A critical Bug has been discovered and fixed in Grafana
that allows an unauthenticated attacker to misuse the unprotected
/avatar/* URL for a SSRF-Request that may be chained into a RCE
(CVE-2020-13379).
CVSS is not assigned, but might be expected to be a 9.x
Since patches are out, exploiting the bug does not looks like supermagic, and the finder of the vuln (@Rhynorater) announced to release a PoC later, we expect heavy exploitation very soon.
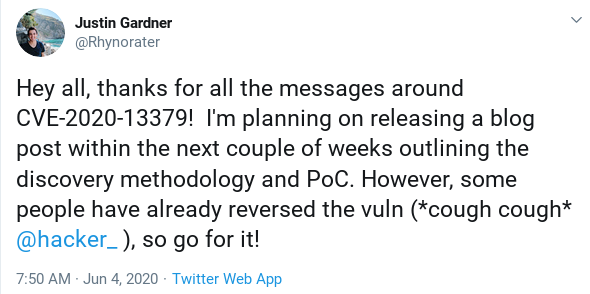
We tested the attacking-URL as well and found the /avatar/* - route
unprotected (the grafana - installation itself had a login-page)
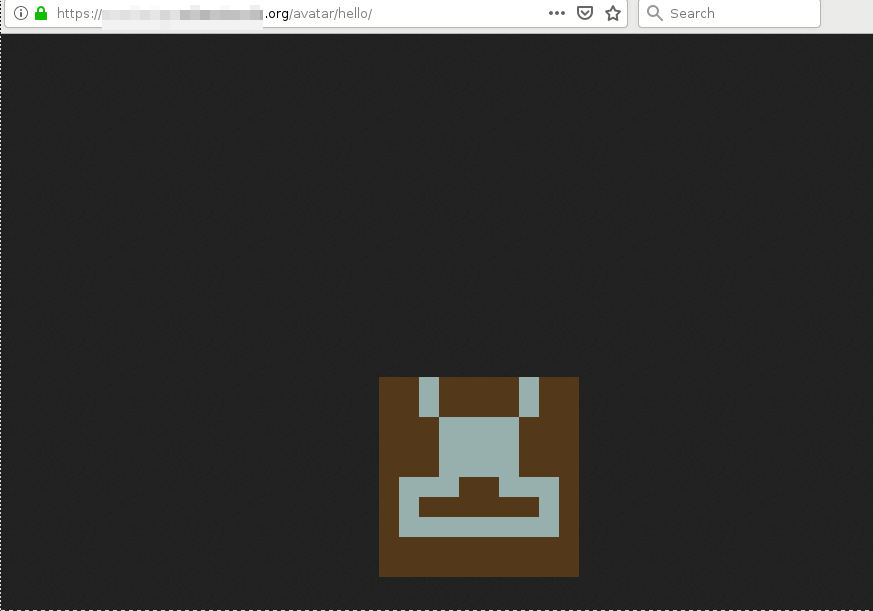
Thread-Surface
60.000 instances to be found online, and since this is unauth, all might be exploited.
References
Fragen? Kontakt: info@zero.bs
