Critical and high-severity vulnerabilities in F5's BIG-IP-Appliance allowing a remote attacker to take complete control of the targeted system (RCE)
CVE-2020-5902 has a CVSS-Score of 10
The Problem lies within the admin-interface Traffic Management User Interface (TMUI), that can be trivially exploited, when exposed.
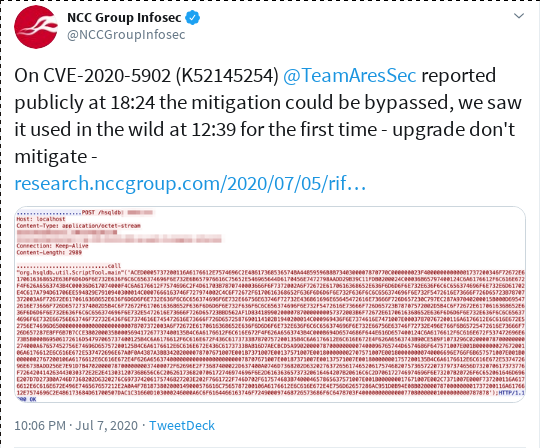
Update 2020-07-07: The Mitigations by F5 mentioned in their Article can be bypassed, and we have multiple confirmation, including active exploitation from logs as well
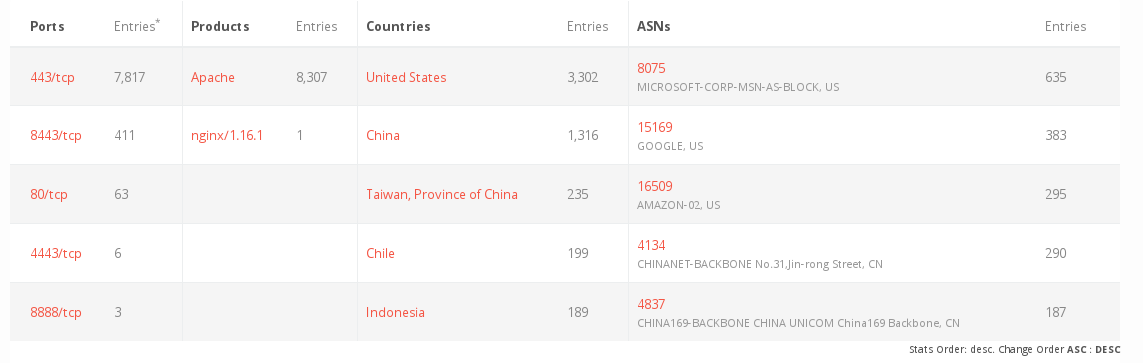
8.500 devices are to be found online.
Updates over the weekend:
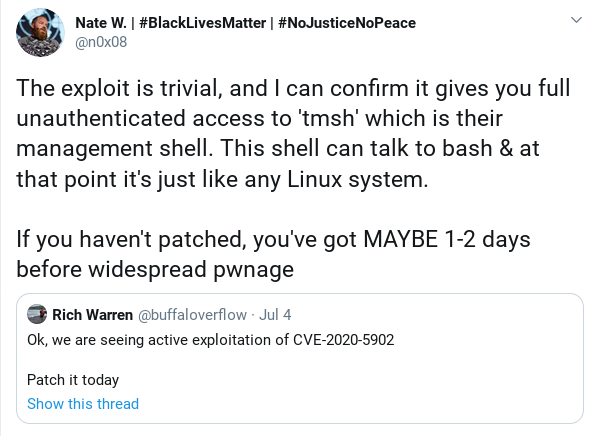
exploits released, mayhem started, every device that was unpatched by 2020-07-05, 16 CET should be considered hacked
- mitigations from F5 can bypassed (we have multiple confirmation, active exploitation from logs as well)
- good summary on the expected impact, by kevvvyg (1)
- Rapid7 releases full RCE
- Twitter-Chatter
- Github-Chatter
- NSE-Script
References
- F5-Advisory: K52145254: TMUI RCE vulnerability CVE-2020-5902
- NCC: RIFT: F5 Networks K52145254: TMUI RCE vulnerability CVE-2020-5902 Intelligence
- mitigations from F5 can bypassed (we have multiple confirmation, active exploitation from logs as well)
- Twitter-Chatter
- Github-Chatter
Fragen? Kontakt: info@zero.bs
