{% .img-responsive %}
Regarding the latest [Confluence-RCE-Vuln](https://confluence.atlassian.com/doc/confluence-security-advisory-2019-03-20-966660264.html)
from late March we've seen the first wildly used [Exploit/POC](https://github.com/Yt1g3r/CVE-2019-3396_EXP/commit/36ba5d2213539caa19ae33736d2f43845ab3f309)
released on Apr 10. at 02.30 UTC.
We did a forensic-job recently on exactly that issue and were able to obtain some
access-logs from exploited machines (see below)
We see successfull usage of that exploitcode from botnets at around 7.30 UTC, so roughly 5hours
later. (kerberods/Miner-Bots were installed; we'll do a writeup on that forensics later).
5 hours from POC to Mass-Exploitation, **THAT is quick.**
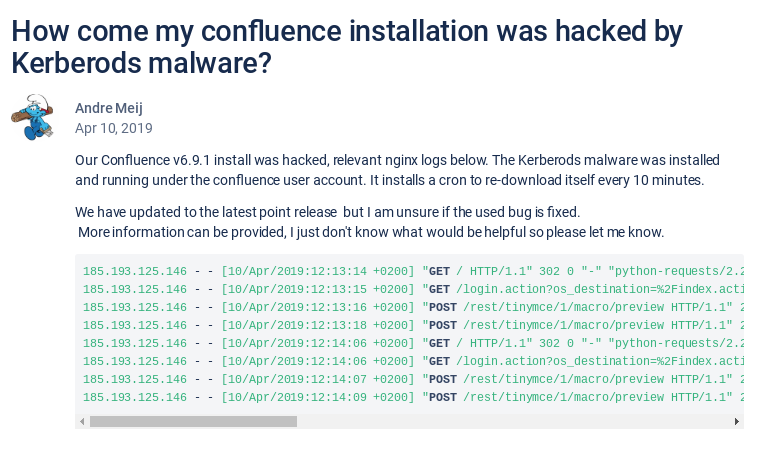
Exploitation-Extract from access.log
27.102.129.88 - - [10/Apr/2019:09:25:35 +0200] "POST /rest/tinymce/1/macro/preview HTTP/1.1" 200 3680 "https://xxxploit.me/pages/resumedraft.action?draftId=12345&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&" "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0" "-"
45.32.45.82 - - [10/Apr/2019:09:44:22 +0200] "POST /rest/tinymce/1/macro/preview HTTP/1.1" 200 3445 "https://xxxploit.me/pages/resumedraft.action?draftId=12345&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&" "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0" "-"
45.32.45.82 - - [10/Apr/2019:09:44:21 +0200] "POST /rest/tinymce/1/macro/preview HTTP/1.1" 200 3680 "https://xxxploit.me/pages/resumedraft.action?draftId=12345&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&" "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0" "-"
45.32.45.82 - - [10/Apr/2019:09:44:19 +0200] "POST /rest/tinymce/1/macro/preview HTTP/1.1" 200 3680 "https://xxxploit.me/pages/resumedraft.action?draftId=12345&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&" "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0" "-"
185.193.125.146 - - [10/Apr/2019:12:00:20 +0200] "POST /rest/tinymce/1/macro/preview HTTP/1.1" 200 3680 "https://xxxploit.me/pages/resumedraft.action?draftId=12345&draftShareId=056b55bc-fc4a-487b-b1e1-8f673f280c23&" "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0" "-"
The timestamp is confirmed by a blogpost:How come my confluence installation was hacked by Kerberods malware? :
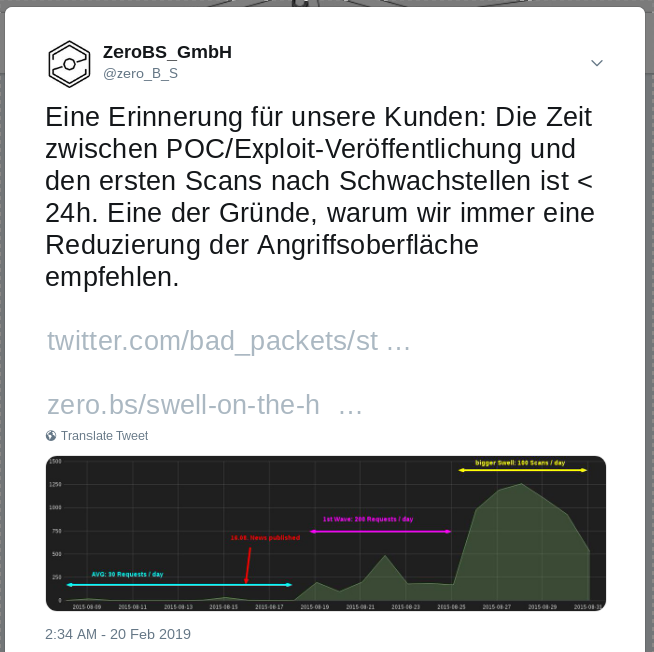
What amazes us: we track the TTE (Time To Exploit) since we started using honeypots for botnet-tracking around 10 years ago, and got used to a TTE from around 24hrs since Mirai, we even confirmed that recently with @BadPackets:
Fragen? Kontakt: info@zero.bs