Updates/Timeline
- 2021-03-[03-09] IOC and DFIR - Links added below
- 2021-03-11 - PoC released
- 2021-03-14 - multiple working PoCs circulating
- 2021-03-23 - ransomware-gangs starting to use the vuln for attacks
Today Microsoft released a blogpost detailing an exploit-campaign by the group HAFNIUM, targeting and exploiting Exchange-Servers with 0-Day-Exploits.
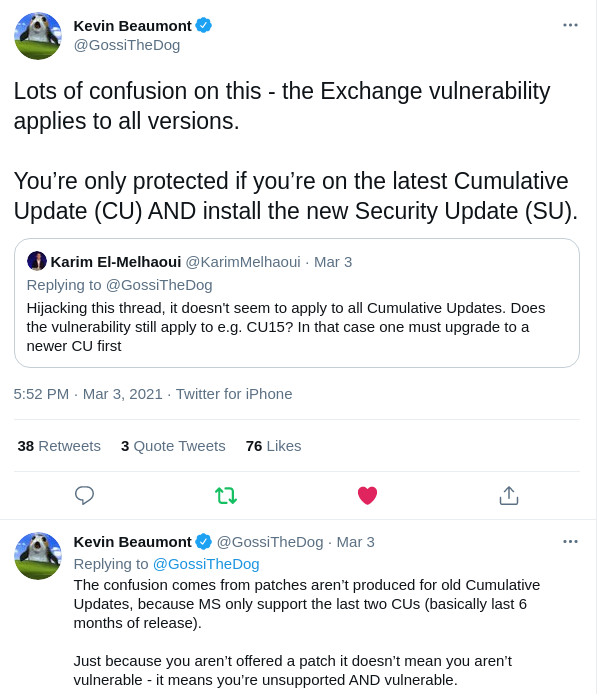
Microsoft releases emergency-patches for mentioned 0days as well for affected Exchange-Servers:
- Microsoft Exchange Server 2013
- Microsoft Exchange Server 2016
- Microsoft Exchange Server 2019
A more C-level-Blogpost: New nation-state cyberattacks was released by MS as well.
We urge our customers to update affected Exchange-Installations ASAP, since PoCs and massexploitation is to be expected within days.
If you have patched, confirm the patch with a vulnscan (see reasons below)
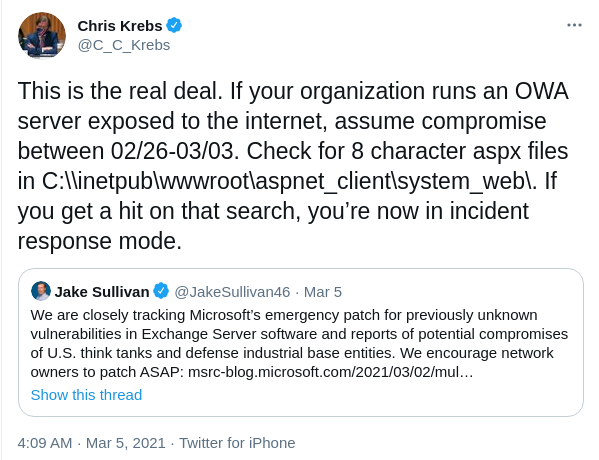
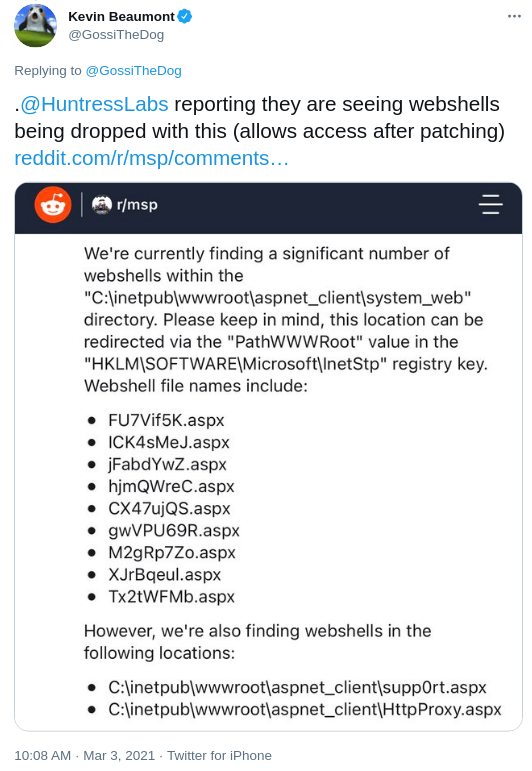
Since 2021-03-02 public exploits are floating around, every instance not patched before this date should be assumed compromised. Thera are also reports of mass-scanning dating back to 2021-02-26
ATTENTION: if you operate in a field that is susceptible to state-actor-attacks, CISA released an Alert, stating that scans and exploitation dates back as Sep 2020:
CISA is aware of threat actors using open source tools to search for vulnerable Microsoft Exchange Servers and advises entities to investigate for signs of a compromise from at least September 1, 2020.
Since 2021-03-21 Ransomware-Gangs are actively using the vuln to attack companies.
According to a client affected by the incident, the events that led to the successfull attack took place in the following timeline
- 2021-03-05 Webshell ChinaChopper deployed
- 2021-03-09 System been seen in a Vulnscan, ignored
- 2021-03-12 System patched
- 2021-03-20 BK access the system for the first time via webshell
- 2021-03-23 Exchange and AD encrypted
References
Timeline
- Microsoft: Multiple Security Updates Released for Exchange Server
- HAFNIUM targeting Exchange Servers with 0-day exploits
- Microsoft: New nation-state cyberattacks
- Microsoft: Released: March 2021 Exchange Server Security Updates
- Microsoft says China-backed hackers are exploiting Exchange zero-days
- Microsoft Exchange Server Vulnerabilities Mitigations – updated March 6, 2021
- Volexity: Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities
- OrangeTsai Proxylogon
- ProxyLogon - Details
- CISA-Alert on Vulnscans dating back Sep 2020
- MassExploitation/Webshells beeing deployed 2021-03-03
- automated exploitation of Internet-facing Exchange servers/03.03.
- Expect exploitation starting 26.02/03.03.
- Brian Krebs: At Least 30,000 U.S. Organizations Newly Hacked Via Holes in Microsoft’s Email Software
- Brian Krebs: A Basic Timeline of the Exchange Mass-Hack
- Timeline by Unit42
- Nr of exploitable Exchange-installations over time
- TheRecord: Microsoft Exchange servers targeted by second ransomware group
- Analyzing attacks taking advantage of the Exchange Server vulnerabilities
All Things Updates
- Microsoft: Multiple Security Updates Released for Exchange Server
- Microsoft: Released: March 2021 Exchange Server Security Updates
- Issues due to Exchange Server security updates
- BlueTeamThread
- About Updates/PatchAdvise
- MS: ExchangeUpdateWizard
- UpdateProgress Part 1
- Microsoft has released a new, one-click mitigation tool, the Microsoft Exchange On-Premises Mitigation Tool
IOCs
- IOCs Twitter/eric_capuano
- IOCs Twitter/steventseeley
- IOC/DFIR: Rapid response, Mass Exploitation and IOCs by Huntress.com
- IOC: feed of observed indicators of compromise (IOCs)
- IOC: CISA-IOCs
DFIR & PoC
- PublicPOC (untested), but most probably confirmed by Malwaretechblog
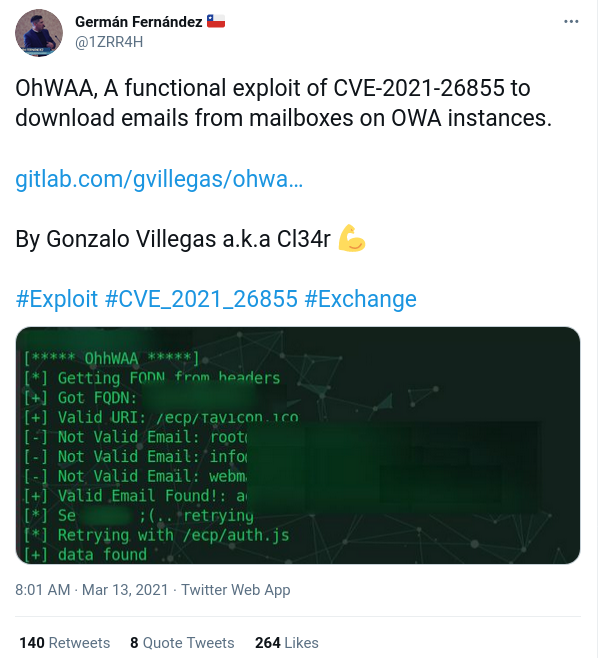
- Public PoC to read any emails surfaced
-
BleepingC: New PoC for Microsoft Exchange bugs puts attacks in reach of anyone
- EsetMassExploit
- DFIR: Webshell-detection
- DFIR: Rapid response, Mass Exploitation and IOCs by Huntress.com
- DFIR: NSE-Script to test for the vuln by MS
- DFIR: simple NSE-script to check for probably vulnerable exchange-versions
- DFIR: Detection and Response to Exploitation of Microsoft Exchange Zero-Day Vulnerabilities by FireEye
- DFIR: NCC released a tool to check docroots for compromise/implants
- DFIR: automated exploitation of Internet-facing Exchange servers/03.03.
- Yara/ThorLite-Rules
- DFIR: Scan for HAFNIUM Exploitation Evidence with THOR Lite
- DFIR: MS-Tools to check locally (hashes) and remote (vulnscan)
- DFIR: tool to create a scanfile to check remotely for backdoors
- DFIR: why webshells might disappear
- DFIR: update for MSERT Microsoft Safety Scanner to scan locally for Backdoors
- DFIR: Defender-update
- DFIR: Guidance for responders: Investigating and remediating on-premises Exchange Server vulnerabilities by MS/MSRC-Team
Fragen? Kontakt: info@zero.bs
