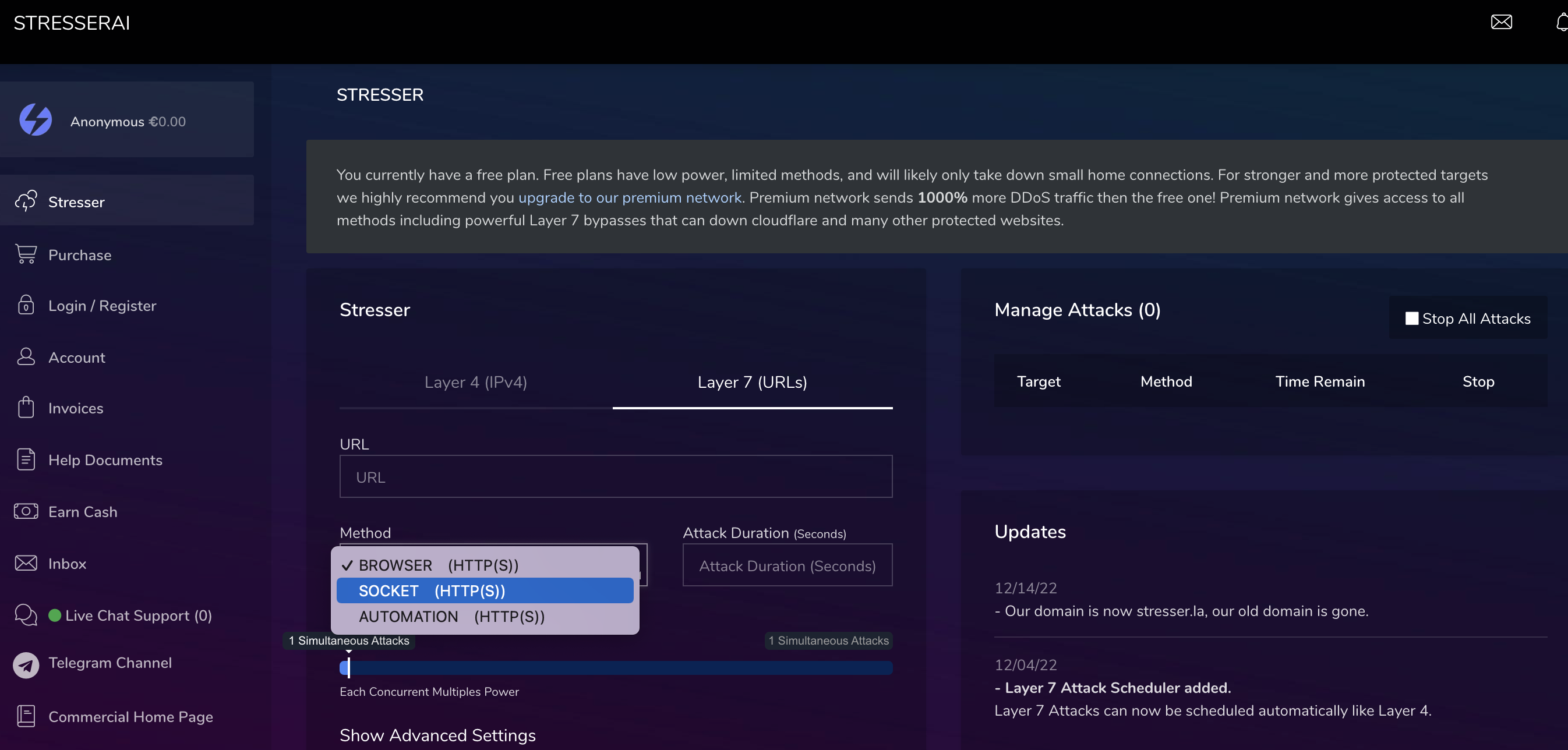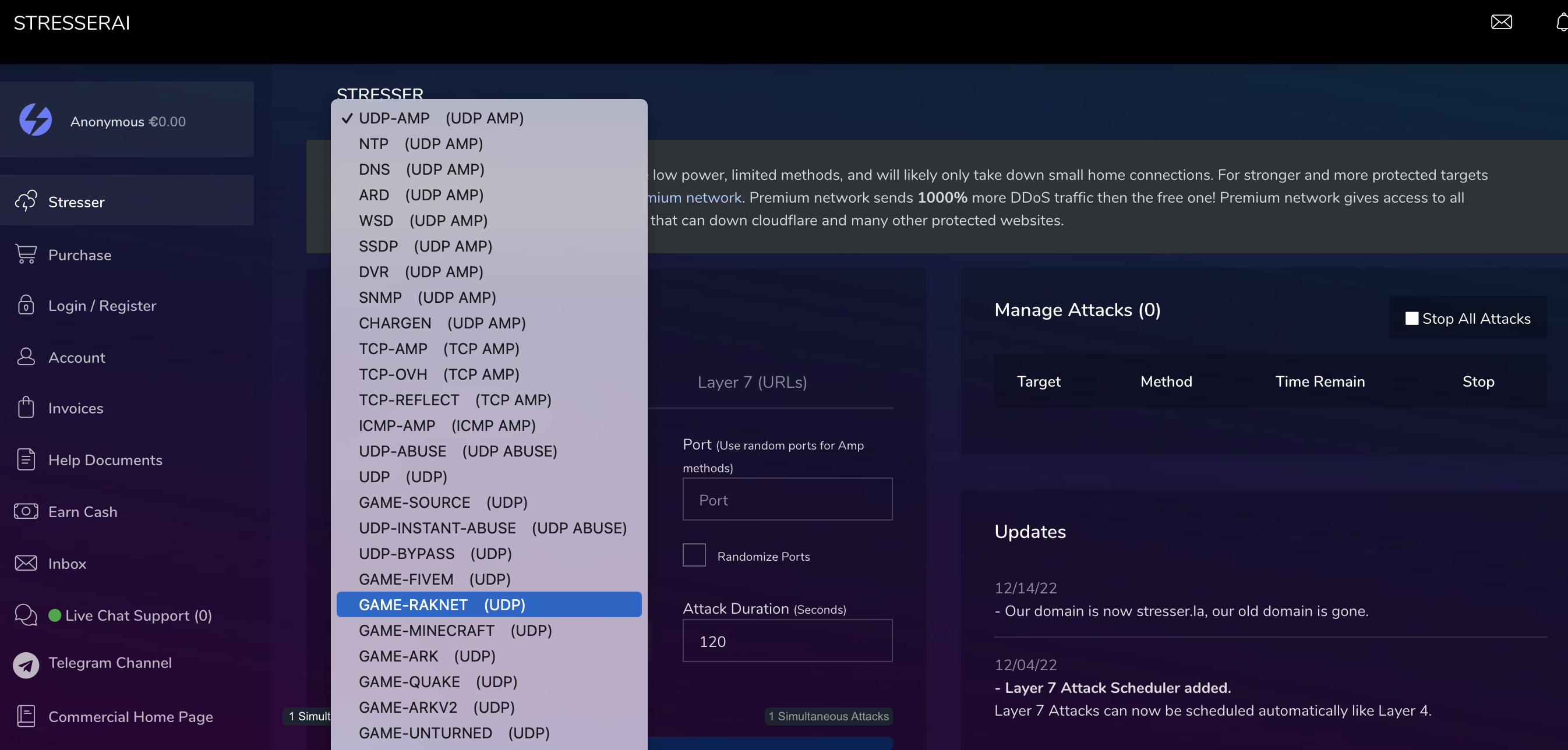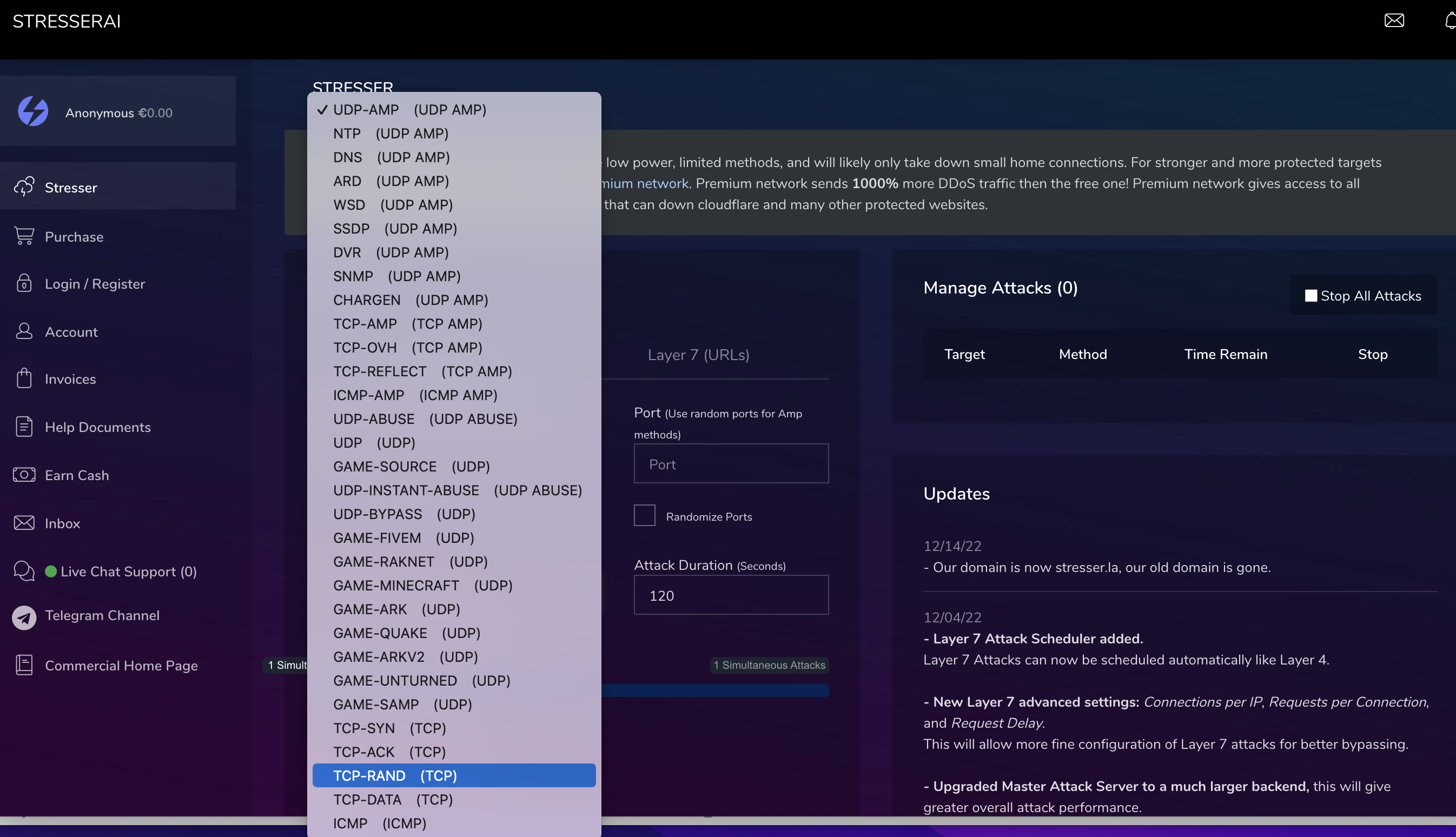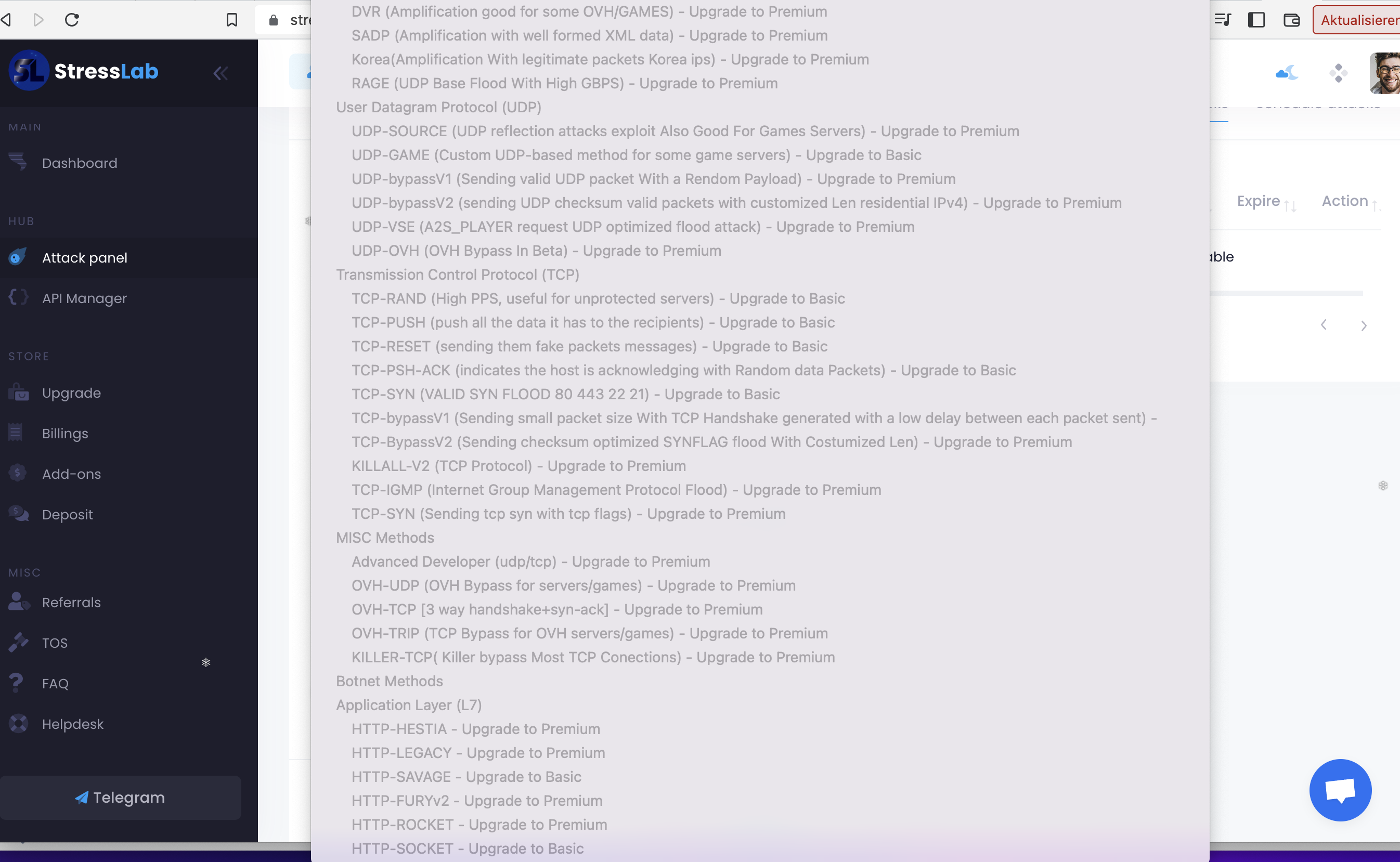
New methods and capabilities like Browser-Bots and advanced TCP-Attacks have been observed beeing available via booter-services in the last year, that have been used only by more advanced attackers.
-
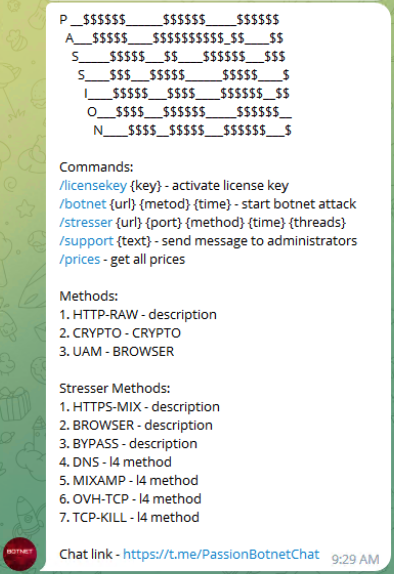
Browser-based attacks to mitigate BrowserChallenges
-
TCP Handshakes (valdi TCP-sessions, not just traffic; think "SlowLoris", just for TCP)
-
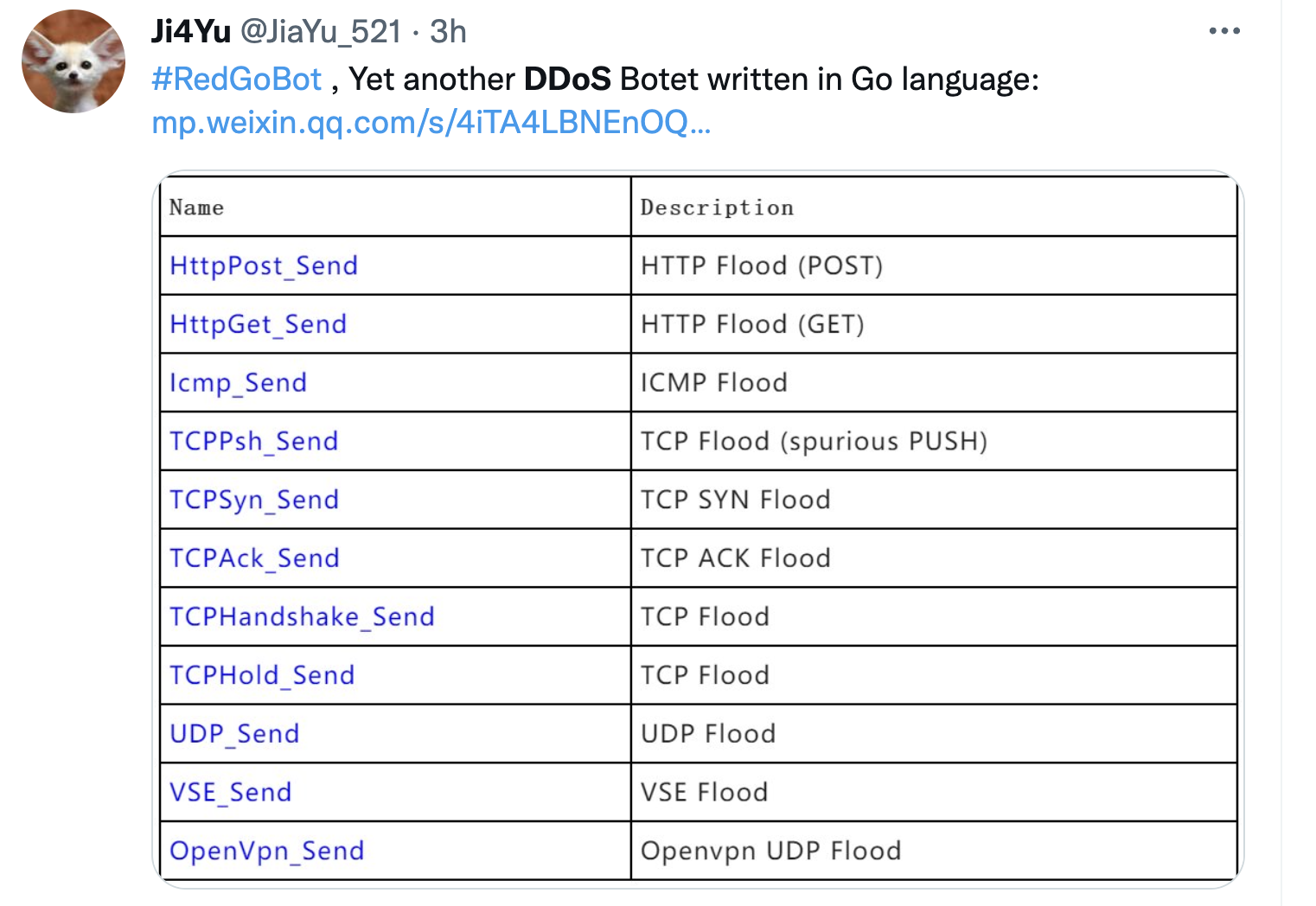
a wide range of other TCP-based attacks, which use is also reflected by a) TCP beeing the mostly-observed attackvector on network-based attacks in 2022 and b) beeing often successful and thus beeing applied by whoever executes DDoS-Attacks; we covered this developmend in our post "Smashing the Stack for fun and Profit, 2023 Edition"
We also found that a lot of Actors recently switched to Browserbots and more sophisticated attacks, with overwhelming success. Many State-of-the-Art Layer7-protection-methods rely on browserchallenges as a last-line-of-defense, and if this line is broken, the first attack-wave will be successful.
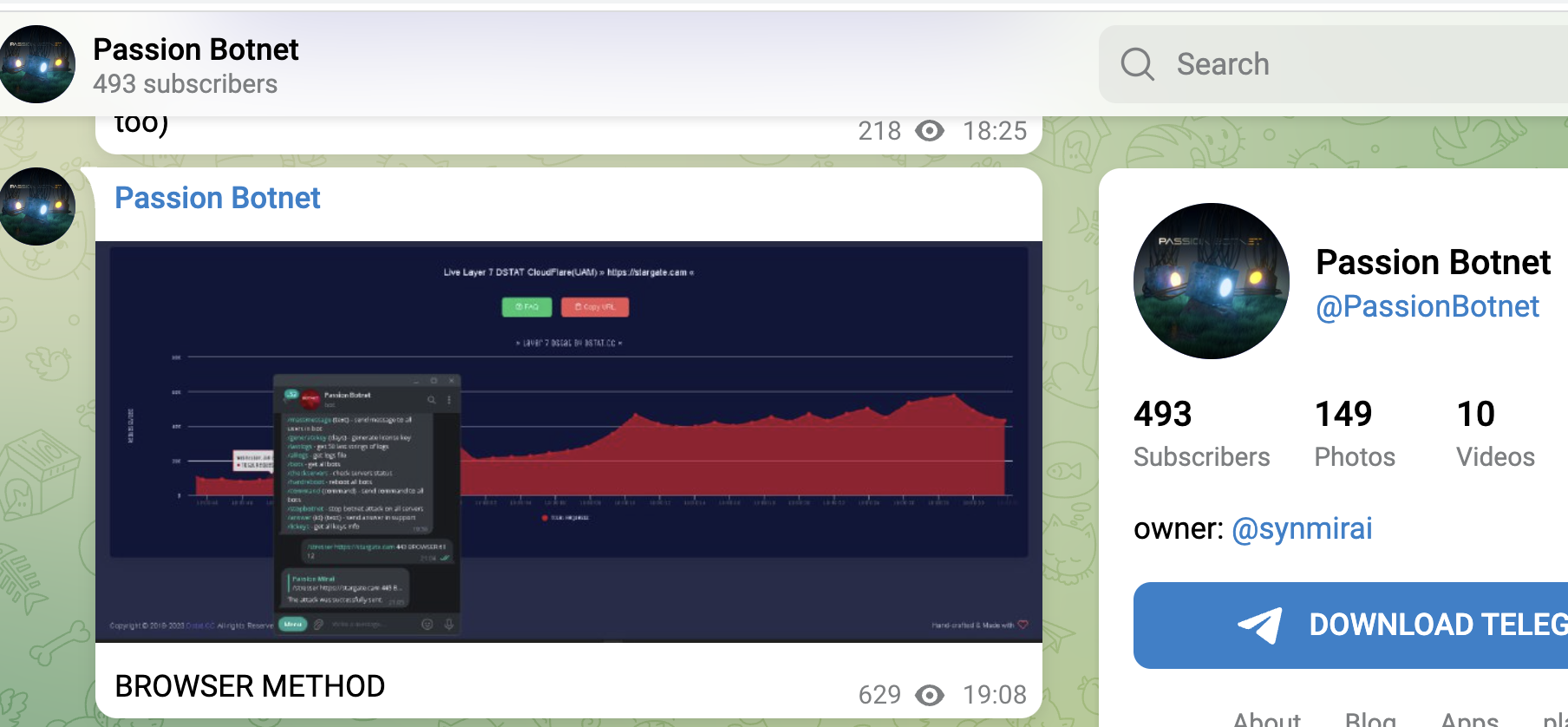
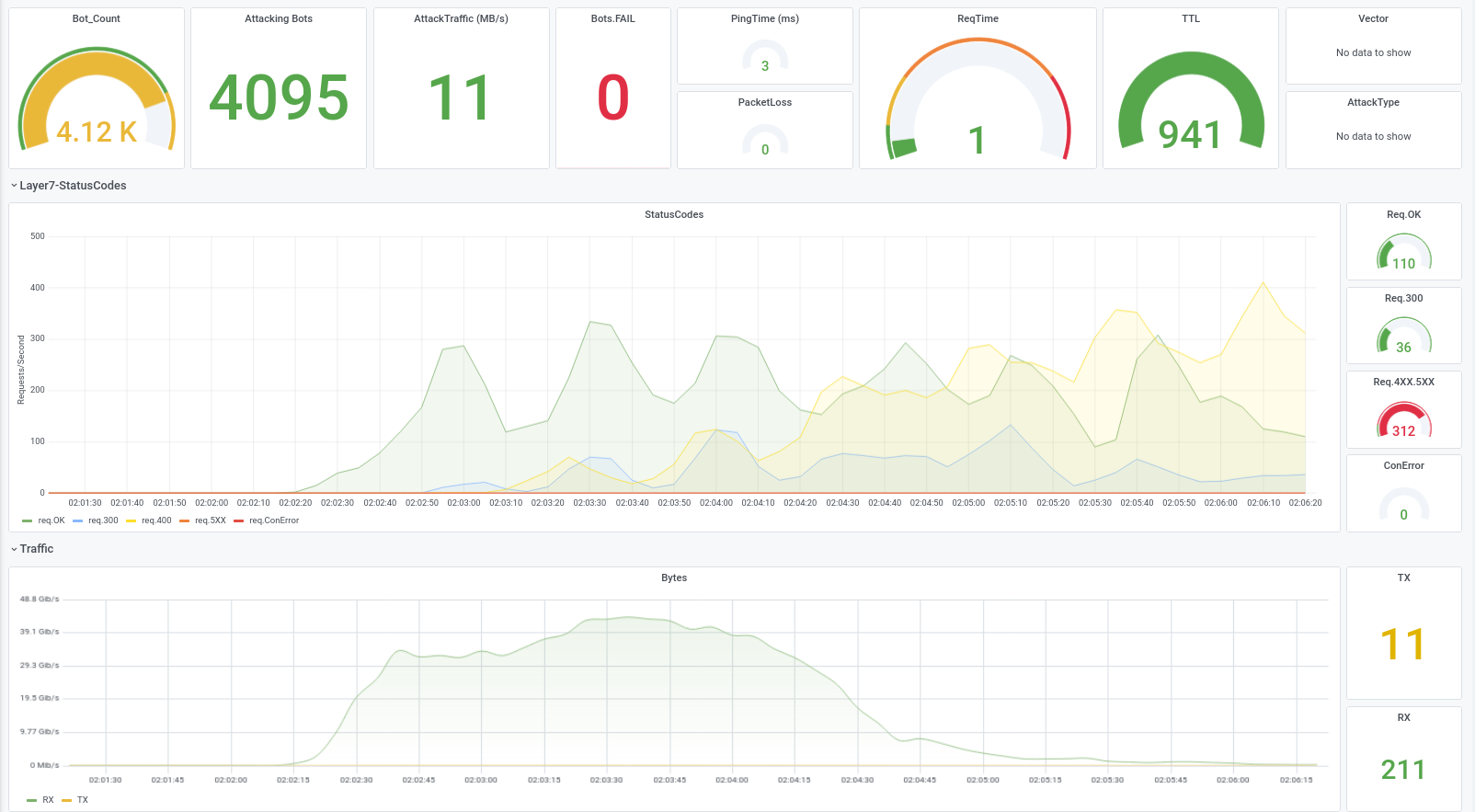
With browserattacks you'll also find different sideffects, like shown in the screenshot above. With "just" 5000 Browsers we were able to completely saturate the upstream-connection (40 GB/s traffic generated from the target outgoing), which then lead to a complete halt of all traffic.
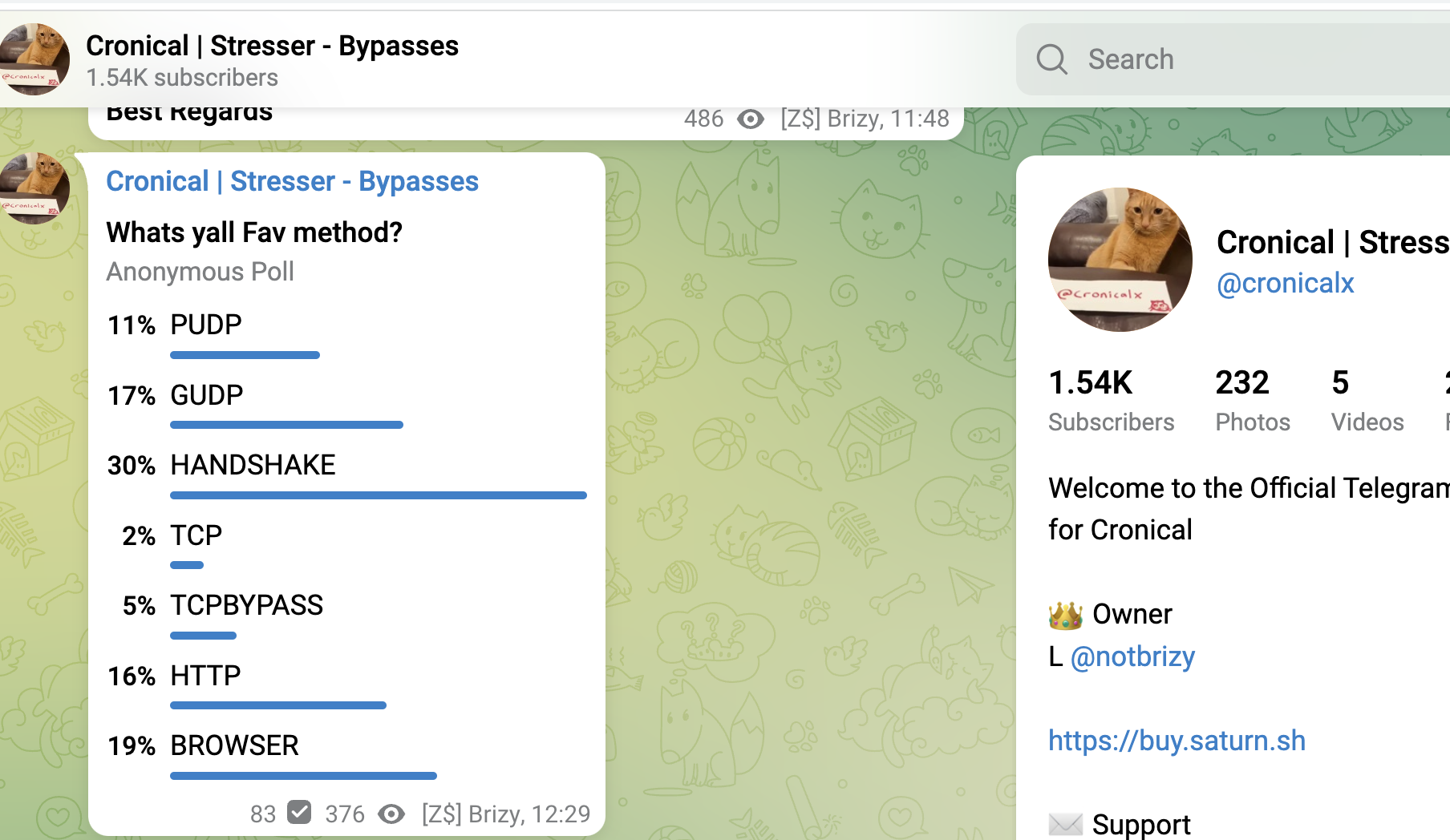
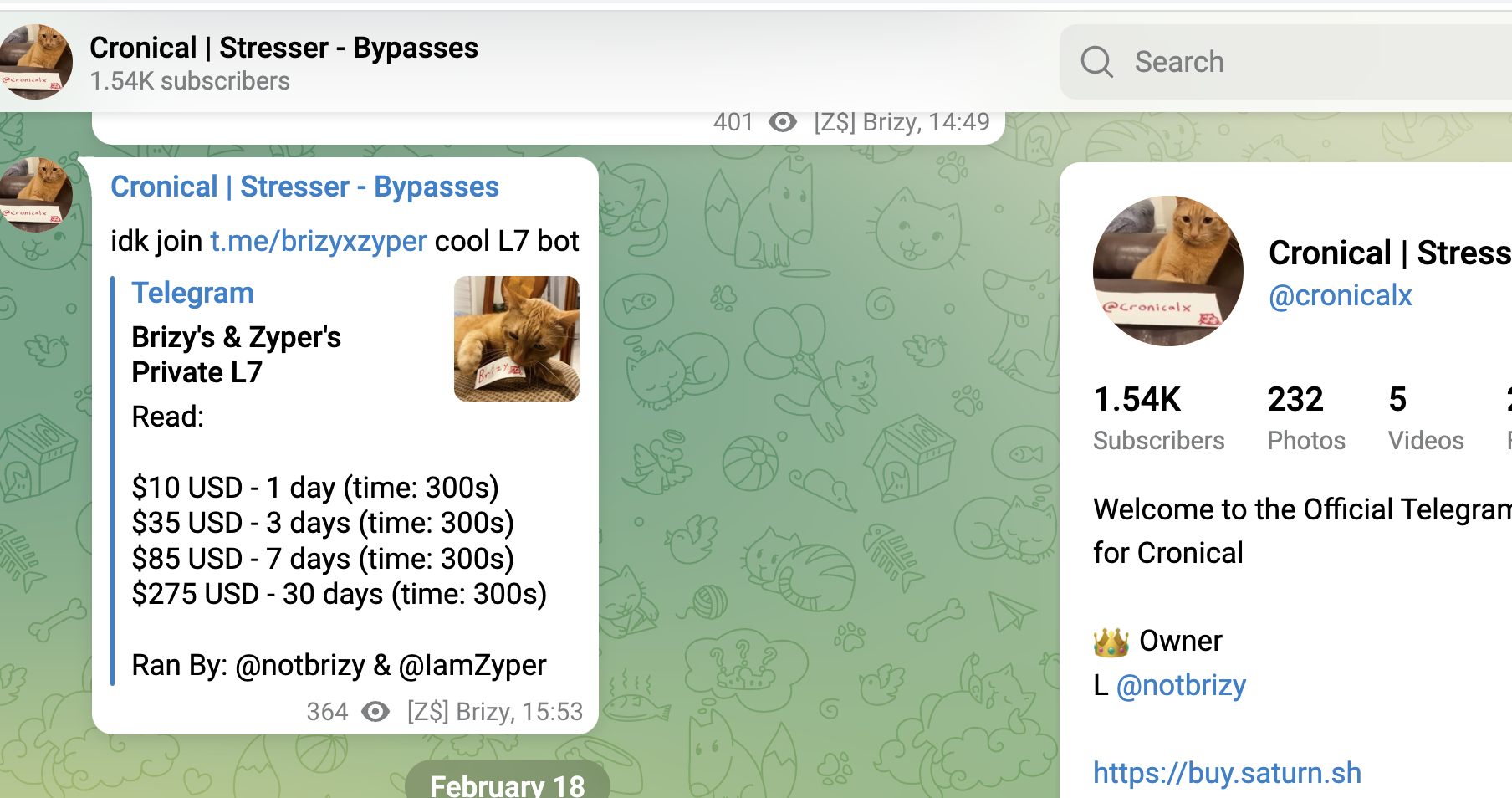
find below a couple of recent screenshots from booter-services or botnet-providers and available attack-methods
Fragen? Kontakt: info@zero.bs