Timeline
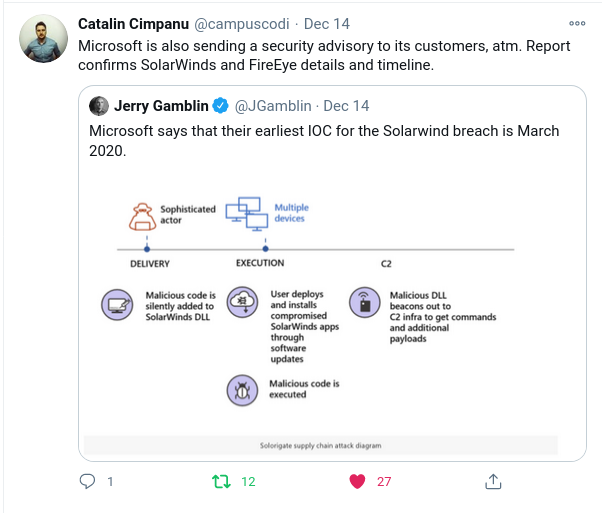
On Dec 14, 2020, news broke that recent hacks of Fireeye and other are linked to a supply-chain-attack on SolarWind
[
link
](https://twitter.com/campuscodi/status/1338346046896939008)
[
link
](https://twitter.com/campuscodi/status/1338346046896939008)
[
CISA-Advisory
](https://www.cisa.gov/news/2020/12/13/cisa-issues-emergency-directive-mitigate-compromise-solarwinds-orion-network)
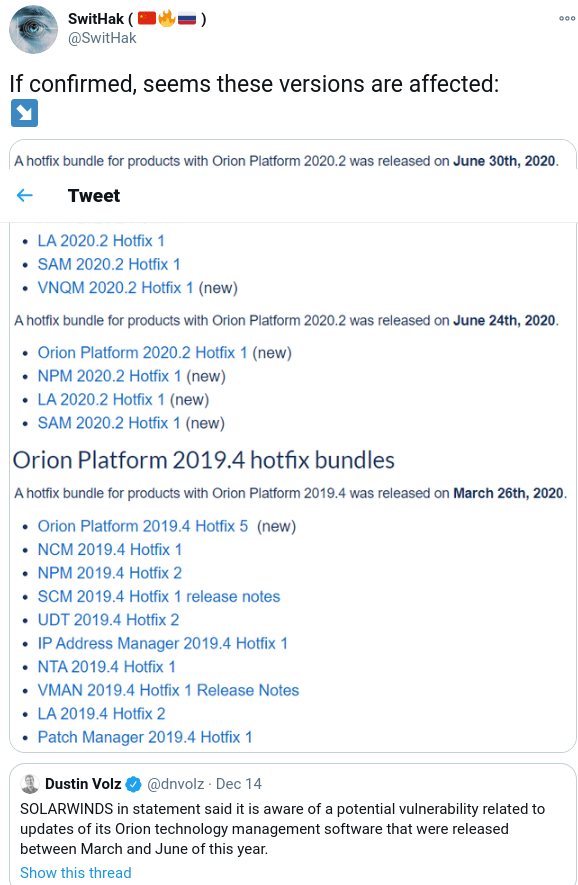
Versions affected
[
link
](https://twitter.com/SwitHak/status/1338269888796905474)
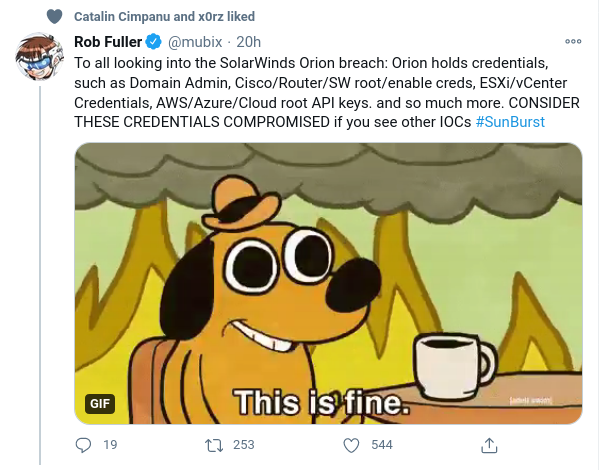
Impact
[
Impact
](https://twitter.com/mubix/status/1338502543635329028)
[
Thread on Impact
](https://twitter.com/KimZetter/status/1338389130951061504)
[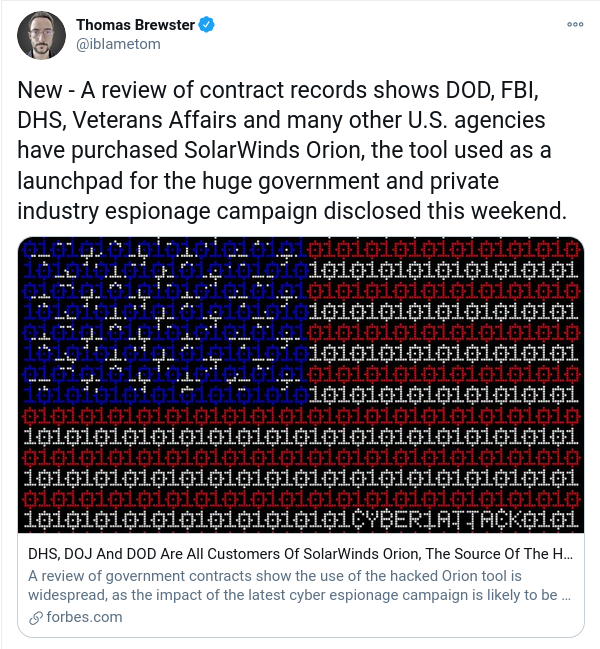
Thread on Impact
](https://twitter.com/iblametom/status/1338430669534490631)
DFIR
from the advisory solarwinds.com/securityadvisory:
[
link
](https://twitter.com/mubix/status/1338775856408367104)
Mubix released a PW-Dumper for SolarWinds: SolarFlare Release: Password Dumper for SolarWinds Orion
[
link
](https://twitter.com/ffforward/status/1338785034375999491)
Article by NetReSec on [Finding Targeted SUNBURST Victims with pDNS]https://www.netresec.com/?page=Blog&month=2021-01&post=Finding-Targeted-SUNBURST-Victims-with-pDNS
IOCs
Domains from FireEye/Volexity
databasegalore[.]com
deftsecurity[.]com
digitalcollege[.]org
freescanonline[.]com
highdatabase[.]com
incomeupdate[.]com
lcomputers[.]com
panhardware[.]com
thedoccloud[.]com
CobaltStrike Beacon domains (Symantec)
ervsystem[.]com
infinitysoftwares[.]com
Subdomains
https://blog.prevasio.com/2020/12/sunburst-backdoor-part-ii-dga-list-of.html
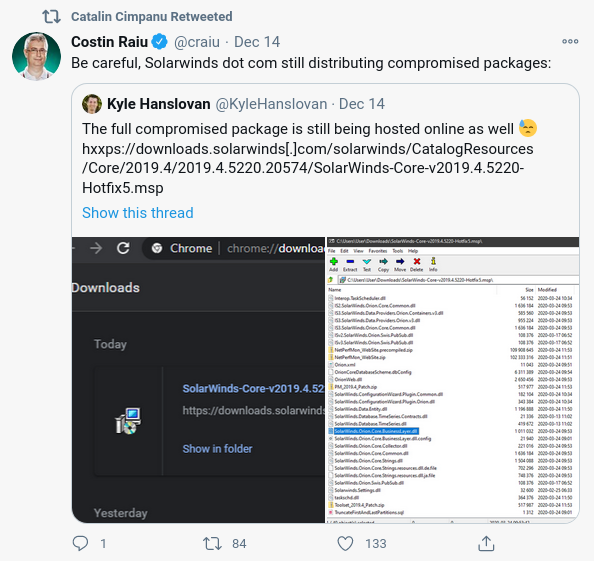
updates still compromised
as of Dec 14, Updates are still compromised
[
link
](https://twitter.com/craiu/status/1338400603769348096)
[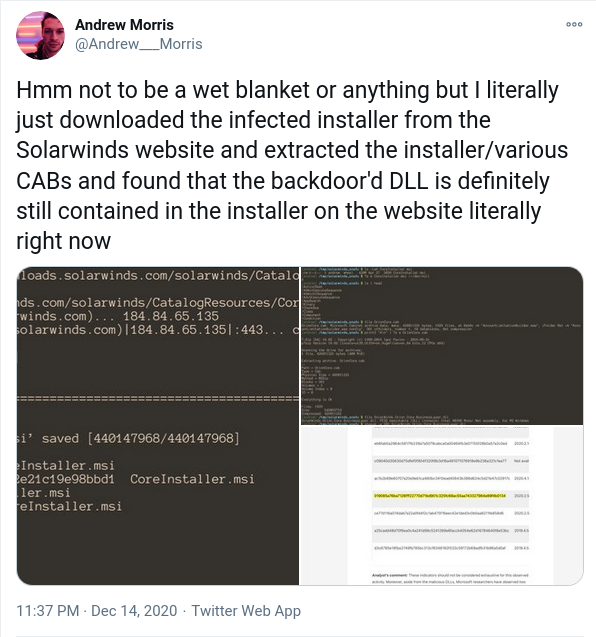
link
](https://twitter.com/Andrew___Morris/status/1338614208905302021)
AttackWay
possibly
[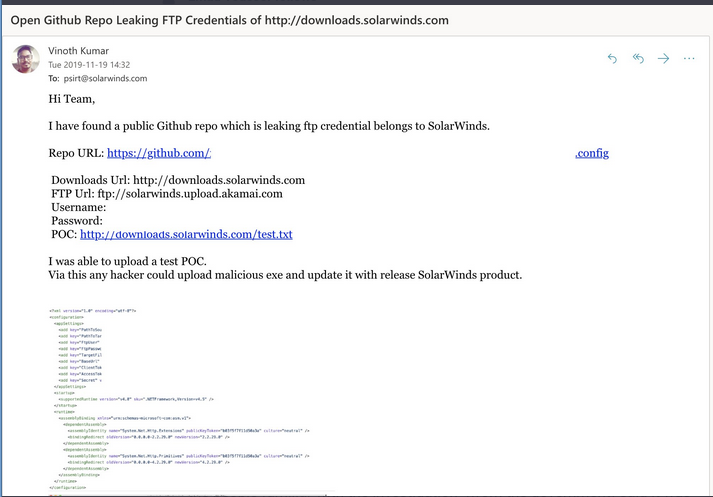
link
](https://twitter.com/vinodsparrow/status/1338431183588188160)
Fragen? Kontakt: info@zero.bs
