VMWare released an adivisory (VMSA-2020-0006) which pointed to a critical vulnerability with CVSS-Score of 10.0 in vCenter/vmdir that allows an attacker to "extract highly sensitive information which could be used to compromise vCenter Server or other services which are dependent upon vmdir for authentication."
TL;DR: You can create/have access to user with Admin-Rights in vCenter (BOOM)
Because of the score we expect this vulnerability easy to be found and exploited by 3rd parties and POCs probably incoming very soon.
Multiple Exploits/POCs have emerged
(Update: 2020-04-17)
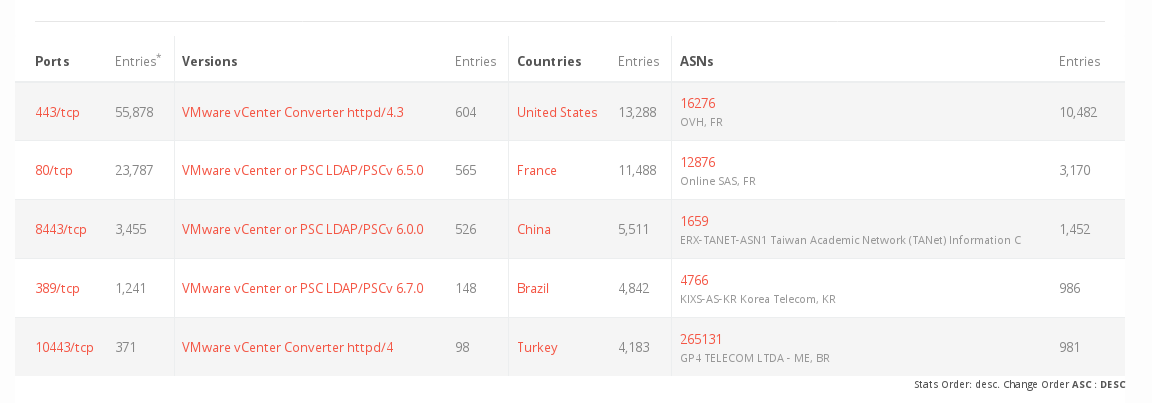
Workarounds
- none
Additional Notes
vCenter Server 6.7 (embedded or external PSC) prior to 6.7u3f is affected by CVE-2020-3952 if it was upgraded from a previous release line such as 6.0 or 6.5.
Clean installations of vCenter Server 6.7 (embedded or external PSC) are not affected.
References:
- VMWare: VMSA-2020-0006
- VMWare: Additional Documentation for VMSA-2020-0006: Determining if a vCenter 6.7 deployment w/embedded or external Platform Services Controller (PSC) is affected by CVE-2020-3952 (78543)
Fragen? Kontakt: info@zero.bs
