CVSS-Score: 10.0
exploited in the wild == 0day
possible RCE
A SQL injection issue was found in SFOS 17.0, 17.1, 17.5, and 18.0 before 2020-04-25 on Sophos XG Firewall devices, as exploited in the wild in April 2020.
This affected devices configured with either the administration (HTTPS) service or the User Portal exposed on the WAN zone.
A successful attack may have exfiltrated usernames and hashed passwords for the local device admin(s), portal admins, and user accounts used for remote access (but not external Active Directory or LDAP passwords); RCE is probably possible as well, as Sophos stated in an aftermath-article.
Sophos delivers an extensive KB-article with details and also lists ways to determine, if a firewall has been exploited.
In an aftermath -
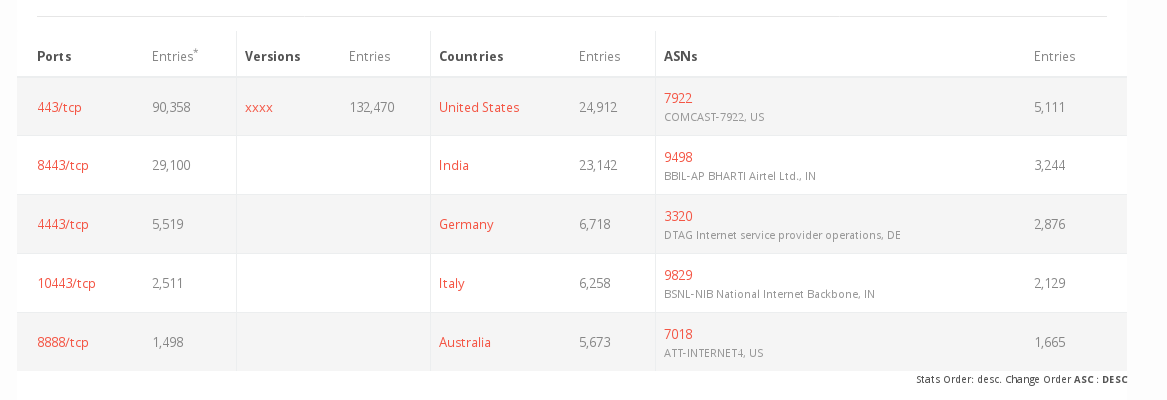
There are 130.000 possible targets worldwide to be found.

References
- Sophos: Fixing SQL injection vulnerability and malicious code execution in XG Firewall/SFOS
- NIST: CVE-2020-12271 Detail
- Sophos: "Asnarök" Trojan targets firewalls
Fragen? Kontakt: info@zero.bs
