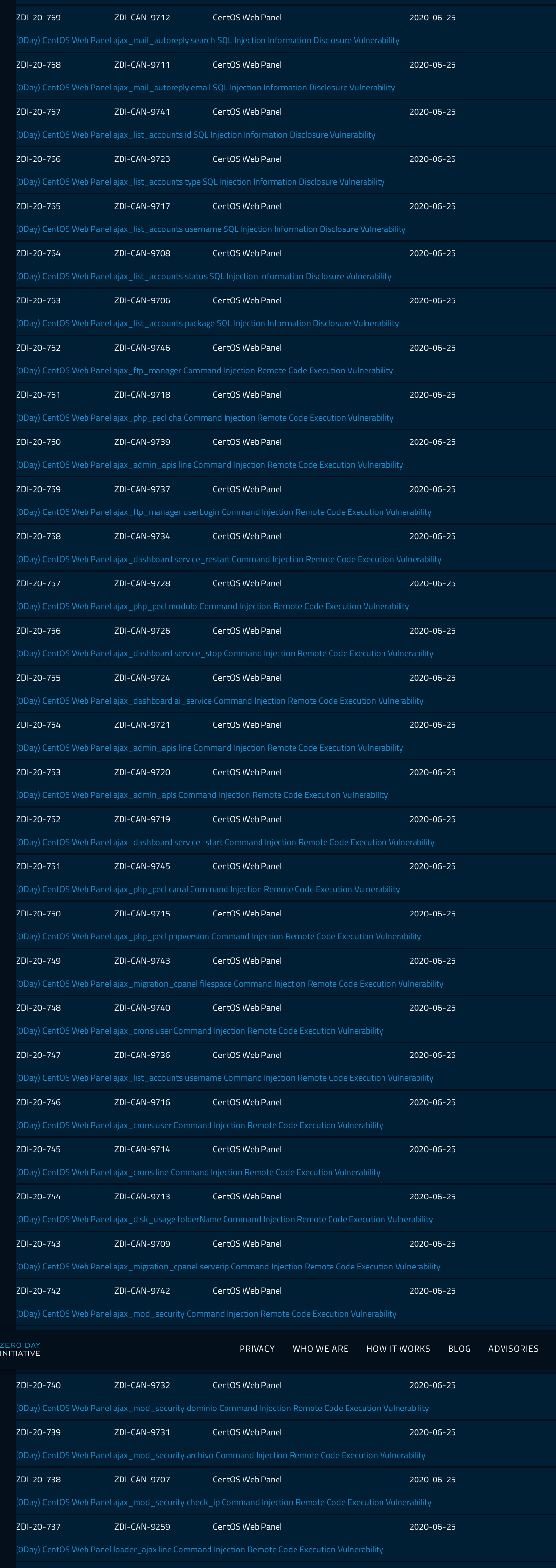
ZDI has released 37 0day-advisories with critical vulns for CentOS WebPanel; multiple SQL-Injections, some of them RCE with CVSS of 9.8, like (0Day) CentOS Web Panel ajax_mod_security archivo Command Injection Remote Code Execution Vulnerability which reads like a nightmare:
This vulnerability allows remote attackers to execute arbitrary code on affected installations of CentOS Web Panel. Authentication is not required to exploit this vulnerability. The specific flaw exists within ajax_mod_security.php. When parsing the archivo parameter, the process does not properly validate a user-supplied string before using it to execute a system call. An attacker can leverage this vulnerability to execute code in the context of root.
It looks like CentOS-Webpanel-Team (which has nothing to do with CentOS-Team) did not acknowledged the vulns, because no CVE had been requested and ZDI released the advisories as 0-Days
Mitigation
- take CentOS Webpanel offline
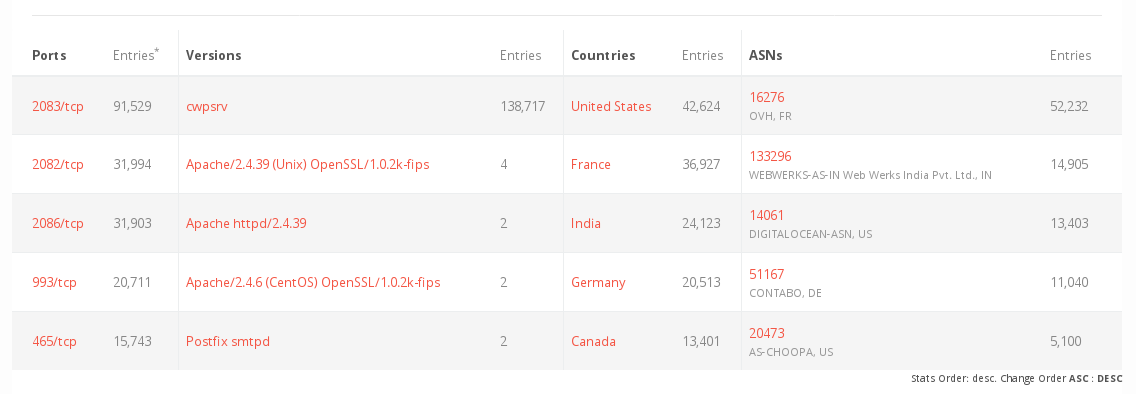
We found 215.000 IPs online with CentOS WebPanel installed, and since this will allow complete server-takeover, we expect a lot of fallout.
List of Advisories
Fragen? Kontakt: info@zero.bs