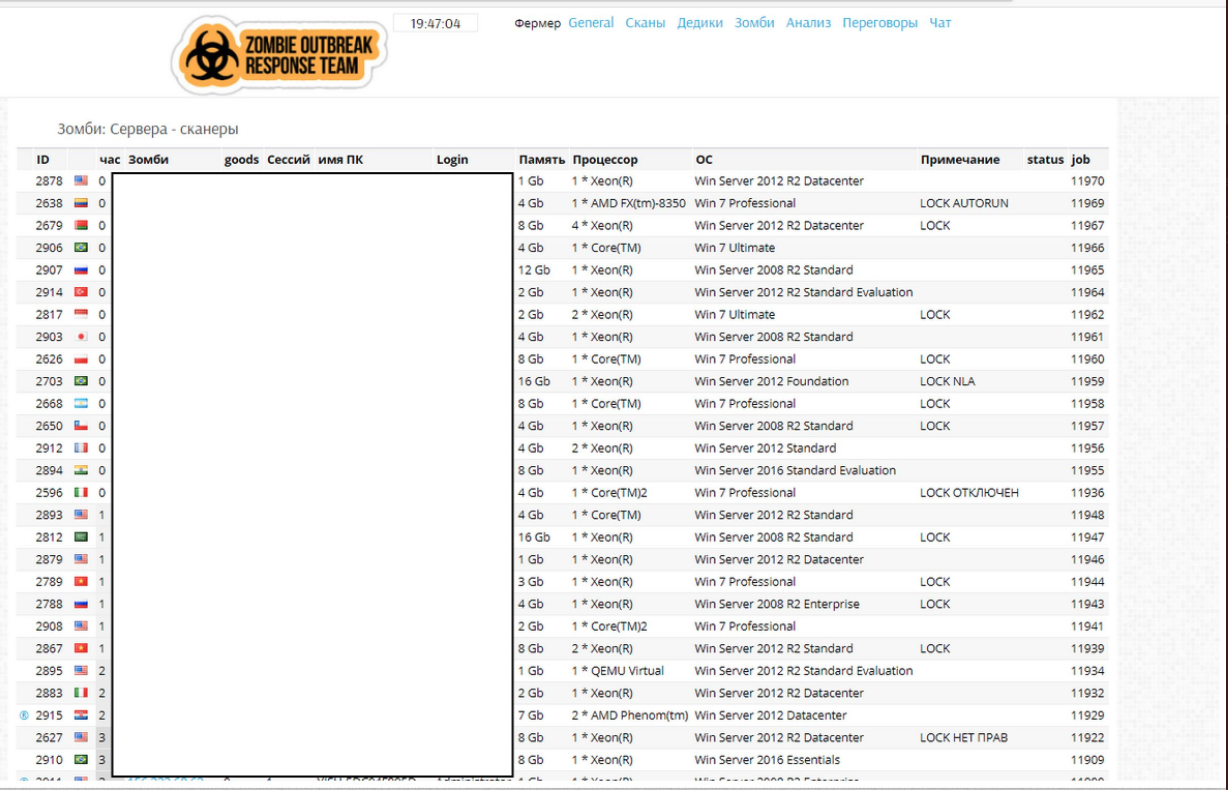
Cybercrime store sells 43,000 hacked servers, via ZDNet
Counter measures
Every IT security officer in an organization operating more than one public IP should be aware of the problem and can provide visibility -which is the base for improvement- by use of a few simple measures:
- Measuring the current external attack surface through a manual recon or an automated tool such as Luup (Asset-Discovery and Asset-Management)
- Identifying possible vulnerabilities, internal or critical systems which should not be available to the whole world
- Eliminating the attack points
- GOTO 10: continuous monitoring of the external attack surface
These simple measures, which don’t require any large new hardware, appliances or solutions investments, enable implementing quick and effective measures in order to increase security levels against external attacks significantly and to avoid being the next entry in the ransomware groups’ leak list.
Wie teils desaströs die Lage ist, haben wir in unserer Lehrlingsserie Cyberien im Winterschlaf analysiert.
In our Cyberia in Hibernation trainee series 8german only), we analyzed how disastrous the situation is to some extent.
References
- Ludwigshafen: Hacker-Angriff auf TWL betrifft ALLE Kunden – welche Gefahren jetzt drohen
- UTB: Clop Ransomware group hacked TWL
- ZDNet: NSA shares list of vulnerabilities commonly exploited to plant web shells
- Campuscodi: The list of commonly exploit vulnerabilities includes popular tools like Microsoft SharePoint, Microsoft Exchange, Citrix, Atlassian Confluence, WordPress, the Zoho ManageEngine, and Adobe ColdFusion
- Campuscodi: Ransomwaregangs goes Infra-Attacks and RDP
- nsacyber / Mitigating-Web-Shells via Github
- NSA-Report: Detect and Prevent Web Shell Malware (PDF)
- Microsoft: Ransomware groups continue to target healthcare, critical services; here’s how to reduce risk
- Microsoft: Ghost in the shell: Investigating web shell attacks
Addendum
- current figures (2020–05) of vulnerable systems with various security gaps, worldwide
--[ CVE-2020-0796 | MS SMBv3 RCE (SMBGhost) ]------------------------------
Total number of results: 130575
--[ CVE-2019-19781 | Citrix RCE (Shitrix) ]------------------------------
Total number of results: 5819
--[ CVE-2019-1653 | Cisco WAN VPN Router unauth access ]------------------------------
Total number of results: 7332
--[ CVE-2019-0708 | Windows RDP RCE (BlueKeep) ]------------------------------
Total number of results: 386229
--[ CVE-2019-11510 | PulseSecure VPN RCE ]------------------------------
Total number of results: 1226
Fragen? Kontakt: info@zero.bs
