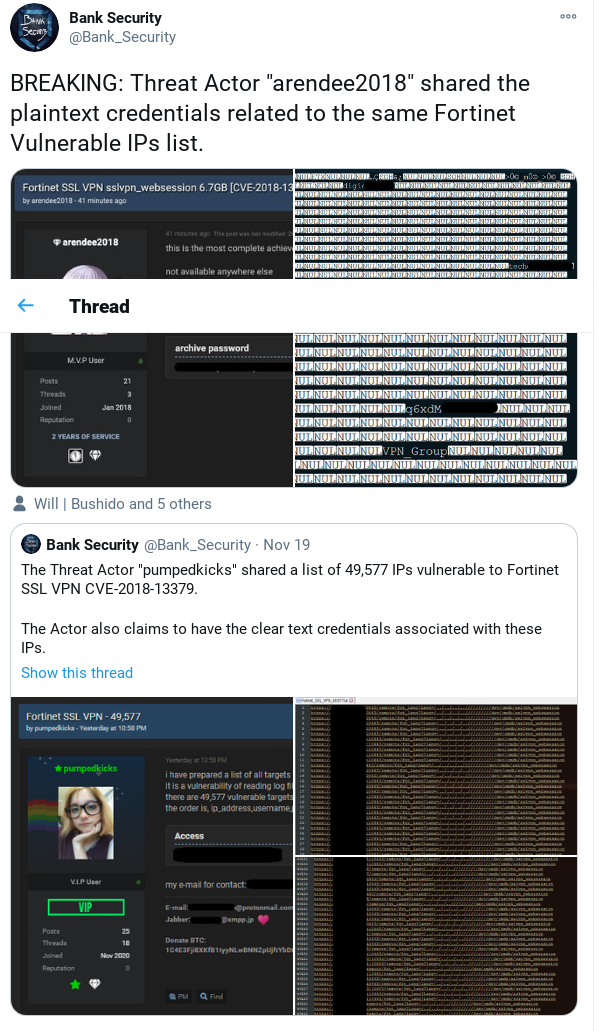
A List of 49.000 vulnerable Fortinet-VPN-gateways has been released on a popular hackerforum in 2020-11-19 [1]
6 days later, an archive with credentials for that IP-list has been released by a different actor in the same forum [2]
a short analysis
- 49577 IPs in the original list
- 49622 IPs in the Cred-Archive with 1 or more credentials listed
- 45953 IPs of that original list are still vulnerable as of 2020-11-225, as a short vulnscan by a partner of us showed
Summa summarum: since the original actors released the data from a 2 year old vuln, with VPN-Data for 49k VPN-gateways of which 45k are still online and vulnerable: expect the access-brokers are already in there and the next huge Ransomware-wave incoming.
what you should do, if you operate a Fortinet SSL-VPN - Gateway
- check, if you are on the list
- check, when you deployed the patches. if it wasnt in 2018, right after the CVE-2018-13379 and fixes have been published, do some forensic on your gateway and check if there implants / unusual behavior, and nuke from orbit.
If you operate an AS or Network or single IP, feel free to contact us, we can check if one of your IPs or networks is on that list, for free. Just click the Button below or send an Email.
References
- Hacker posts exploits for over 49,000 vulnerable Fortinet VPNs
- Threat Actor "arendee2018" shared the plaintext credentials related to Fortinet Vulnerable IPs list
Fragen? Kontakt: info@zero.bs
