TL;DR
- new DDOS-Attack-Vector for UDP Amplification/Reflection-Attacks, SRC_PORT 3702
- Port 3702 belongs to WS-Discovery which uses SOAP over UDP (not kidding)
- Amplification-Factor 30 - 100 (*)
-
total 630.000 IPs with UDP WS-Discovery/SOAP - services available online (*)
-
5.000 IPs seen in an attack, attack-size was ~40 GBit/s for that vector alone (multi-vector, volumetric UDP reflection/amplification attack)
Updates
- 2019-08-26 - new analysis on number of devices, based on Binaryedge-Data
- 2019-08-27 - Tucker Preston (@flockforward) helped to evaluate new amplification - factors and mitigation-techniques
- 2019-08-27 - ZDNet: Protocol used by 630,000 devices can be abused for devastating DDoS attacks
- 2019-09-15 - Phenomite informs us on his work he did in early 2019
- 2019-09-18 - Akamai: NEW DDOS VECTOR OBSERVED IN THE WILD: WSD ATTACKS HITTING 35/GBPS
- 2019-09-18 - Wired: Clever New DDoS Attack Gets a Lot of Bang for a Hacker's Buck
Intro
A client of us got attacked recently (August 2019) with a moderate 300GBit/s volumetric DDoS - attack, which was easily mitigated. The attack was a quite "normal" UDP Reflection/Amplification, mostly from LDAP-servers.
While analyzing the attack to determine the attacker-level we detected an unknown (to us) source-port 3702, and shortly after we began to investigate a possible new DDoS-Attackvector.
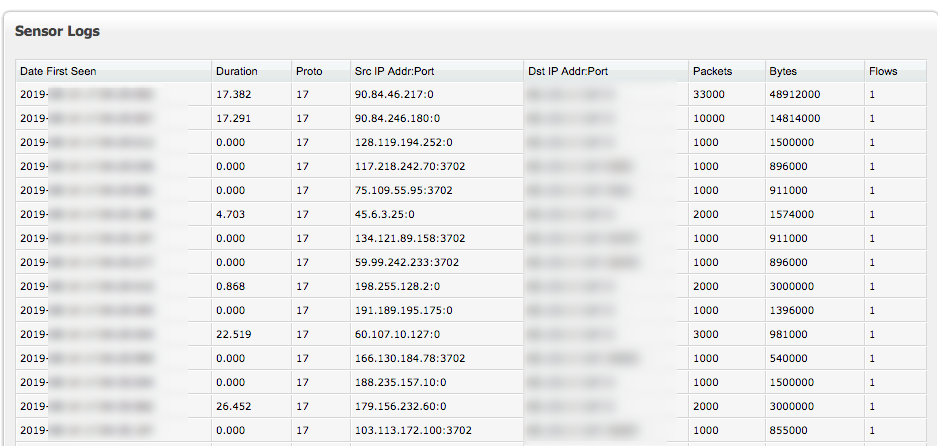
Port 3702/UDP is used by the WebService-Discovery-Protocoll which uses SOAP (XML) over UDP.
From Wikipedia:
Web Services Dynamic Discovery (WS-Discovery) is a technical specification that defines a multicast discovery protocol to locate services on a local network. It operates over TCP and UDP port 3702 and uses IP multicast address 239.255.255.250. As the name suggests, the actual communication between nodes is done using web services standards, notably SOAP-over-UDP.
We modified a Python-Library for scanning, extracted a couple of attacking IPs (see "Stats" below) and started tests to determine the amplification-factor.
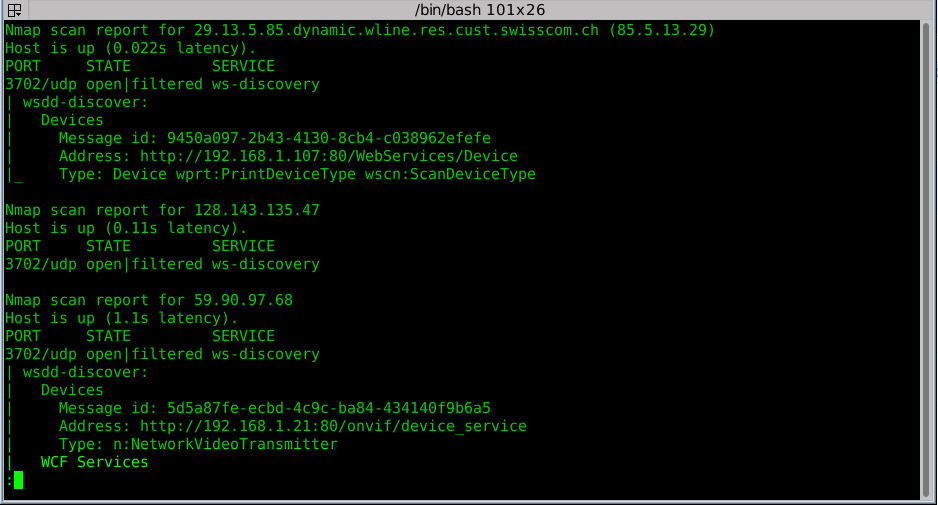
Using nmap's script=wsdd-discover we scanned a handful attacking-IPs and saw mostly 2 different
services advertised:
- cameras
- printers
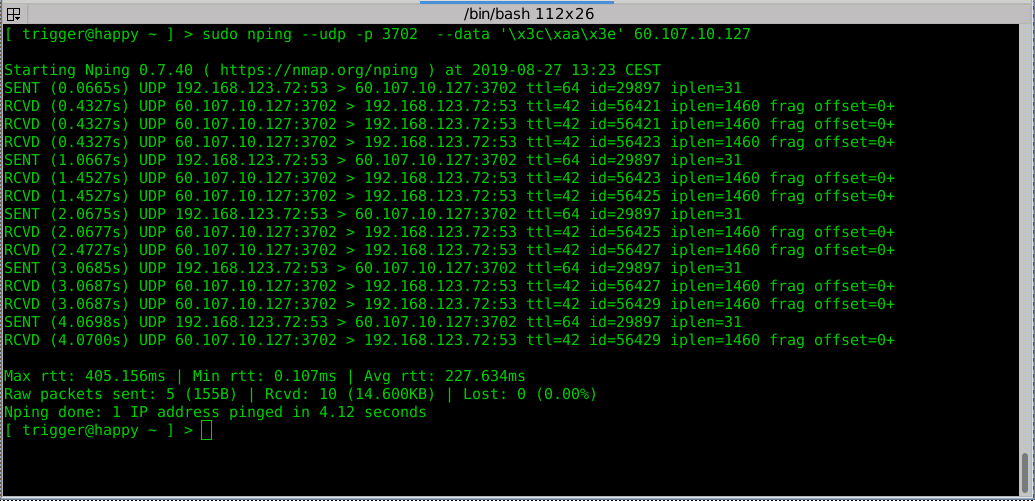
From what we have seen so far, testing 5 different IPs, the amplification-factor varies between 30 and 100, depending on the device connected.
This response we get with a modified ws-discovery-library:
$ discover -l DEBUG -s http://192.168.1.100:80/onvif/device_service
DEBUG:ws-discovery:using eth0 interface with IPv4 address 1.2.3.4
DEBUG:ws-discovery:probe response from 70.171.XX.YY:
--- begin ---
EPR: urn:uuid:1419d68a-1dd2-11b2-a105-70809100754F
Types: [http://www.onvif.org/ver10/network/wsdl:NetworkVideoTransmitter]
Scopes: [onvif://www.onvif.org/type/NetworkVideoTransmitter, onvif://www.onvif.org/name/00001101, onvif://www.onvif.org/hardware/00E00ADD0000, onvif://www.onvif.org/location]
XAddrs: [u'http://192.168.1.100/onvif/device_service']
Metadata Version: 1
--- end ---
With help from Tucker Preston (@flockforward), who also told us he saw such kind of attacks back in May 2019, attacking with up to 350 GB/s, we were able to come up with an amplification-factor up to 100:
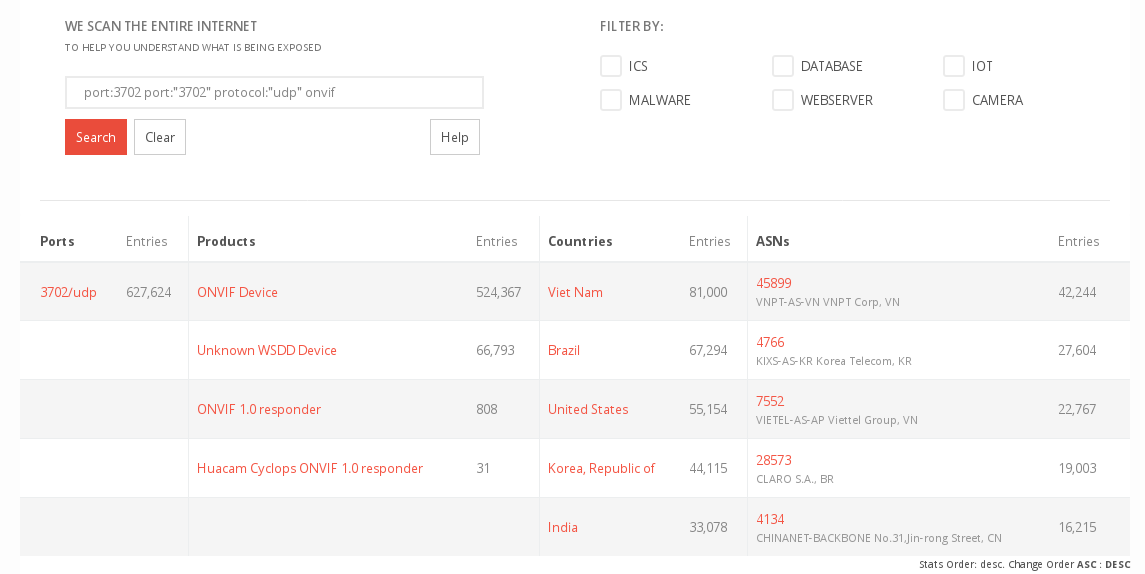
Measuring the Attacksurface
According to a Binaryedge-Search, there are roughly 630.000 IPs online available with SOAP/WS-Discovery services on UDP-protocol, which is a serious amount and can be used for huge attacks.
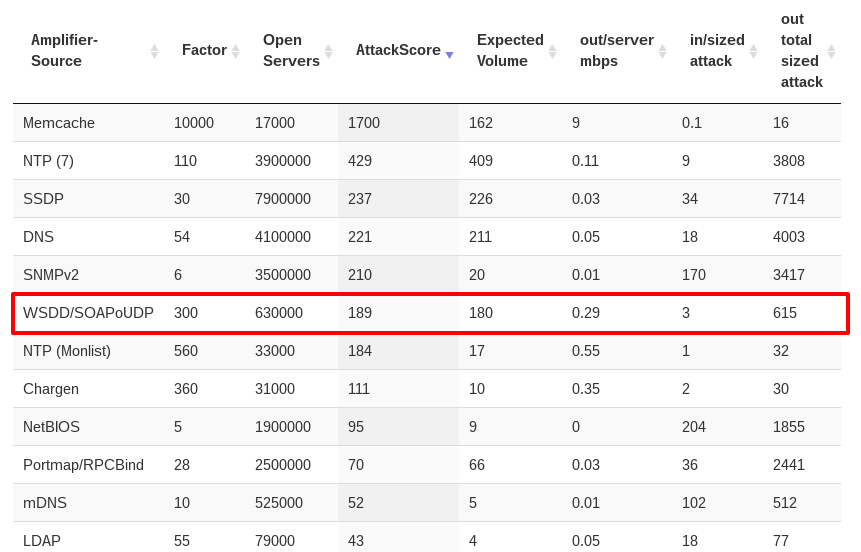
Classification besides other Amplification-Vectors, SRC
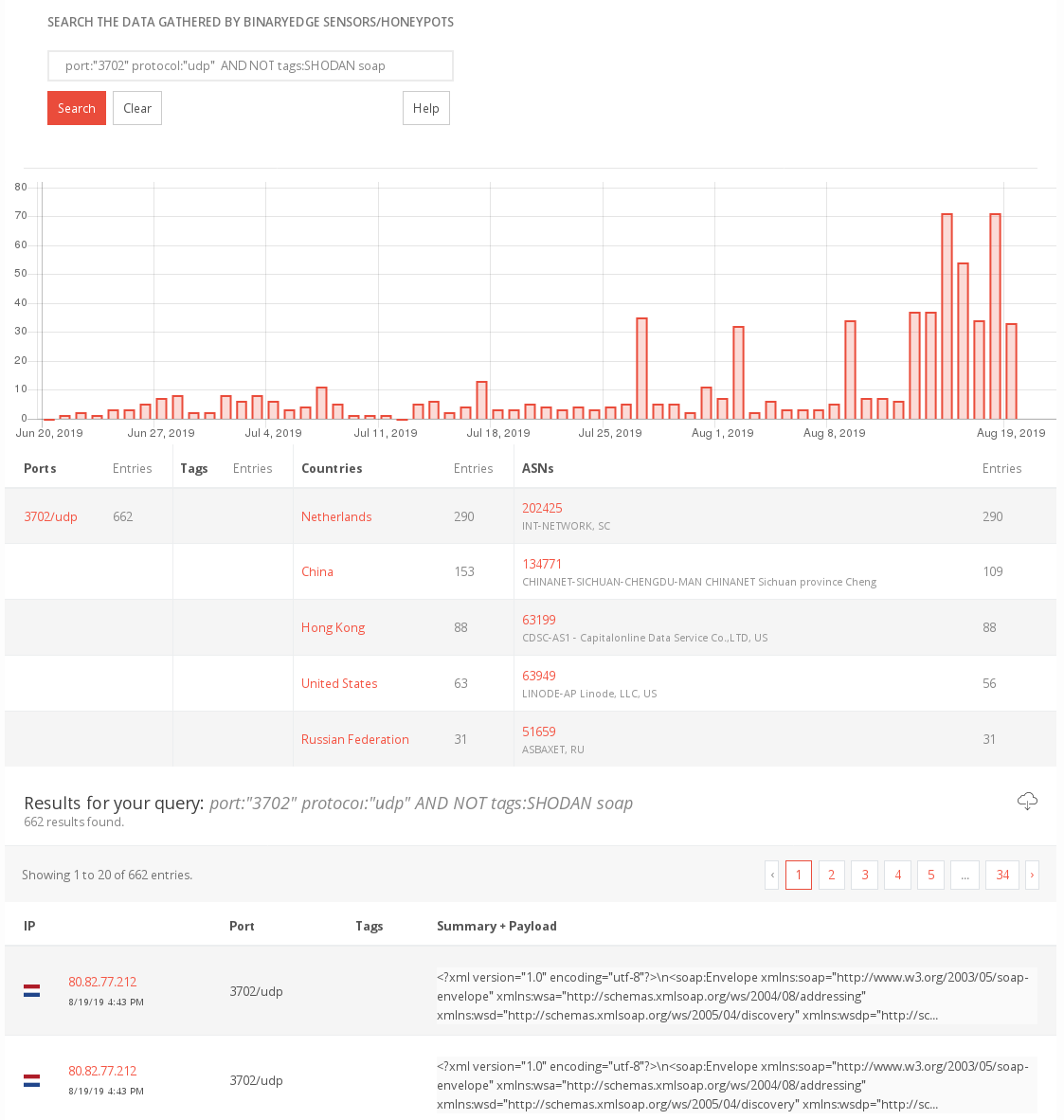
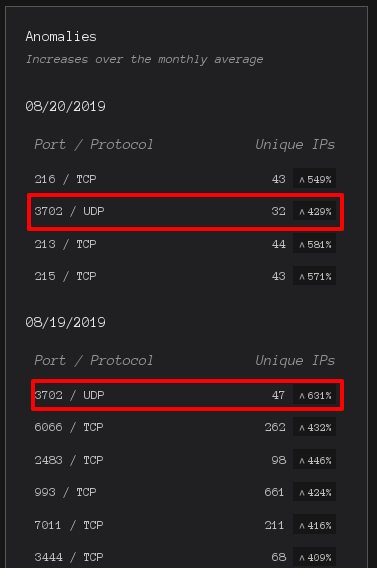
recent scanning-activity
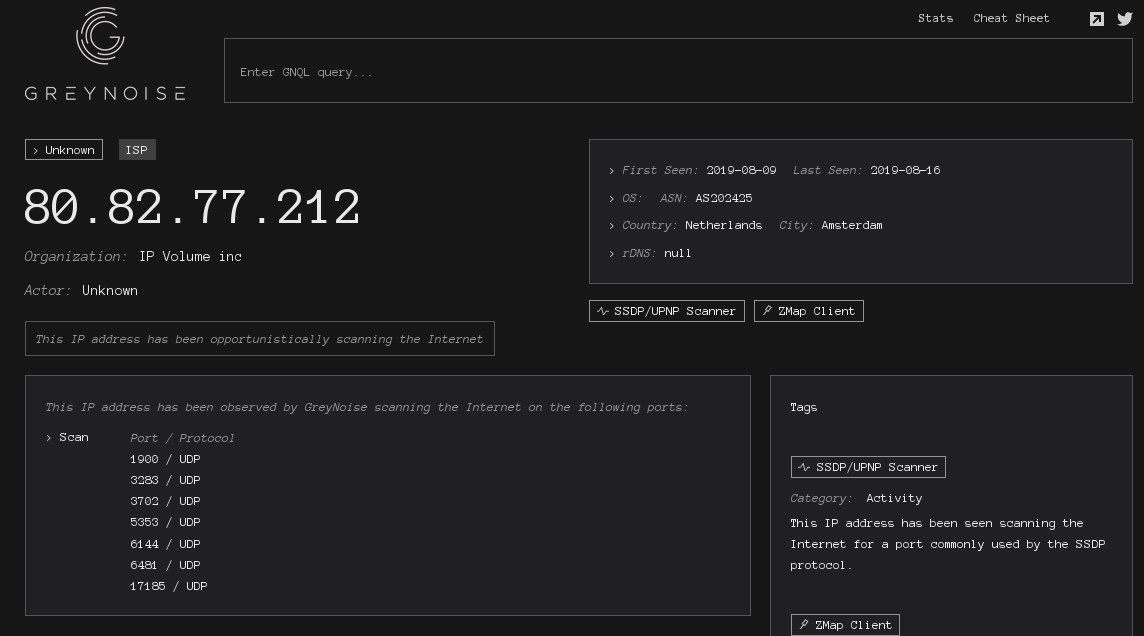
According to sensorsdata from binaryedge, scanning-activity intensified since mid-august. The uptick from 08. August on is dedicated to a single IP from Netherlands, 80.82.77.212, which scans UDP only.
Mitiations
- Src: Tucker Preston / pastebin
Juniper
firewall {
term wsdiscovery-ddos {
from {
protcol udp;
source-port 3702;
}
then policer wsdiscovery;
}
term accept {
then accept;
}
policer wsdiscovery {
if-exceeding {
bandwidth-limit 1024m;
burst-size-limit 256k;
}
then discard;
}
Nokia FP4:
Standard ACL Match (applicable to Juniper Flex Match as well)
Pattern: 0x3c3f786d6c +
Offset (byte) 42
BGP Flowspec (GoBGP)
$ gobgp global rib -a ipv4-flowspec add match protocol udp source-port '==3702' then discard / rate-limit
some stats from the attack
various Statistics from attacking IPs, ASNs and Countries, SRC_PORT 3207 only
SUMMARY
IPs : 4871
Networks : 2125
ASNs : 789
Countries : 89
- ASNs with more than 20 participating IPs
Top ASNs
ASN_NR | Count | ASNName
----------+--------+-----------------------------------
680 | 334 | DFN Verein zur Foerderung eines Deutschen Forschungsnetzes e.V., DE
4134 | 334 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
22394 | 255 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
3462 | 208 | HINET Data Communication Business Group, TW
3215 | 145 | France Telecom - Orange, FR
4837 | 120 | CHINA169-BACKBONE CHINA UNICOM China169 Backbone, CN
7552 | 102 | VIETEL-AS-AP Viettel Group, VN
4782 | 98 | GSNET Data Communication Business Group, TW
852 | 94 | ASN852 - TELUS Communications Inc., CA
3450 | 92 | UTK - University of Tennessee, Knoxville, US
7018 | 91 | ATT-INTERNET4 - AT&T Services, Inc., US
1659 | 87 | ERX-TANET-ASN1 Taiwan Academic Network (TANet) Information Center, TW
45899 | 79 | VNPT-AS-VN VNPT Corp, VN
6830 | 64 | LGI-UPC formerly known as UPC Broadband Holding B.V., AT
5410 | 63 | ASN-BOUYGTEL-ISP, FR
8151 | 61 | Uninet S.A. de C.V., MX
48161 | 58 | NG-AS Sos. Bucuresti - Ploiesti nr. 42-44, RO
9050 | 55 | RTD Bucharest, Romania, RO
8708 | 52 | RCS-RDS 73-75 Dr. Staicovici, RO
7922 | 48 | COMCAST-7922 - Comcast Cable Communications, LLC, US
2701 | 39 | KSU-NET - Kansas State University, US
5617 | 39 | TPNET, PL
2119 | 31 | TELENOR-NEXTEL Telenor Norge AS, NO
217 | 31 | UMN-SYSTEM - University of Minnesota, US
20130 | 30 | DEPAUL - Depaul University, US
4760 | 30 | HKTIMS-AP HKT Limited, HK
17 | 27 | PURDUE - Purdue University, US
3320 | 24 | DTAG Internet service provider operations, DE
1759 | 23 | TSF-IP-CORE Telia Finland Oyj, FI
12400 | 23 | PARTNER-AS, IL
16135 | 23 | TURKCELL-AS Turkcell A.S., TR
137 | 22 | ASGARR Consortium GARR, IT
6327 | 22 | SHAW - Shaw Communications Inc., CA
9416 | 21 | MULTIMEDIA-AS-AP Hoshin Multimedia Center Inc., TW
9304 | 21 | HUTCHISON-AS-AP HGC Global Communications Limited, HK
16086 | 21 | DNA, FI
25513 | 21 | ASN-MGTS-USPD, RU
58224 | 20 | TCI, IR
395421 | 20 | OKSTATE - Oklahoma State University, US
30722 | 20 | VODAFONE-IT-ASN, IT
- Contry-Stats with more than 10 IPs
Top 100 Countries
Country | Count
--------+-----------
US | 1157
CN | 484
TW | 441
DE | 393
CA | 232
FR | 219
VN | 210
RO | 197
BR | 135
RU | 124
MX | 106
PL | 98
SE | 86
HK | 70
GB | 69
CZ | 61
UA | 57
NO | 52
IR | 49
IT | 46
FI | 45
IL | 42
NL | 38
TR | 37
JP | 36
ES | 35
IN | 23
CO | 21
HU | 19
PA | 19
PT | 15
CH | 14
PR | 13
SG | 13
AU | 13
BE | 12
EC | 12
BG | 11
- Networks/CIDRS with more than 10 participating IPs
Top 100 Networks
NW | Count | NetworkName
------------------+--------+-----------------------------------
134.176.0.0/16 | 233 | DFN Verein zur Foerderung eines Deutschen Forschungsnetzes e.V., DE
117.24.0.0/13 | 61 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
117.56.0.0/16 | 54 | GSNET Data Communication Business Group, TW
89.80.0.0/12 | 43 | ASN-BOUYGTEL-ISP, FR
141.99.0.0/16 | 39 | DFN Verein zur Foerderung eines Deutschen Forschungsnetzes e.V., DE
129.130.0.0/16 | 39 | KSU-NET - Kansas State University, US
96.1.0.0/17 | 39 | ASN852 - TELUS Communications Inc., CA
160.36.0.0/18 | 38 | UTK - University of Tennessee, Knoxville, US
140.192.0.0/16 | 30 | DEPAUL - Depaul University, US
166.248.0.0/16 | 26 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
171.208.0.0/12 | 25 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
128.46.0.0/16 | 24 | PURDUE - Purdue University, US
139.6.0.0/16 | 23 | DFN Verein zur Foerderung eines Deutschen Forschungsnetzes e.V., DE
223.200.0.0/16 | 23 | GSNET Data Communication Business Group, TW
140.128.0.0/13 | 21 | ERX-TANET-ASN1 Taiwan Academic Network (TANet) Information Center, TW
139.78.0.0/16 | 20 | OKSTATE - Oklahoma State University, US
166.154.0.0/16 | 20 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
140.112.0.0/12 | 19 | ERX-TANET-ASN1 Taiwan Academic Network (TANet) Information Center, TW
166.141.0.0/17 | 19 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
46.214.208.0/21 | 19 | NG-AS Sos. Bucuresti - Ploiesti nr. 42-44, RO
2.55.0.0/17 | 19 | PARTNER-AS, IL
37.203.128.0/18 | 18 | CABLECOM-AS, GB
116.52.0.0/14 | 18 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
82.76.0.0/14 | 18 | RCS-RDS 73-75 Dr. Staicovici, RO
82.127.0.0/16 | 18 | France Telecom - Orange, FR
96.47.64.0/20 | 17 | NYINTERNET - NYI, US
160.36.128.0/18 | 17 | UTK - University of Tennessee, Knoxville, US
59.49.0.0/17 | 17 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
173.182.0.0/19 | 16 | ASN852 - TELUS Communications Inc., CA
60.168.0.0/13 | 16 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
12.128.0.0/9 | 16 | ATT-INTERNET4 - AT&T Services, Inc., US
160.36.64.0/18 | 16 | UTK - University of Tennessee, Knoxville, US
160.36.192.0/18 | 16 | UTK - University of Tennessee, Knoxville, US
176.128.0.0/10 | 15 | ASN-BOUYGTEL-ISP, FR
125.227.0.0/16 | 15 | HINET Data Communication Business Group, TW
112.112.0.0/14 | 15 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
166.164.0.0/16 | 15 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
87.92.0.0/14 | 14 | DNA, FI
163.24.0.0/14 | 14 | ERX-TANET-ASN1 Taiwan Academic Network (TANet) Information Center, TW
180.96.0.0/11 | 14 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
166.148.64.0/18 | 14 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
94.53.139.0/24 | 14 | NG-AS Sos. Bucuresti - Ploiesti nr. 42-44, RO
143.107.0.0/16 | 13 | UNIVERSIDADE DE SAO PAULO, BR
166.251.0.0/16 | 13 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
61.219.0.0/16 | 12 | HINET Data Communication Business Group, TW
80.48.0.0/13 | 12 | TPNET, PL
60.249.0.0/16 | 12 | HINET Data Communication Business Group, TW
96.64.0.0/11 | 12 | COMCAST-7922 - Comcast Cable Communications, LLC, US
166.255.0.0/17 | 12 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
166.155.0.0/16 | 11 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
166.166.0.0/16 | 11 | CELLCO - Cellco Partnership DBA Verizon Wireless, US
163.29.0.0/16 | 11 | GSNET Data Communication Business Group, TW
130.15.0.0/16 | 11 | QUEENSU-KINGSTON - Queen_s University, CA
27.152.0.0/13 | 11 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
92.87.0.0/16 | 10 | RTD Bucharest, Romania, RO
80.11.0.0/16 | 10 | France Telecom - Orange, FR
160.94.0.0/16 | 10 | UMN-SYSTEM - University of Minnesota, US
66.166.120.0/21 | 10 | MEGAPATH5-US - MegaPath Corporation, US
147.188.0.0/16 | 10 | JANET Jisc Services Limited, GB
128.8.0.0/16 | 10 | UMDNET - University of Maryland, US
81.128.0.0/12 | 10 | BT-UK-AS BTnet UK Regional network, GB
68.182.0.0/18 | 10 | TELUS-3 - TELUS Communications Inc., CA
221.208.0.0/14 | 10 | CHINA169-BACKBONE CHINA UNICOM China169 Backbone, CN
216.173.128.0/20 | 10 | CZIO-ASN - Cruzio, US
85.133.130.0/24 | 10 | IR-SEPANTA-ISP, IR
86.120.0.0/13 | 10 | RCS-RDS 73-75 Dr. Staicovici, RO
36.4.0.0/14 | 10 | CHINANET-BACKBONE No.31,Jin-rong Street, CN
References
Fragen? Kontakt: info@zero.bs
