Ressources and Feeds (TLP:WHITE)
- critical CVE/CVSS-Definition: AttackVector == Network AND PrivilegesRequired == None AND UserInteraction == None AND (privilege escalation OR RCE)
2020-12-14 [+]
- SolarWinds supply-chain-attack: multiple Customers hacked by infected update
- FireEye lost it's stash of RedTeam-Tools and provides a Repo with signatures to detect these
2020-12-09 [+]
- SAP NetWeaver RCE CVE-2020-26829 with a CVSS - Score of 10.0
NIST - FireEye lost it's stash of RedTeam-Tools and provides a Repo with signatures to detect these
2020-11-26 [+]
2020-11-04 [+]
- Solaris SSH 0day leaked CVE-2020-14871 / NIST / POC
- Oracle-RCE CVE-2020-14882 and POC released
- NSA publishes list of top vulnerabilities currently targeted by hackers
2020-10-16 [+]
- SonicWALL VPN RCE NIST: CVE-2020-5135, Advisory, it is said trivial to exploit, but no PoC seen so far
2020-09-30 [+]
-
WebSphere: ZDI published a blog on CVE-2020-4464: SOAP Deserialization of Untrusted Data where it states that Auth can easily bypassed by
<LoginMethod>TokenBased</LoginMethod><token>foo</token>for that attack, lifting the CVSS from 8.8 to 9.8, because PR:L changes to PR:N; expect PoCs and Exploits soon; this also gives an explanation to an answer from july -
RoundCube-Webmail has RCE and path-traversal - vulns ( CVE-2020-12640, CVE-2020-12641)
-
Rails: multiple PoCs and new details have emerged for the Rails-RCE reported in June (CVE-2020-8165), please see the following links: PoC, Details, there are also a couple of more noteworthy CVEs: (CVE-2020-8162, CVE-2020-8164, CVE-2020-8165, CVE-2020-8166, CVE-2020-8167, CVE-2020-15169
-
Zoho ManageEngine Applications Manager has multiple critical RCE-vulns ( CVE-2020-14008, CVE-2020-24786)
-
Zoho ManageEngine Exchage Reporter has a critical RCE CVE-2020-15394,
-
Kubernetes: if you run public clusters, you might want to look into CVE-2020-8559, Details; a PoC is available
-
re:Zerologon (CVE-20202-1472): for those who need to find and check more than one DomainController in their networks, we released an article (Zerologon (CVE-2020-1472) finding and checking ) with instructions how to find and scan DC for the Zerologon in larger networks
2020-09-14 [+]
-
a critical RCE vuln has been published in Mobilenron MDM, CVE-2020-15505 ;PoCs are available there is also more to this:
CVE-2020-15506 - Authentication Bypass // CVE-2020-15507 - Arbitrary File Reading
NIST/CVE-2020-15505
NIST/CVE-2020-15506
NIST/CVE-2020-15507 -
the Zerologon-dubbed NetLOGON - vuln from August-Patchday CVE-2020-1472 with CVSS of 10 has now a PoC and a Blog-Entry, giving more insights. It is HIGHLY adivsed to patch ASAP.
-
various ongoing DDoS-Attacks against ISP have been observed in early September
2020-08-31 [+]
- RCE-0day against QNAP had been seen and analyzed by netlab.360.com
- a critical NET-SNMP - vuln had been published that allows an remote attacker RCE as root. for details read this detailed analysis. so far no PoC has been seen yet
2020-08-27 [+]
- Talos reported a DOS in ISC-BIND (CVE-2020-8620), affecting versions 9.16.x - 9.17.x, 13000 installtions found online, CVSS 7.5
- Path-Traversal was reported in Icinga-Web (successor of nagios2), CVE-202-24368 / CVSS 7.5 since availability-monitoring is crucial for datacenters, this could allow to read sensitive information on the monitoring-host
- ZDI reported 2 vulnerabilities on Schneider Electric APC (CVE-2020-7521, CVE-2020-7522) that allows remote attackers to execute arbitrary code on affected installations of Schneider Electric APC UPS Online. Authentication is not required to exploit this vulnerability, both rated with CVSS of 9.8 ZDI-20-1006 | ZDI-20-1007
- SNMPTT before 1.4.2 allows attackers to execute shell code via EXEC, PREXEC, or unknown_trap_exec (CVE-2020-24361, CVSS 9.8
2020-08-20 [+]
- Nexus Repository Manager from Sonatype has an Auth-Bypass (CVE-2020-15868, CVSS 7.5); Advisory | NIST
-
Zoho ManageEngine ADSelfService has a priviledge Escalation again CVE-2020-11552, CVSS 9.8, and POCs already circulating
-
Horde, a popular Webmail-Frontend, had a RCE-0day published as well, with Advisory on ZDI and a working-POC
-
the Microsoft- Netlogon-Vuln (CVE-2020-1472) is still in discussion, see here
-
Cisco released multiple Advisories
- Cisco vWAAS for Cisco ENCS 5400-W Series and CSP 5000-W Series Default Credentials Vulnerability | CVE-2020-3446
- Cisco Video Surveillance 8000 Series IP Cameras Cisco Discovery Protocol Remote Code Execution | CVE-2020-3507
- Cisco Smart Software Manager On-Prem Privilege Escalation Vulnerability | CVE-2020-3443
-
Blackberry QNX Software Development Platform version 6.4 to 6.6 has an RCE (see Advisory or NIST CVE-2020-6932), CVSS 9.8
2020-08-11 [+]
-
Citrix again []https://www.bleepingcomputer.com/news/security/citrix-fixes-critical-bugs-allowing-takeover-of-xenmobile-servers/
-
vbulletin had a 0day-published, obviously a non-complete patch for CVE-2019-16759, Update: CVE-2020-17496 was assigned a week later with a CVSS - Score of 9.8
2020-08-05 [+]
- a hacker has leaked access for 900+ enterprise VPN servers
2020-07-31 [+]
-
Cisco released multiple critical advisories for its Data Center Network Manager (Auth-Bypass, CommandInjection/RCE) and SD-WAN vManage - products / / a blogpost on these issues had been releases as well, but no PoC so far
-
Dells released an Advisory with a PathTraversal in iDRAC: "A remote authenticated malicious user with low privileges could potentially exploit this vulnerability by manipulating input parameters to gain unauthorized read access to the arbitrary files. PTSecurity has a Blogpost on that issue
-
IBM WebSphere has a critical vuln, which was reported by ZDI with CVSS 9.8, but got a 8.8 from IBM itself; ZDI's statement on Twitter:
Auth required but can be bypassed easily. Maybe there should have been a separate CVE for the auth bypass but there isn't.
-
Claroty found a couple of vulns in VPN-products like Secomea GateManager (CVE-2020-14500, CVE-2020-14510 ) + Moxa Industrial VPN-Gateways
-
Swithak released an excellent summary of GRUB2-Vulnerability (BootHole)
2020-07-24 [+]
- Cisco ASA WebVPN FileRead - Vulnerability (CVE-2020-3452)
lets attackers read sensitive files on a targeted system. currently not 100% sure about the sensivity
of these files (VPN-session info or not), but expect the worst
various POCs had been put out immediatly after release of the advisory, so better patch
2020-07-20 [+]
- July Patch Priorities - List by Swithak
Oracle July Patchday cummulated summary
- Multiple CVSS 10.0 und countless 9.8 across all Oracle - Products, check yourself if you are affected, this covers only the most widespread aplications and implementations
-
Oracle WebLogic Application-Server has multiple serious vulns with CVSS 9.8 in 3rd-party-libs and the Core (CVE-2020-9546, CVE-2018-11058, CVE-2020-14625, CVE-2020-14644, CVE-2020-14645, CVE-2020-14687, CVE-2017-5645, CVE-2017-5645), 15.000 IPs affected CVE-2020-14645 is likely to be exploited soon as it is just another try from oracle to circumvent old vulnerabilities that we followed since long time: CVE-2020-2555 bypass > CVE-2020-2883 bypass > CVE-2020-14645
-
Oracle WebCenter Portal has an easy to abuse XML/XE-vuln in a 3rd-party-lib ( CVE-2019-17531)
- Oracle SD-WAN has 2 x 10.0 CVE-2020-14701 and CVE-2020-14606
- SAP like: Hold My Beer! and scores a 10.0 as well with SAP Netweaver RCE / CVE-2020-6287 , a POC is available
2020-07-15 [+] (cummulated Summary)
- July Patch Priorities - List by Swithak
Windows Server DNS RCE (CVE-2020-1350
- Mitigate, Test, Patch
- exploits expected soon
- NOT a single-request-RCE, so probably not exploitable by a single Email/Phish
- References:
Oracle Cummulative Summary Jul 2020
not good SNR:
- CVE-2020-14606 / 10.0 RCE Oracle SD-WAN
- CVE-2020-14701 / 10.0 RCE Oracle SD-WAN
- CVE-2020-14705 / 9.6 RCE in Oracle GoldenGate
2020-07-09 [+]
- PaloAlto/PAN-OS: OS command injection vulnerability in GlobalProtect Portal
CVE-2020-2034 with CVSS 8.1 (assuming Complexity:HIGH)
a nice version-scanner is available - F5 withdraw mitigation-suggestions for their TMUI RCE vulnerability CVE-2020-5902 and urges you to either upgrade or shutdown TMUI-access
2020-07-08 [+]
- Critical Citrix-ADC/Gateway-vuln (CVE-2020-8193)
- bypass for the inital mitigation in F5 / BigIPs Management-Interface - Vuln (CVE-2020-5092), seen by NCCGroup in the wild
2020-07-03 [+]
- Multiple Backdoors and critical vulns found in Cisco-Appliances
- RCE (CVSS 10.0) in F5 / BigIPs Management-Interface) with 8.500 devices exposed online
- PaloAlto has a critical RCE in its VPN/Firewalls, if SAML is used
- RCE in Cisco Telnetd (CVE-2020-10188) puts 137.000 installations risk
- CentOS WebPanel (CWP) has 20+ RCE and SQLi- Vulns published by ZDI (CVSS >= 9.8); there are so many, that linking one is not sufficient; please use the search-function with "centos" in the ZDI Advisory page
2020-06-24 [+]
- Sophos XG-Firewalls: Potential RCE through heap overflow in awarrensmtp (CVE-2020-11503) / CVSS: 9.8
- we see a crazy uptick in ransomware/dataleak-announcements and access to be sold on the darknet; still not yet sure if it is a real uptick or just more visibility
- Schneider Electric issued an advisory with Ripple-affected devices, namely lots of SCADA/IndustrialControll-Devices and APC/UPS - powersupply.
- Alias Robotics issued multiple advisories on their MiR-products
- Ruby on Rails has a nice RCE/CVSS 9.8 in one of their parsers (yes, again)
2020-06-10 [+]
- some new critical CVEs after Microsoft-Patchday and ZDI-Publications
- WebSphere from IBM has 2 RCE with CVSS of 9.8 announced by ZDI: CVE-2020-4450 and CVE-2020-4448
- ZecOPS claims that CVE-2020-1206, which allows reading parts of memory and was dubbed "SMBleed", can be chained with SMBGhost to pre-Auth-RCE; a POC was released and other POCS that claim to have RCE-capabilites emerged as well
- CVE-2020-1301 SMBv1 RCE is Post-Auth
- various SharePoint-RCEs, but Post-Auth, like CVE-2020-1181
- UPNP has a protocol-vulnerability CallStranger, CVE-2020-12695 that allows to be misused for TCP-DDoS Reflection/Amplification
- Intel-Processors have a new vulnerability called CROSSTalk; you can read a breakdown here
2020-06-04 [+]
- some new critical CVEs
- Grafana has a pre-auth-SSRF that might lead to RCE (CVE-2020-13379); 60k instances to be found online, see our Bulletin SB 20.20 on this issue
- "Ignition" from Inductive Automation, which is used in energy/critical manufacturing industries, has multiple serious RCE - vulns with CVSS 9.8 (CVE-2020-10644, CVE-2020-12000 )
- Cisco released advisories with critical vulns in IOS for Industrial Routers and IOx
- VMWare vCloud-Director post-auth-RCE (CVE-2020-3956) has a nice writeup/PoC and exploits released)
- OpenSSH will deprecate SSH-Keys based on RSA
- Cisco had been hacked by the Salt-Vuln mentioned roughly a month ago
Update:
- grafana-writeup published 2020-08-10
2020-05-26 [+]
- some new critical CVEs
- MariaDB has a possible RCE (CVE-2020-13249, see our Bulletin here); we expect a PoC very soon
- RangeAMP: a new DDoS-Attack against CDNs had been published that leverages HTTP Reflection AND Amplification, misusing CDNs; we are looking into that, since our DDoS-Team already has some CDN-Reflection-Attacks in use (mostly successfull)
2020-05-20 [+]
- some new critical CVEs
- a new attackvector against DNS-Servers has been published as NXNSAttack,
tl;dr: easy way to take down DNS-resolvers by spamming with many NXDOMAIN entries, this amplifies and stresses existing nameservers
updates for existing popular resolvers are distributed (ISC Bind, Unbound, PowerDNS) - RubyOnRails' "actionpack_page-caching", which was per default included in Rails-Core until 4.0,
has a critical vuln that allows an attacker to write arbitrary files to a web server, leading to potential RCE;
CVSS 9.8, CVE-2020-8159 - proxygen by facebook: A use-after-free is possible due to an error in lifetime management in the request adaptor when a malicious client invokes request error handling in a specific sequence;
CVSS 9.8, CVE-2020-1897 - we are waiting for some serious vulns with CVSS 9.8 from centos webpanel that are announced on ZDI for 2020-05-27
2020-05-14 [+]
- many new critical CVEs, due to MS Patchday
- rumours thickens that there is a new UnAuth RCE against SMB; we already mentioned it in late April, but now it it seems we are only one Patchday from a PoC and a new SMB-Worm away (WannaBlue? BlueCry?)
-
Sharepoint has a couple of Post-Auth - Low-Complexity-Vulns, which might be exploited easily once you have valid creds
- CVE-2020-1069
- CVE-2020-1102
- CVE-2020-1024
- CVE-2020-1023
- remember, trivial PoCs for similar low-complexity vulns are already released, and Sharepoint beeing one of the main target for automated exploitation
-
for some of the vulns reported last month we see PoCs emerging, so expect some fallout from this:
- people running the PiHole-Version with blocklists from this group should check out this exploits against PiHole
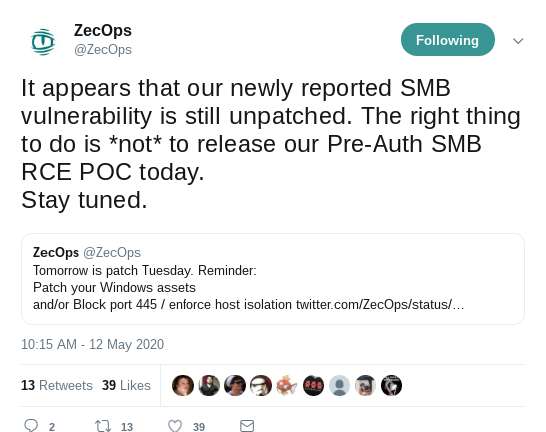
2020-05-07 [+]
- 98 new CVEs, a couple of them critical
- Cisco had patchday and released
a couple of CVEs released with CVSS > 9; we're still investigating impact, but here is a couple of interesting unauth-vulns (all DoS-related skipped)
- CVE-2020-3125 Cisco Adaptive Security Appliance Software Kerberos Authentication Bypass Vulnerability
- CVE-2020-3259 Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software Web Services Information Disclosure Vulnerability
- CVE-2020-3187 Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software Web Services Path Traversal Vulnerability
- Microsoft apparently lost some source-code
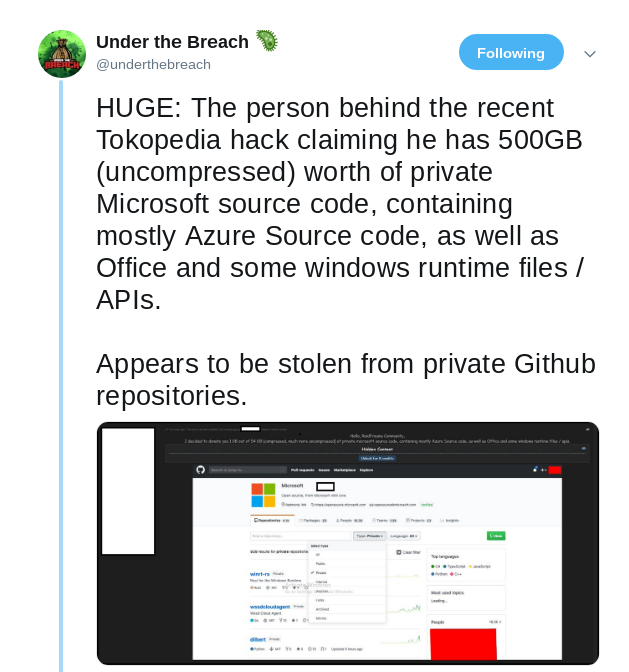
2020-05-06 [+]
- 31 new CVEs, none critical
- Citrix ShareFile has some Unauth-RCE and Unauth - Data-Access, read our Bulletin: [SB 20.17] RCE and unauthorized Access on Citrix ShareFile Storage-Appliances (CVE-2020-8982)
2020-05-05 [+]
- 38 new CVEs, none critical
- we published a Bulletin for that SaltStack-Vuln (CVE-2020-11651) which found DigiCert, Ghost-Platform and LineageOS hacked after 24hrs; probably many more as well.
2020-05-04 [+]
- XXX new CVEs, some to be analyzed
- F-Secure released an advisory with some critical SALTSTACK-Vulns (CVE-2020-11651) that may allow attackers access data on the saltstack-master
- ZDI released "CVE-2020-0932: Remote Code Execution on Microsoft SharePoint Using TypeConverters" with a detailed description of an RCE-bug in Sharepoint (CVE-2020-0932)
- a couple of BIG-IP/BIG-IQ - Advisories released last friday
2020-04-29 [+]
- 51 new CVEs, none critical
- Fortinet finally released PSIRT-Note and CVE-Details for the vuln/issue we mentioned last week; still no CVSS though, but expect this >= 9.0, given the overhasty release
2020-04-28 [+]
- 51 new CVEs, none critical
- Fortinet finally released PSIRT-Note and CVE-Details for the vuln/issue we mentioned last week; still no CVSS though, but expect this >= 9.0, given the overhasty release
2020-04-27 [+]
- 121 new CVEs since last Thursday, 2 critical
- Sophos reported and investigated
an issue/unathorized data_access with their firewalls:
The data ... may include usernames and hashed passwords for the local device admin(s), portal admins, and user accounts, but no LDPA/AD-Credentials - HP reported an issue with HPE UIoT, we are still investigating a possible AttackSurface
2020-04-24 [+]
- 92 new CVEs, 1 critical
- FortiMail/FortiVoice seems to have a serious issue; please check our Bulletin SB 20.13
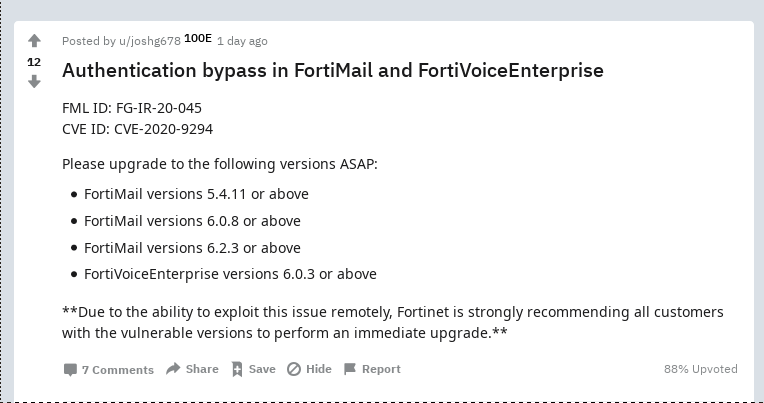
2020-04-23 [+]
- 120 new CVEs, 1 critical
- SysAid on_premise has a bug_chain that allows RCE, a POC is available
- that SMBv3 - vuln (SMBGhost) with possible RCE is still under investigation (see msgs from yesterday)
2020-04-22 [+]
- 42 new CVEs, none critical
- yesterday was the day of 0-day, YaY!, and a couple of POCs emerged as well
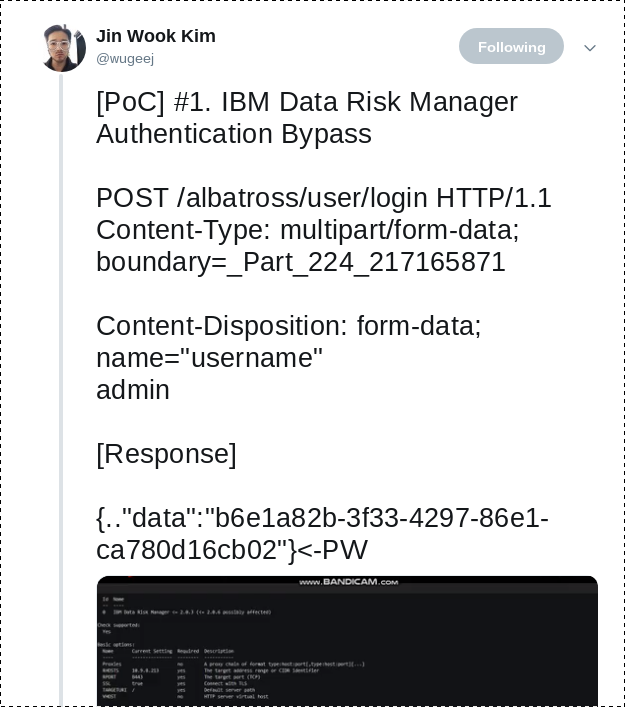
- Pedro Ribeiro: "I am disclosing four 0day for IBM Data Risk Manager"
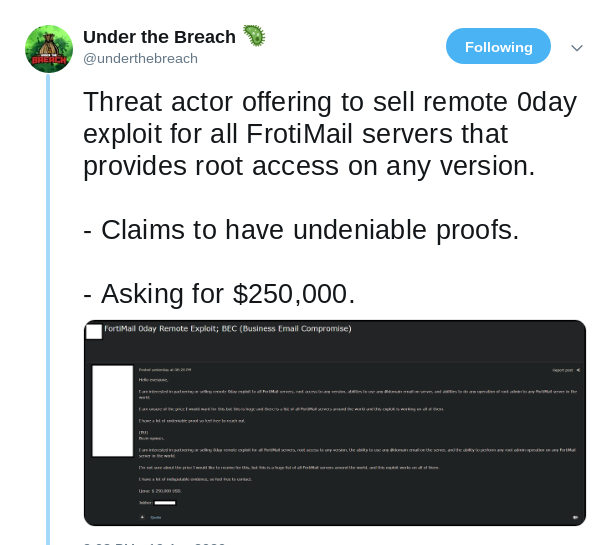
- Under The Breach: "Threat actor offering to sell remote 0day exploit for all FrotiMail servers that provides root access on any version."
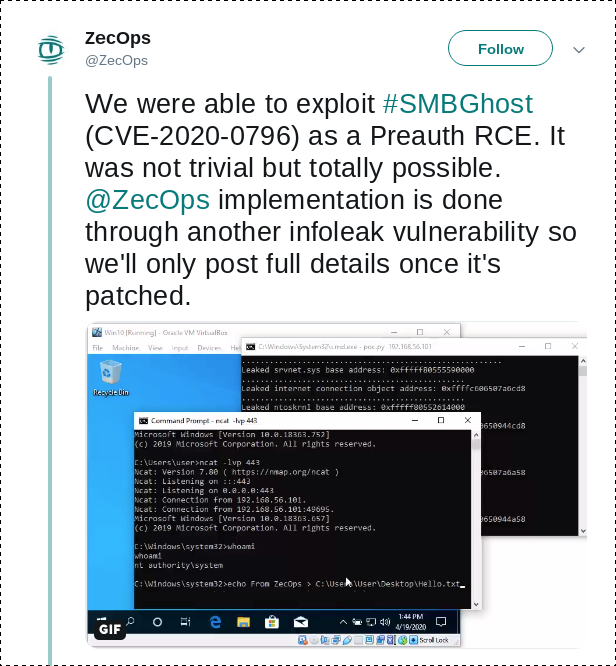
- ZecOps: "We were able to exploit #SMBGhost (CVE-2020-0796) as a Preauth RCE. It was not trivial but totally possible."
- Jin Wook Kim: "[PoC] #1. IBM Data Risk Manager Authentication Bypass"
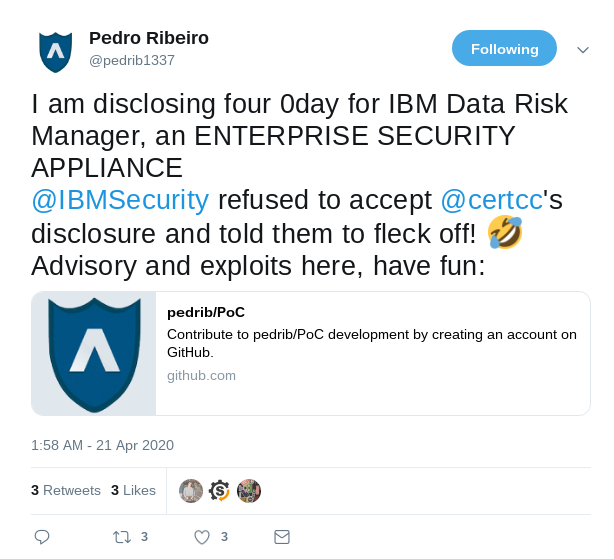
2020-04-21 [+]
- 51 new CVEs, none critical
- HAPRoxy-RCE (CVE-2020-11100): a public POC came out
for the latest HAPRoxy-RCE, announced
2020-04-04
direct link to Project Zero Advisory - SMBGhost (CVE-2020-0796): a non_public POC with a possible RCE came out for a vuln in SMB, reported by Microsoft 2020-03-12
2020-04-20 [+]
- 78 new CVEs over the weekend, nothing critical so far
- it seems that the Nexus Repo-Manager-Vuln from 12 days ago, which was stated "post_auth" in the advisory, is possible pre_auth, according to a statement from Rahul Maini
- someone claims to have a 0day for FortiMail
2020-04-18 [+]
- uncounted new CVEs since 2020-04-14, due to Patchdays from Microsoft, Oracle and Cisco, multiple critical, so this summary is splitted into various parts
- re: VMware vCenter: POC-Code has emerged that allows access to /creation of Admin-Users in vCenter
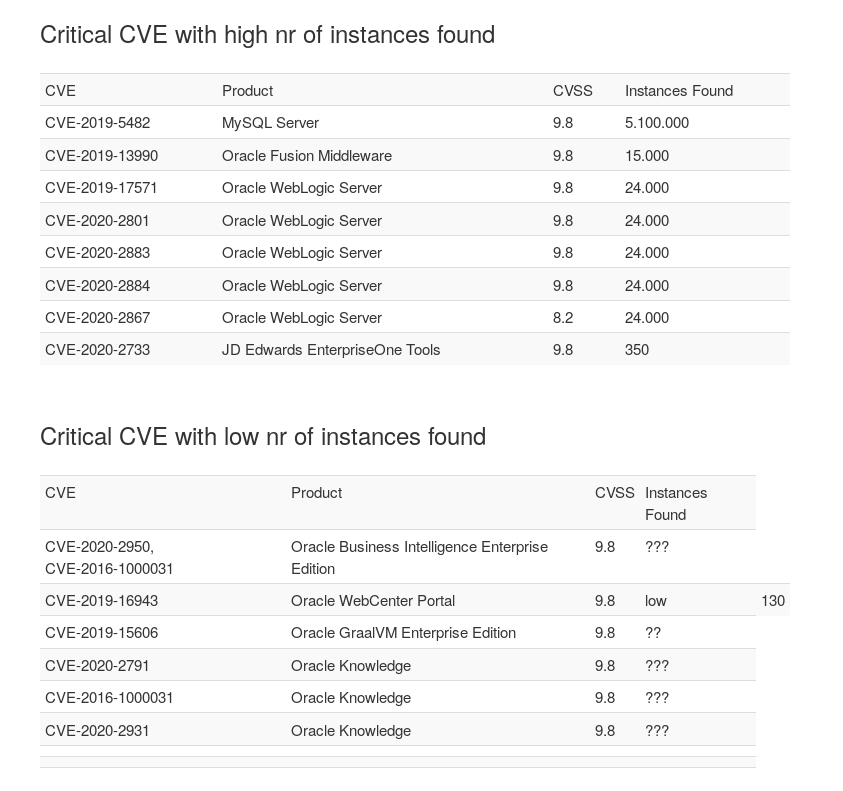
- Oracle has a couple of critical Vulns (CVSS 9.8) in the following products
- MySQL Server
- Fusion Middleware
- WebLogic Applicationserver
- JD Edwards Enterprise Tools
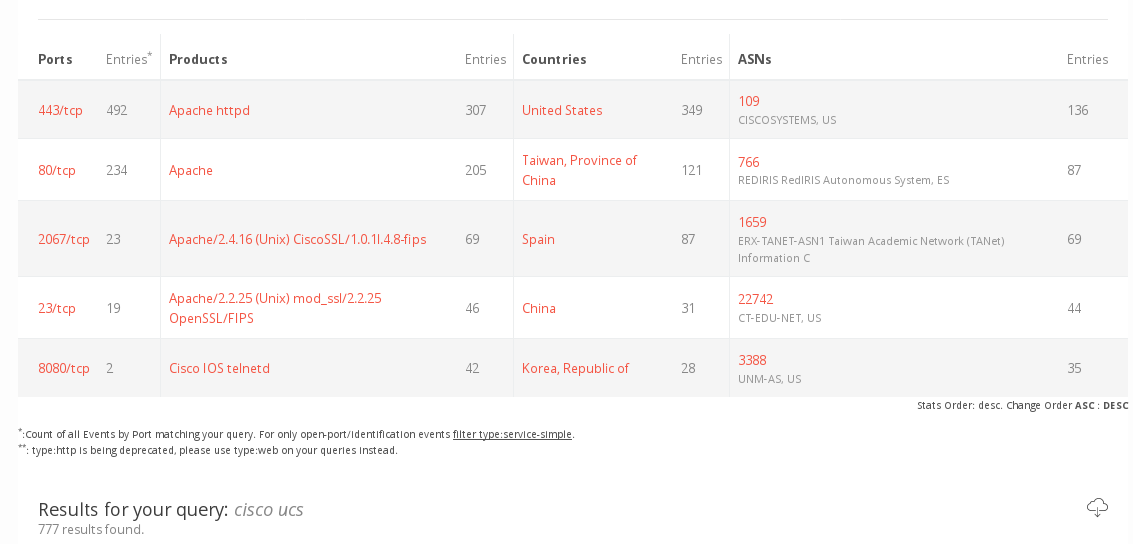
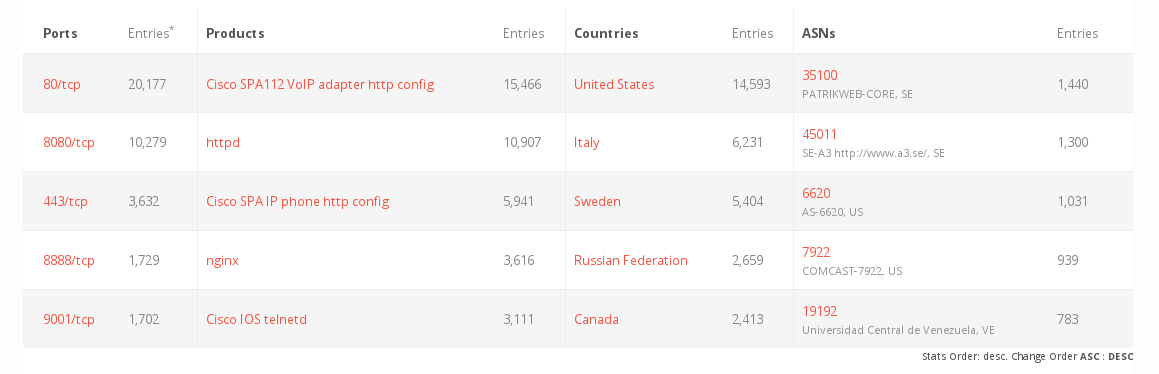
- re: Oracle -> Cisco: hold my beer and releases advisories with critical RCE-Vulns (both CVSS: 9.8) for UCS Director (CVE-2020-3240) and Cisco IP - Phones (CVE-2016-1421) (yes, that Bug lived for 4 years)
- a POC already exists for the UCS-Vuln so DONT PANIC
2020-04-14 [+]
- 40 new CVEs since 2020-04-11, none critical
- for those who may have skipped some messages due to easter-holidays, there was a serious VMWare vCenter-Vuln, allowing sensitive information disclosure late last Thursdays, with approx ~85.000 installations to be found online
2020-04-11 [+]
- 15 new CVEs, some critical
- VMWare vCenter published CVE-2020-3952 with CVSS - 10; operators of VMWare vCenter or PSC should upgrade ASAP
- someone goes around and whipes all ElasticSearch - Servers (again); approx. 34.000 found accessible online
2020-04-10 [+]
- 109 new CVEs, some critical
- Juniper releases a huge number of Security-Advisories for different products that everyone using Juniper should study
- that mentioned Symantec-Case is not so terrible anymore (EOL-Product, according to a Notice in a tweet)
Symantec Secure Web Gateay seems to have a PreAuth and PostAuth - 0day, leading both to RCE
2020-04-08 [+]
- RCE in Dell iDRAC, CVE-2020-5344
- RCE in Zoho ManageEngine ADSelfService, CVE-2020-11518
- RCE in Paessler PRTG, CVE-2020-10374
- RCE/Java-EL-Injection in Nexus Repository Manager, CVE-2020-10199
2020-04-06 [+]
- 12 new CVEs, some new Critical
- CVE-2020-11527 + CVE-2020-11518 Zoho ManageEngine RCE and arbitrary file read
- CVE-2020-10199 Nexus Repository Manager RCE
- we will issue an alert later today and publish lists to the Github-Repo for easier access
- a russian telco highjacked some juicy AS over the weekend: Rostelecom involved in BGP hijacking incident this week impacting more than 200 CDNs and cloud providers.
2020-04-04 [+]
- 57 new CVEs, some under investigation
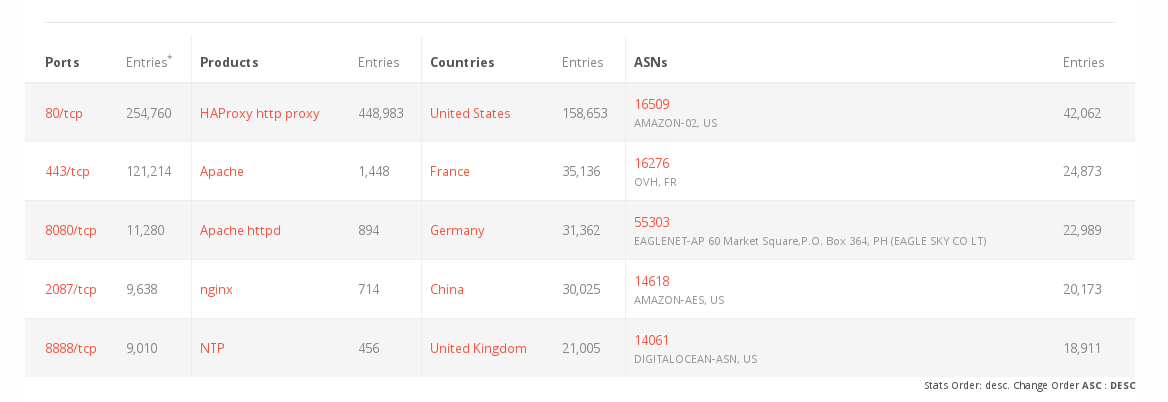
- for the HAProxy-Case from yesterday (CVE-2020-11100) we issued an alert with more details:
[SB 20.08] RCE in HAPROXY (CVE-2020-11100)
2020-04-03 [+]
- 124 new CVEs, 1 Critical HAPROXY, (CVE-2020-11100)
Link to Advisory - we are investigating the HAPROXY-case (460.000 Installations to be found online) and will inform NAT-Certs accordingly

2020-04-02 [+]
- 31 new CVEs, none critical
- Bad Guys started targetting RDP and Company-Access for Ransomware and stuff, due to:
"Sadly we have seen some orgs drop "domain users" into their VPN groups to scale up WFH. We're discovering more valid creds during brute forcing with generic usernames such as meeting-room, conference, vendor, and other dormant but not disabled accounts."
2020-04-01 [+]
- 53 new CVEs, 1 critical (Paessler PRTG)
- a critical unauth-RCE in Paessler Monitoring-System PRTG has been found (CVE-2020-10374), but no CVSS asigned yet
Knowledgebase-Article with Mitigations
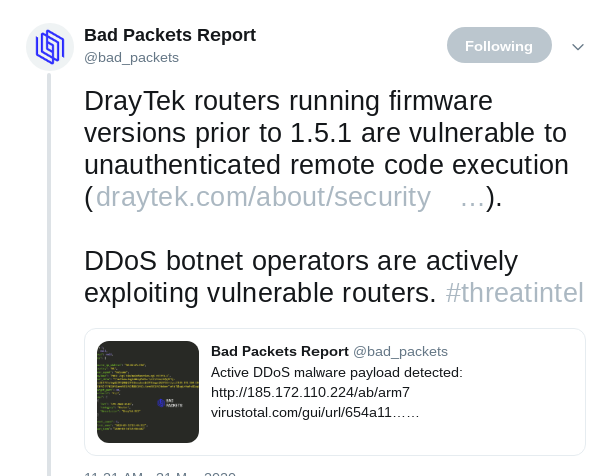
Advisory by cirl.lu - The Draytek-Vuln mentioned yesterday is already exploited by Botnet-Operators
2020-03-31 [+]
- 32 new CVEs, none critical
- POCs emerged for a vuln in Draytek-Broadband-Routers, (CVE-2020-8515, CVSS 9.8, from early Feb 2020),
which has a surpisingly high distribution UK and NL
total: 2.5 Mio devices
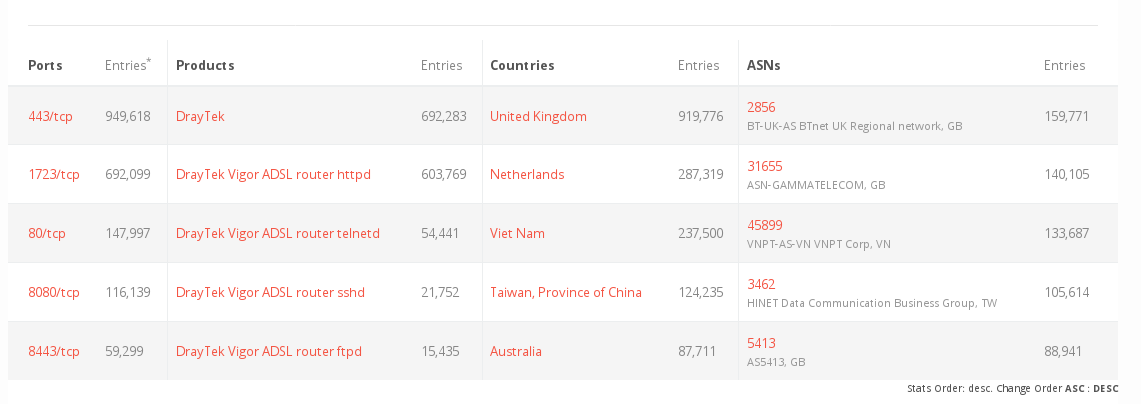
2020-03-30 [+]
- 43 new CVEs, none critical (over the Weekend)
2020-03-26 [+]
- 104 new CVEs, none critical
- Google (Cloud, GPC, Apps) had a short hickup around 6pm UTC, but got fixed soon, read story on ycombinator
- massive uptick in scanning/bruteforce-activities seen by different sources
PulseSecure, Netscaler, RDP
2020-03-25 [+]
- 134 new CVEs, none critical
- a little hickup with DNSSEC due to old BIND9-Installations ( =< 9.11.2 ) and a legacy validation, method (DLV, fixed after 6hrs)
Link to short analysis
2020-03-24 [+]
- 120 new CVEs, none critical
- an issue with memcached DOS, possible RCE, but only a handfull affected (v1.6.[0,1])
Twitter-Link
2020-03-23 [+]
- Critical: CVE-2020-7961 - simple RCE in Liferay - Portal, 33.000 IPs affected
- Critical: Microsoft: ADV200006 | Type 1 Font Parsing Remote Code Execution Vulnerability
2020-03-22 [+]
- 20 new CVEs, none critical
- background-noise of covid-related Malware/Scam/Spam/phishing still very high, see here
2020-03-21 [+]
- 3 new CVEs, none critical
- COVID related Malware/Scam/Phishing on the rise (via RiskIQ)
2020-03-20 [+]
- 57 new CVEs, none critical
- RiskIQ starts daily update:
Investigate | COVID-19 Cybercrime Daily Update
2020-03-19 [+]
- 140 new CVEs, none critical
- very loud background-noise of malware/spam/scam/phishing regarding covid and crisis
- DDoS-Attacks against US Health Agency (HHS)
2020-03-18 [+]
- DDoS-Attacks on takeaway-delivery-services in germany (pizza.de/lieferando.de)
- ca 35.0000 Spam/Phishing - domains related to corona/covid registered daily, -> ZDNet - article
RiskIQ provides free-access-datafeeds
COVID-19 additionals
- RiskIQ: Investigate | COVID-19 Cybercrime Daily Update
- RiskIQ: Feed and daily Updates on COVID-Domains
- John Bambenek COVID-Feed with additional Infos / Manual
Volunteer-Groups and Help:
- COVID-19-CTI: Slack-Channel with CTI and Security-Experts, CERTs, Telcos, created by Ohad Zaidenberg from Clearsky / Announcement
- COVID19 Cyber Threat Coalition: Slack-Channel with CTI and Security-Experts, lots of national CERTs, Registrars / created by Joshua Saxe from Sophos / Announcement
- Coveware und Emsisoft: COVID-19 Response: Free Ransomware Assistance for Coronavirus Healthcare Providers
Fragen? Kontakt: info@zero.bs
