tl;dr
GCP-Loadbalancer-Setup can protect you successfully from volumetrics TCP - DDoS - attacks, if HTTP/S or SSLProxy-Loadbalancers are used.
Intro
Recently we were asked to perform a DDoS-Test for a client who had some issues with their GCP-Loadbalancer-Setup during attacks and and asked us to test both their original (Setup A) and the changes (Setup B).
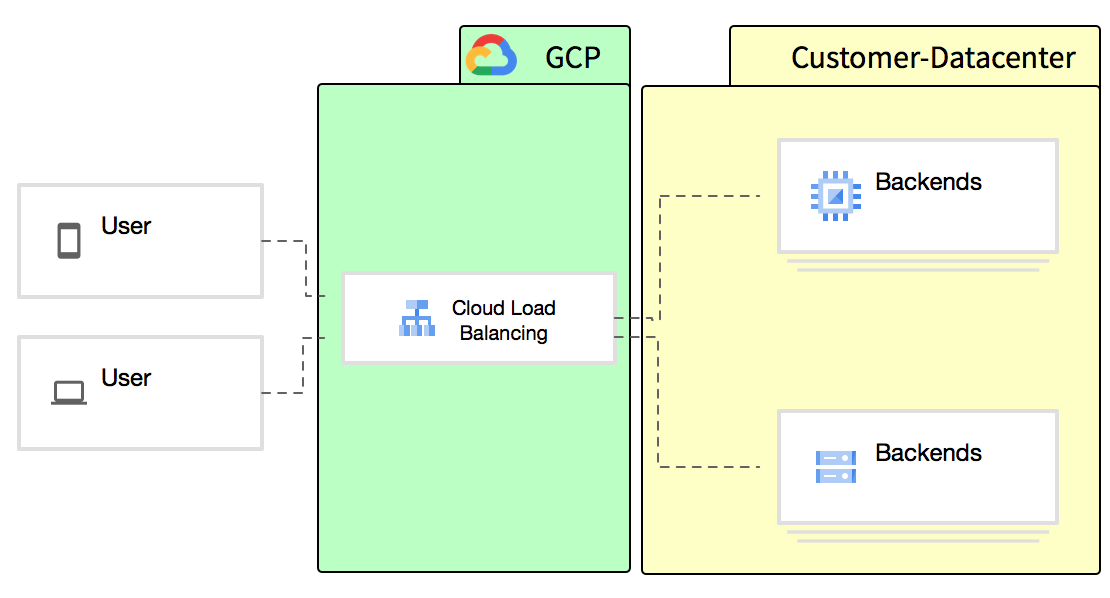
The uplink to the backends has a capacity of 10 GB / s.
The only difference: in Setup A the TCP Loadbalancer was used, while in Setup B the HTTP/S Loadbalancer was used.
Testseries B
Setup B was tested first (HTTP/S Loadbalancer) to verify that the modified setup successfully protects against TCP volume attacks.
We tried different TCP attack patterns against the open port 443, which can also be found in ITW, and turned up the traffic to 20 GB/s in total. At the same time, we measured on one of the backends whether TCP packets arrived or not.
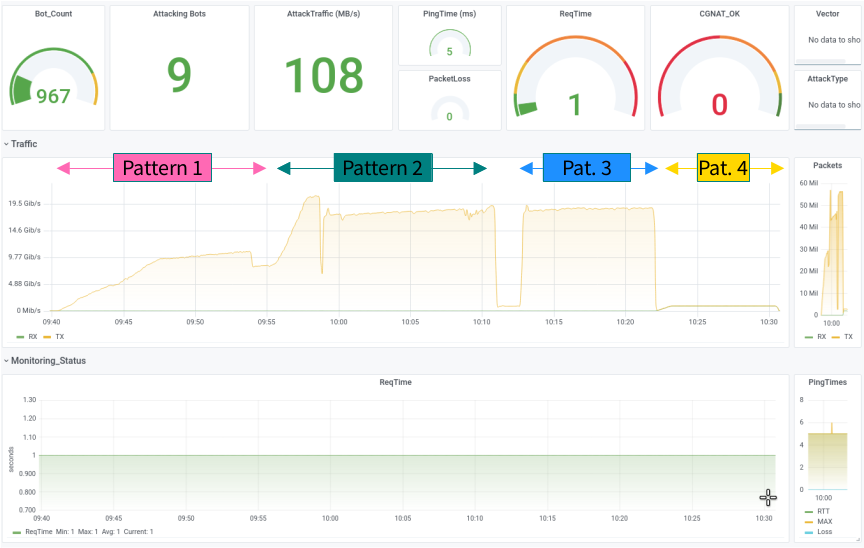
During the entire time of the attacks, no malicious packets arrived at the backends, no matter which attack pattern we tried; the customer had given us a completely free hand here, and we naturally selected the somewhat more sophisticated pattern from our platform.
So for Testseries B, we could see that the setup changes were successful and protected well against volumetric TCP-DDoS-attacks.
Testseries A
Setup A (TCP Loadbalancer) showed a different picture: here we were able to find a reproducible attack vector (TCP Chewy/TCP Garbage) that caused the backends to stumble and denied access to the application after a short while.
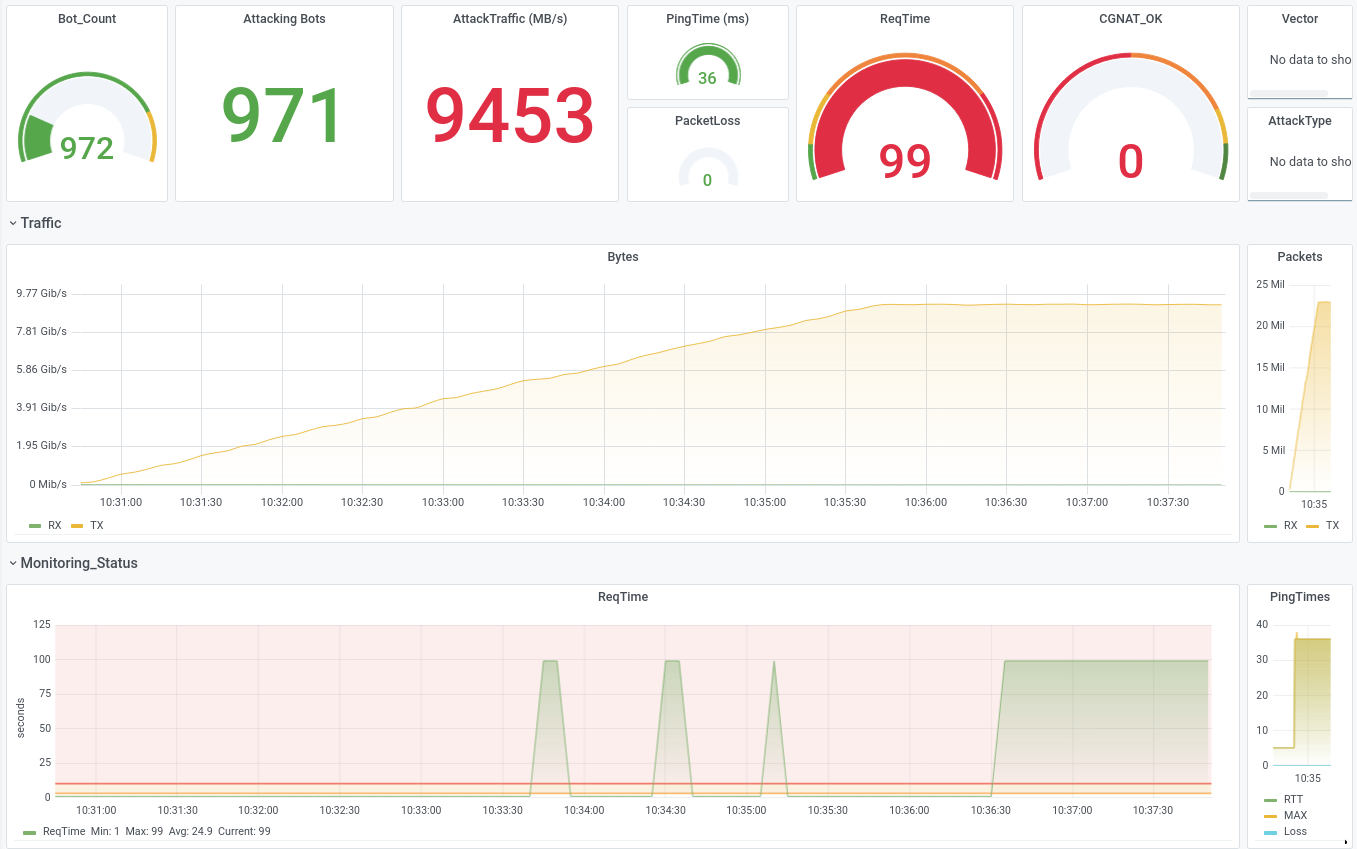
The team's original assumption that the use of TCP-LBs does not reliably protect against all from all DDoS attacks could thus be confirmed.
Conclusion
-
using HTTP(S)LoadBalancing or SSLProxy-LoadBalancing mitigates and absorbs many Layer4 and below attacks, such as SYN floods, IP fragment floods, port exhaustion, etc.
-
use the TCP-LoadBalancer only if you need to, and apply additional Anti-DDoS-Measures
-
The Google - Guide Best Practices for DDoS Protection and Mitigationon Google Cloud Platform might be studied additionally
more Details on our DDoS-Stresstest-Plattform: click here
Fragen? Kontakt: info@zero.bs
