On Thursday, 2020-04-02 the HAProxy-Team announced an update to HAProxy because of a vulnerability in the HPACK-decoder used for HTTP/2 which may lead to which cause memory corruption, leading to a crash or potential remote arbitrary code execution, when sending a crafted HTTP/2 - request.
Affected: version 1.8 and above
HAProxy is packaged with Openshift-Plattform, but the attack-surfaced is limited, according to this bugzilla-page:
OpenShift Container Platform versions through 4.3 contain the vulnerable code; exploitation requires setting ROUTER_USE_HTTP2 in the OpenShift Ingress Operator, which is not currently possible. The impact of this vulnerability is therefore reduced in OCP 4.x, prior to version 4.4, to low.
OpenShift Container Platform 3.11 added a configuration option to ose-haproxy-router that made enabling HTTP/2 support easy. However, it is not enabled by default on that version.
Updates
2020-04-21
a POC has been released: @_fel1x vai Twitter,
Project Zero Advisory: Issue 2023: haproxy: out-of-bounds-write in http2 hpack dynamic table
Mitigations
There is no configuration-based workaround for 2.1 and above. src
Impact
HAProxy is widely used and usually well maintained; so we expect a huge ammount of affected systems (460.000 installations indexed)
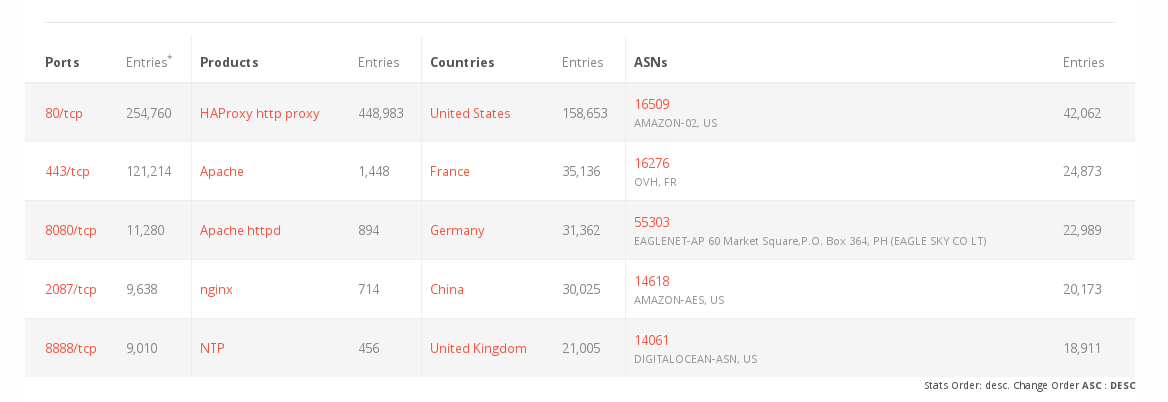
The Bug was discovered by Google's ProjectZero.
References
- Mailinglist-Announcement: [ANNOUNCE] haproxy-2.1.4
- Redhat: CVE-2020-11100 haproxy: malformed HTTP/2 requests can lead to out-of-bounds writes
- Redhat-Bugzilla: Bug 1819111 (CVE-2020-11100) - CVE-2020-11100 haproxy: malformed HTTP/2 requests can lead to out-of-bounds writes
Fragen? Kontakt: info@zero.bs
