DDoS attacks on Internet infrastructure and web services are a troublesome problem and a plague, not only since Mirai, However, with the theme of IoT and IoT-based botnets, DDoS has become a serious threat to services and the Internet infrastructure.
The "Packet Firing Range" - trainings gives administrators and operations personnel the ability to experience and fend off DDoS attacks on multiple targets in a real-time simulation.
Special attention is paid to offering participants the widest possible range of attacks, based on real world examples and to discussing and using the available options for action.
At the workshop, the participants learn additional techniques of the attackers, including:
- how information gathering (OSINT) of the attackers works (OSINT)
- how attackers see and analyze your own organization from the outside
- what methods attackers use to make themselves invisible
- how you can reduce your own attacksurface and thus avoid direct attack points
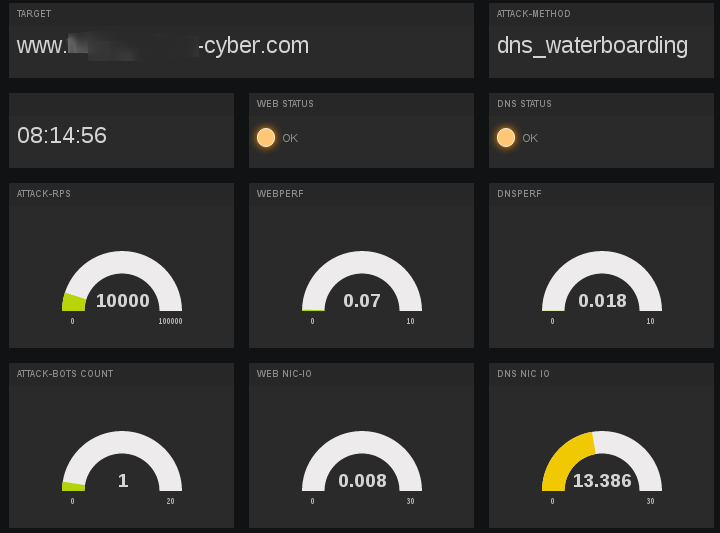 Packet Firing Rang - Dashboard
Packet Firing Rang - Dashboard
The Packet Firing Range, especially in conjunction with a stress test, is intended as a fire-fighting exercise for admins and operations personnel who can test effects and countermeasures in a controlled environment to be prepared for emergencies.
The Packet Firing Range forms the basis for understanding the nature and impacts of DDoS attacks and the application of the DDoS defense toolkit, which are used in later Stresstests against the own infrastructure.
Links:
Topics and agenda:
- Problem DDoS, current examples
-
Introduction to the problem of botnet attacks
-
Overview of the current threat situation (who, what, why)
- DDoS as a Service, Alphabay and Cybercrime Exchanges in Darknet
- Outlook for the near future
-
Rate defensive ability
- short introduction to the DDoS Resiliency Score (DRS)
- OSINT: Attackers' Methods to enumerate Systems
- Reconnaissance / intelignce against its own infrastructure
-
Overview of DDoS attack types
- Overview of common protection methods, methods and appliances
- Introduction to the DDoS Defense Toolkit
- DDoS Defense Toolkit and its own protection procedures
- Exercises detection, defense, working with the toolkit
-
Explanation types of attacks, examples and exercises / volume attacks (layer 3,4)
- Detection
- UDP Direct, Reflection, Amplification
- TCP
- Defenseoptions & working with the DDoS Defense Toolkit
-
Explanation Types of attacks, examples and exercises / application attacks (Layer 7)
- Detection
- Attacks Layer 7 Web
- Attacks Layer 7 DNS
- Attacks Layer 7 Any TCP Services
- Attacks using IPv6 (optional)
- Defense Options & working with the DDoS Defense Toolkit
