Talos recently released and advisory for ISCB-BIND TALOS-2020-1100 - Internet Systems Consortium's BIND TCP Receive Buffer Length Assertion Check Denial of Service Vulnerability CVE-2020-8620 where an unauth DOS is described.
An assertion failure exists within the Internet Systems Consortium’s BIND server versions 9.16.1 through 9.17.1 when processing TCP traffic via the libuv library. Due to a length specified within a callback for the library, flooding the server’s TCP port used for larger DNS requests (AXFR) can cause the libuv library to pass a length to the server which will violate an assertion check in the server’s verifications. This assertion check will terminate the service resulting in a denial of service condition. An attacker can flood the port with unauthenticated packets in order to trigger this vulnerability.
2 interesting things here:
- version 9.16-9.17
- Port 53/TCP
from all the ISC-Bind versions in use online, that answered on Port 53/tcp (2.3 mio total) we could identify 13.000 as version 9.16/9.17 (0.8%), while 14% (340.000 installations) dont show versions-info; see an according table and chart below.
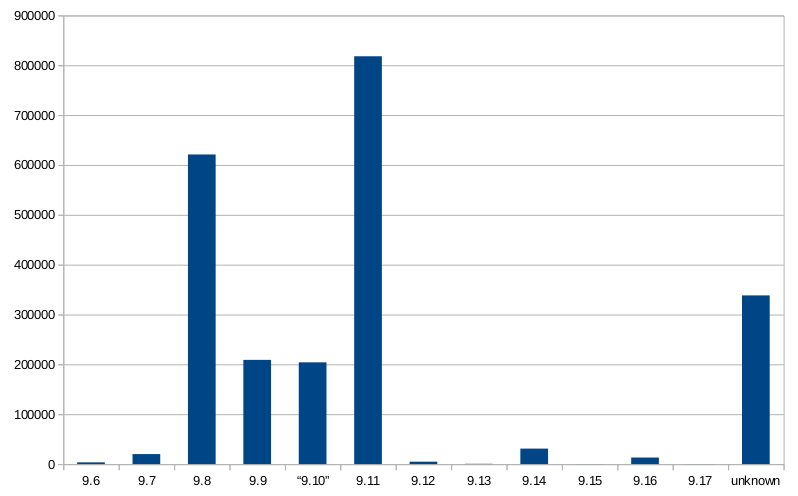
| Version | Count | % |
|---|---|---|
| ISC BIND/9.5.x | 2700 | 0.1 |
| ISC BIND/9.6.x | 3400 | 0.15 |
| ISC BIND/9.7.x | 20.000 | 0.9 |
| ISC BIND/9.8.x | 209.000 | 27 |
| ISC BIND/9.9.x | 70.096 | 9 |
| ISC BIND/9.10.x | 204000 | 9 |
| ISC BIND/9.11.x | 818000 | 36 |
| ISC BIND/9.12.x | 4800 | 0.2 |
| ISC BIND/9.13.x | 512 | 0.02 |
| ISC BIND/9.14.x | 31000 | 1.4 |
| ISC BIND/9.15.x | 91 | 0.004 |
| ISC BIND/9.16.x | 13000 | 0.6 |
| ISC BIND/9.17.x | 127 | 0.005 |
| ISC BIND/unknown | 338370 | 14 |
Fragen? Kontakt: info@zero.bs
